Update like a boss with Intune in an Enterprise Environment
The purpose of the blog post is to inform you how to rollout updates in an enterprise environment with Intune. What is Windows update for Business, share my update strategy, how to configure that strategy in the Intune/Endpoint manager portal and how to assign these update rings, and what are the next steps after configuring the update rings.
Today’s world security is more important than ever and staying up to date plays a key role in keeping a secure environment. Windows Update for Business is a service that can be configure within Intune to make sure your updates are installed. Windows update for Business automatically deploys Windows updates, feature updates and driver updates to your devices without the need of manually approving the updates as in the past with WSUS.
Note. In this particular blog post, I’m only going to use Update Rings for Windows 10 and later.
Requirements:
What is Windows For Business?
Windows Update for Business enables IT administrators, to keep the Windows client devices in their organization up to date with the latest security defenses and Windows features, by directly connecting these systems to the Windows Update service. You can use Group Policy or Mobile Device Management (MDM) solutions such as Microsoft Intune to configure the Windows Update for Business settings that control how and when devices are updated.
Specifically, Windows Update for Business lets you control update offerings and experiences to allow for reliability and performance testing on a subset of devices before deploying updates across the organization. It also provides a positive update experience for people in your organization because the Pilot users knows that they are pilot and they will be the first group that receive all the updates and features but that it can also cause problems. The non pilot users know that they only receive updates that are tested and do not cause any problems.
Let’s start by taking a look in the Intune Portal. I will open the Update for Business blade.
There are different types of updates. I will highlight two of the available update options:
- Quality updates
Quality updates are traditional operating system updates, typically released on the second Tuesday of each month (though they can be released at any time). These include security, critical, and driver updates.
- Feature updates (Windows 10 20H1/20H2/21H1)
Previously referred to as “upgrades”, feature updates contain not only security and quality revisions but also significant feature additions and changes. Feature updates are released as soon as they become available.
Source: Link to official Microsoft Documentation about Windows Update for Business
Our Update Strategy
The most important thing for a successful side story is to come up with a good strategy. An enterprise environment will have a different strategy than an environment with 10 devices.
