Creating randomly populated groups with azure AD dynamic groups
The purpose of the blog post is to inform you how to create randomly populated groups with Azure AD.
As I already mention in my blog post about Update rings, I want to deploy the Windows updates in different rings.
As my roll-out strategy for the update rings, I also want to roll out my configuration changes.
Requirements:
First I want to explain a little bit about the Azure AD Group features and then I will show you how I create randomly populated dynamic groups. E.G. Within Microsoft Endpoint Manager you create the configuration profile and to ensure that these configurations will be applied on the device you have to assign it to a group.
Azure AD groups types
Within the Microsoft Cloud, you have multiple group types available (see below list).
- Distribution Group
- Microsoft 365 Group
- Static group
- Dynamic User Group
- Dynamic Device Group
In this blog post, I will focus on Azure AD Dynamic user and device groups, but first I want to give some background information what Azure AD User and Device groups are and how and when each one can be used.
User groups vs. device groups assignment
Many users ask when to use user groups and when to use device groups.
The answer depends on your goal. Here’s some guidance to get you started.
Device groups
Use device groups when you don’t care who’s signed in on the device, or if anyone is signed in.
You want your settings to always be on the device.
User groups
Use user groups when you want your settings and rules to always go with the user, whatever device they use.
Source: Link to official Microsoft documentation about the assignment of user vs device groups
If you want more information about when to use users or device groups check out the following blog by Kenneth van surksum
Azure Dynamic Groups Membership
In Azure Active Directory (Azure AD), you can use rules to determine group membership based on user or device properties. Dynamic membership is supported for security groups and Microsoft 365 Groups. When a group membership rule is applied, user and device attributes are evaluated for matches with the membership rule. When an attribute changes for a user or device, all dynamic group rules in the organization are processed for membership changes. Users and devices are added or removed if they meet the conditions for a group.
Note. Dynamic groups require an Azure AD Premium P1 license for each unique user that is a member of one or more dynamic groups. You don’t have to assign licenses to users for them to be members of dynamic groups, but you must have the minimum number of licenses in the Azure AD organization to cover all such users. There is no license required for Azure Dynamic device groups.
However, the functionality works, but you do not meet Microsoft’s licensing terms.
Source: Link to official Microsoft documentation about Creating a dynamic group
Which dynamic group property should I use?
To create a randomly populated group I dig into an Azure Ad object and search for an attribute that I can use for the dynamic rule. There are a few properties available to use in the group. Click here to see all available properties. I decided to use the “objectId” property because for both group types I can use the objectId property and the property is based on hexadecimal.
What is hexadecimal
Hexadecimal numerals are widely used by computer system designers and programmers because they provide a human-friendly representation of binary-coded values. Each hexadecimal digit represents four bits (binary digits), also known as a nibble.
Hexadecimal uses 16 distinct symbols, the symbols “0”–”9″ and “A”–”F” which represent values from 10 to 15.
Source: Link to Wikipedia about Hexadecimal
I decided to use 4 dynamic groups in my roll-out strategy, so I have to create a dynamic syntax rule with 4 symbols.
Note. I have used in my syntax “012A”, but you are free to use other symbols like “ABCD” or “01”.
Creating Azure AD dynamic groups via Microsoft Endpoint Manager
- Open Microsoft endpoint manager
- In the menu select Groups
- Under Groups, select All groups
- Click on New group
Or use the following link New Group – Microsoft Endpoint Manager admin center - Set the following settings
| Setting | Value |
|---|---|
| Group type | Security |
| Group Name | E.g. User group 1 |
| Group Description | Set a good description, so that everyone with access to the portal knows the purpose of the group |
| Azure AD roles can be assigned to the group | Yes/No |
| Membership type | Dynamic User / Dynamic Device |
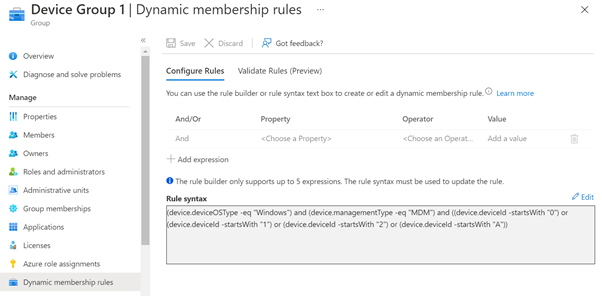
- Click on Add dynamic query after setting the correct group settings