For an Enterprise environment, I always use the following strategy as a baseline and finetune it on the customer’s requirements. I use this strategy for the following reasons
- Updates will be installed within two weeks
- Updates are tested before starting rollout to the end-users
- When an update causes a problem then the update ring can become paused
- Minimum business impact
- Set and forget thought because the Azure Dynamic Device/User Groups
- It is a scalable solution
Update Strategy:
- Grace period between the different rings;
- Update channel;
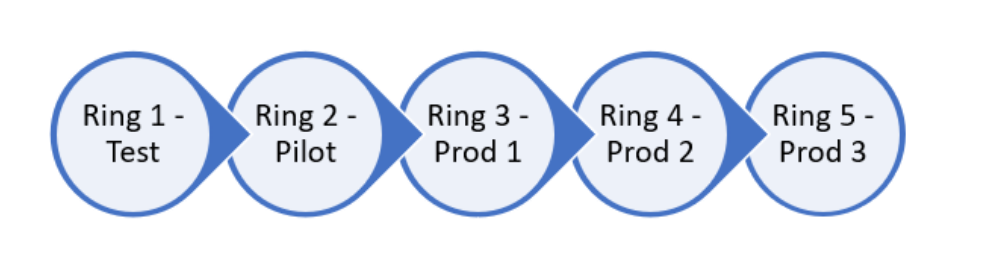
- 5 Update rings;
- Test, a few IT people only
- Pilot, Few people of different departments and levels, so the pilot represent the entire enterprise environment
- 3 Production rings
Creating Windows 10 update Rings
- Open Microsoft endpoint manager
- In the menu selecht Devices
- Under Devices, select Windows and select Windows 10 update rings
Or use the following link Update ring for Windows 10 and later – Microsoft Endpoint Manager admin center - Click on Create Profile
- Provide a policy name, I use the following name “Update Ring XX ”
- Set a description, so that everyone with access to the portal knows the purpose of the update ring
- Click on Next and configure the update ring settings
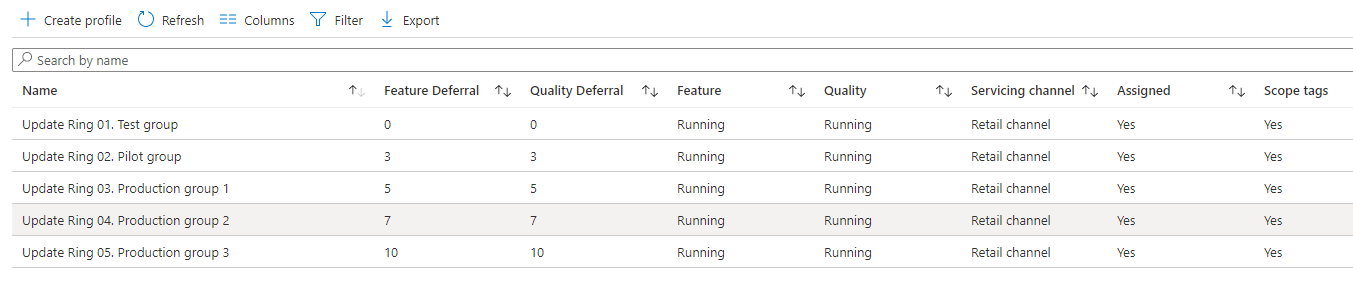
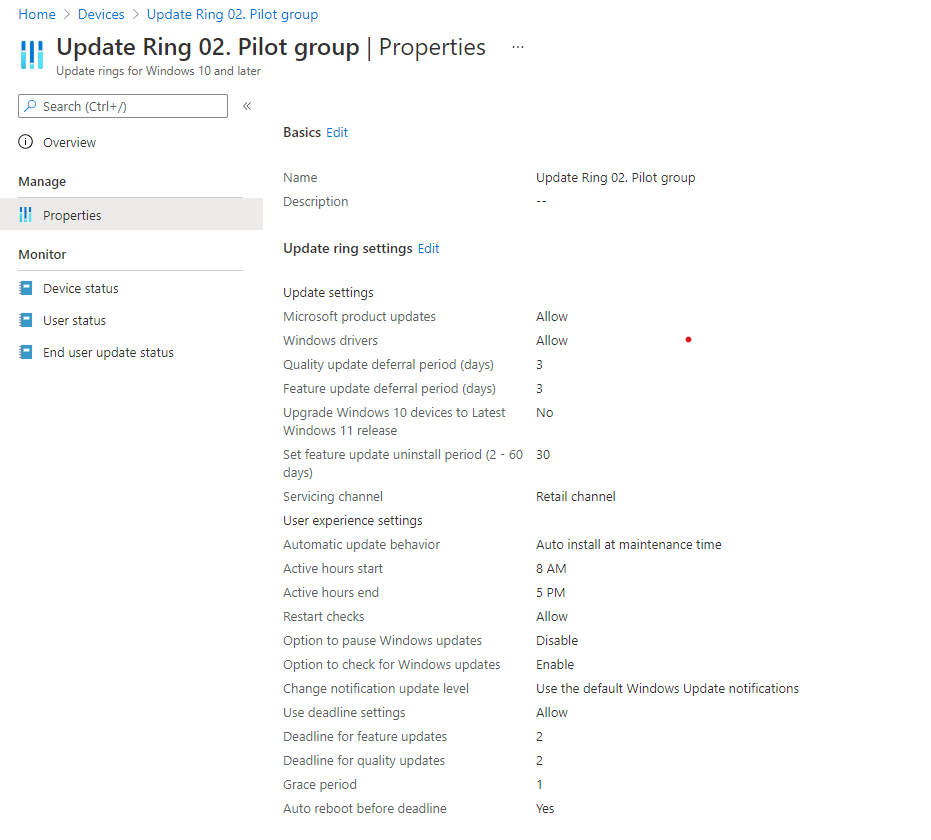
Update settings
| Setting name | Test | Pilot | Production 1 | Production 2 | Production 3 |
|---|---|---|---|---|---|
| Microsoft product updates | Allow | Allow | Allow | Allow | Allow |
| Windows drivers | Allow | Allow | Allow | Allow | Allow |
| Quality update deferral period (days) | 0 | 3 | 5 | 7 | 10 |
| Feature update deferral period (days) | 0 | 3 | 5 | 7 | 10 |
| Upgrade Windows 10 devices to Latest Windows 11 release | No | No | No | No | No |
| Set feature update uninstall period (2 – 60 days) | 30 | 30 | 30 | 30 | 30 |
| Enable pre-release builds | Not Configured | Not Configured | Not Configured | Not Configured | Not Configured |
User Experience settings
| Setting name | Test | Pilot | Production 1 | Production 2 | Production 3 |
|---|---|---|---|---|---|
| Automatic update behavior | Auto install at maintenance time | Auto install at maintenance time | Auto install at maintenance time | Auto install at maintenance time | Auto install at maintenance time |
| Active hours start | 8 AM | 8 AM | 8 AM | 8 AM | 8 AM |
| Active hours end | 5 PM | 5 PM | 5 PM | 5 PM | 5 PM |
| Restart checks | Allow | Allow | Allow | Allow | Allow |
| Option to pause Windows updates | Disable | Disable | Disable | Disable | Disable |
| Option to check for Windows updates | Enable | Enable | Enable | Enable | Enable |
| Change notification update level | Use the default Windows Update notifications | Use the default Windows Update notifications | Use the default Windows Update notifications | Use the default Windows Update notifications | Use the default Windows Update notifications |
Deadline settings
| Setting name | Test | Pilot | Production 1 | Production 2 | Production 3 |
|---|---|---|---|---|---|
| Use deadline settings | Allow | Allow | Allow | Allow | Allow |
| Deadline for feature updates | 2 | 2 | 2 | 2 | 2 |
| Deadline for quality updates | 2 | 2 | 2 | 2 | 2 |
| Grace period | 1 | 1 | 1 | 1 | 1 |
| Auto reboot before deadline | yes | yes | yes | yes | yes |
Results:
Assignment Windows 10 Update ring to a group
After the creation of the update rings, I have to assign the update ring to a group otherwise they will not be applied to any device or user. For users/devices that are part of the test and pilot, I usually use static groups.
For the test group I normally use the IT Admin devices or the IT admins, so they can test the update before it will be applied to the pilot users. For the pilot group, you could (in my opinion, you need to) include users or devices from other departments. For the other (production) devices/users, I will use automatically populated device/user groups.
Check out this blog post on how these automatically populated groups are built up.
Note. When you decide to assign the update rings to a device group, the end user have to login twice during an AutoPilot Enrollement. Because of having the update ring assigned to a Device group, will results that the device go trough the update checks during the enrollment, and if any update requires a reboot, then you will be prompted for a second login due the the user credentials being revoked when the device reboots, when the enrollment resumes you are prompt to Authenticate again to connect back to Azure/ Intune to continue the remaining steps of the enrollment.
End-user experience
That’s all, the update rings are configured and assigned to the device groups. Let’s check the end-user Experience on a Windows 10 device.
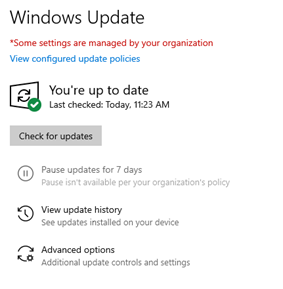
Windows Settings -> Update & Security -> Windows update
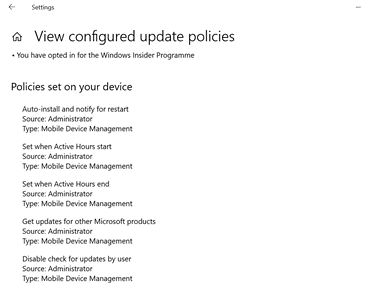
Windows Settings -> Update & Security -> Windows update -> View configured update policies
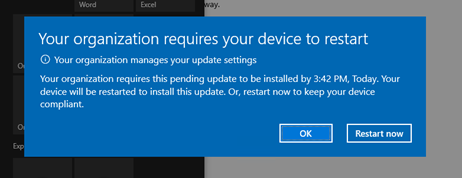
Deadline notification pop-up
Next steps
- Set up delivery optimization
Set up Delivery Optimization – Windows Deployment | Microsoft Docs - Configure reporting
Use Update Compliance reports for Windows Updates in Microsoft Intune – Microsoft Intune | Microsoft Docs



Hi René,
This blog helps us a lot in configuring the updates ring and gives us a good validation of what we did so far. We are only struggling with the right configuration to migrate about 1500 devices (azure and hybrid joined) from w10 to w11 with the least user impact as possible. Do you have some configuration tips and tricks?
Your help would definitely be appreciated!!
Thanks for this post, it has helped me devise a sensible strategy in a very short timeframe.
Question: Do your dynamic groups include exclusions for the Test and Pilot groups?