- Click on the Edit button at the right side of Rule Syntax
- Add below rule syntaxes
- Click on Save, and create the other groups
Device Group
| Group name | Dynamic Rule syntax |
|---|---|
| Device group 1 | (device.deviceOSType -eq “Windows”) and (device.managementType -eq “MDM”) and ((device.deviceId -startsWith “0”) or (device.deviceId -startsWith “1”) or (device.deviceId -startsWith “2”) or (device.deviceId -startsWith “A”)) |
| Device group 2 | (device.deviceOSType -eq “Windows”) and (device.managementType -eq “MDM”) and ((device.deviceId -startsWith “3”) or (device.deviceId -startsWith “4”) or (device.deviceId -startsWith “5”) or (device.deviceId -startsWith “B”)) |
| Device group 3 | (device.deviceOSType -eq “Windows”) and (device.managementType -eq “MDM”) and ((device.deviceId -startsWith “6”) or (device.deviceId -startsWith “7”) or (device.deviceId -startsWith “8”) or (device.deviceId -startsWith “C”)) |
| Device group 4 | (device.deviceOSType -eq “Windows”) and (device.managementType -eq “MDM”) and ((device.deviceId -startsWith “9”) or (device.deviceId -startsWith “D”) or (device.deviceId -startsWith “E”) or (device.deviceId -startsWith “F”)) |
User groups
| Group name | Dynamic Rule syntax |
|---|---|
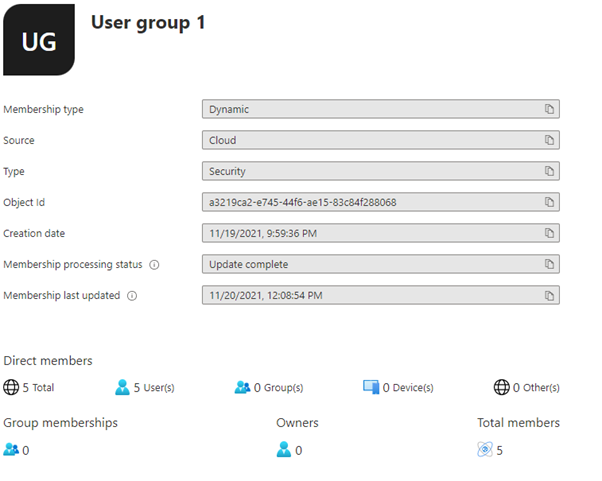
| User group 1 | (user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”)) and ((user.objectId -startsWith “A”) or (user.objectId -startsWith “1”) or (user.objectId -startsWith “2”) or (user.objectId -startsWith “3”)) |
| User group 2 | (user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”)) and ((user.objectId -startsWith “b”) or (user.objectId -startsWith “3”) or (user.objectId -startsWith “4”) or (user.objectId -startsWith “5”)) |
| User group 3 | (user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”)) and ((user.objectId -startsWith “c”) or (user.objectId -startsWith “6”) or (user.objectId -startsWith “7”) or (user.objectId -startsWith “8”)) |
| User group 4 | (user.assignedPlans -any (assignedPlan.servicePlanId -eq “41781fb2-bc02-4b7c-bd55-b576c07bb09d” -and assignedPlan.capabilityStatus -eq “Enabled”)) and ((user.objectId -startsWith “9”) or (user.objectId -startsWith “d”) or (user.objectId -startsWith “e”) or (user.objectId -startsWith “f”)) |
At first I struggled somewhat with the creating of the user group syntax, because Azure AD creates a “normal user object” for e.g. shared mailboxes. I don’t want pollution in my groups, but Thijs Lecomte (MVP) has written a blog post to create a dynamic group with all AAD premium licensed users. I could use his logic to get only licensed users and combine that with the ObjectId to get only users object and not other types objects like shared mailbox for example.
Results:
Validation of an Azure Dynamic Group (preview)
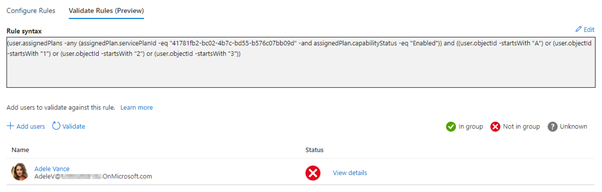
During the creation of a dynamic rule syntax, there is an option to validate your dynamic rule against selected group members to confirm if the rule is working. This helps evaluate whether user or device meets the rule criteria and aid in troubleshooting when membership is not expected. The biggest advantage of the validation option is that you don’t have to save the group to know if your rule is working as expected and you don’t have to wait for the dynamic rule to be processed to know if the correct members will be included.
Results:
Note. Validate Rules is still in public preview, but fully supported by Microsoft.
References
- Hexadecimal
- Creating a dynamic group with all AAD Premium licensed users
- Create or update a dynamic group in Azure Active Directory
- Assign user and device profiles in Microsoft Intune
- Rules for dynamically populated groups membership – Azure AD | Microsoft Docs
- Validate rules for dynamic group membership (preview) – Azure AD | Microsoft Docs





Have multiple assigned update rings and a dynamic (catch-all) group, but this is causing conflicts with deploying quality updates to the assigned groups.
We have a total of 10 update rings including a QA and Pilot group. Pilot and QA do not get conflicts.
Hi Marc,
How did you assigned the update policy? and what is the dynamic query of your AAD Groups that you are using for the assignment?
Hi,
Thanks a lot for this.
I need to create groups of devices based on users attributes. ie I want to create a group of devices for all HR users, another one for all Sales Users.
How can we achieve this?
BR,
Frederic.
Hi Frederic,
I have done something similar in the following blog post.
https://endpointcave.com/create-a-dynamic-device-group-for-all-dem-user-enrolled-devices/
Let me know if this is sufficient enough or I can figure it out and write a blog post if you want.
Kind regards,
René
This is really helpfull, Thnx for sharing