Yes, correct I have excluded the test en pilot groups from the PROD policies
Hi Rene,
I hope you can help me! I pushed Windows 11 to 900 devices. Because of the other updates pushed before Windows 11, the number is increasing very slowly, and we have to trigger the downland and installation process manually. Can you check my deployment configuration and let me know what the problem is? I appreciate any help you can provide.
Update ring: Auto install and restart at maintenance time, Every Week, Any Day, After 4 pm, Option to pause Windows updates: disable, Option to check for Windows updates: enable, Deadline for feature updates:5, Deadline for quality updates:5, Grace period:2, Auto reboot before deadline: No Feature update deployment: Make update available gradually, First group availability: 10/11/2023 Final group availability:11/13/2023 Days between groups:1
Thank you Rene for this post. I have same configuration as you but I’m not sure to understand the user’s experience.
For example:
When my laptop is locked at night and the quality update is available (after deferral days), I expect my laptop to install and reboot outside of Active hours (8am-5pm) because of the Automatic update behavior (even if the deadline is not yet reached).
It does install when it’s locked but it never reboot, it will only prompt for reboot after I log in (same notification window as you).
Is my expectation wrong?
Hi John,
I assume your expectation is wrong. To be sure, if your device is locked will it go into sleep mode?
Otherwise, I can imagine that when a device is locked it is not allowed to reboot until the user is logged in due to data loss.
Many Thanks René.
How you create groups for this updates rings? For devices or users?
Dynamically groups when new computers or users is add on company?
I’m searching for something dynamically but what difference for users or devices?
Thanks again.
Hi, I have added a link to link to a blog post to create the dynamic groups. I’ve use the Objectid to get it dynamic. This is based on hexadecimal. The difference between user and device can be found in de Microsoft documentation.
Kind regards,
Rene
You mention different grace periods for each ring, but then your table shows grace period of 1 day for all of them. Is that intentional? Or I guess…does the 1 day stack atop of the deferral period?
Hi Fo, I have mention that you have to set grace period between the different rings, In my case/configuration, this have been set with the deferral period. so in my case it is correct that the grace period in the deadline settings is set to 1. I want that the update are installed within 3 days after that the update pops up on a device. But keep in mind this is what is prefer and you can create your own configuration.
How it works is that the update will be deferred for e.g., 3 days (Ring 1), after 3 days the update become available on the device, because of the deadline settings the user needs to install the update within 2 days but in case of a weekend for example, The user has 1 day extra, on top of the 2 days (grace period) before the device will be enforced to install the update and be restarted
I hope that it is now clear for you.
Hi Rene,
Thanks for this! Do I need to configure a quality update policy too? Right now I just have a feature update policy for 22H2. It doesn’t look like it is required, but figured I’d ask.
Hi Steve,
It is not required to configure quality updates. you can use the quality update rings to install a specific update etc and speed up the update process.
More information can be found here: https://learn.microsoft.com/en-us/mem/intune/protect/windows-10-expedite-updates
Thank you! So it looks like that would be only for expediting something, but the quality updates would still be covered by the monthly update policies covered by the update rings.
that’s correct
Hi, tks for tips, one question is better to set groups with devices or with users to set on the rings?
Best Regards
Paulo
Hi Paulo,
It depends,
I prefer to use device groups for update rings when a few colleagues in your organization have multiple devices (Like pilot and PRD) so the devices can be part of different rings. If you don’t have colleagues with multiple devices I prefer to use users groups because I prefer user groups to use, but this is my personal opinion.
Kind regards,
Rene
Hi Rene, Thanks for article, In End-user experience, check for update does not happening automatically and have to do it manually (click check for update). currently automatic update is turn off by GPO do I have to enable that? any suggestion please.
Hi Shams,
Do you have a hybrid join machine and managed by GPO and Intune or Intune managed only?
Kind regards,
Rene
The last step when you view configured update policies, I see no policies for a computer I setup in Intune. It shows “no policies have been configured yet”.
What could be causing that? The Deployment status says its succeeded.
Thanks.
Hi Rick, I am happy to help but I am not 100% sure what do you mean, can you explain a little bit more
Hi René, we have the same issue in our environment as Rick mentioned, but only on Windows 11. Windows 10 machines enrolled to Intune show in Windows Update, that the MDM policy is configured, however after upgrading to Windows 11, Windows Update says “No policies have been configured yet.” The policy however is synced and present in the registry.
My advice is to register a support ticket at Microsoft.