Auto assign Managed Google Play (Android) apps
Published: October 14, 2023 | Author: René Laas
The purpose of this blog is to inform you how to auto-assign Android Managed Google Play apps via an Azure Logic app.
If I have time, I check the Intune support TechNet, and if I can I help others with their question about Intune. So, my eyes fell on the question “auto assign”.
A few other people also responded with their point of view but didn’t answer the question. I purposed to use a logic app. The logic app can monitor a scheduled interval of the Graph API for newly added apps, if an app is new and not assigned, the logic app will automatically assign the app to all user groups.
Requirements:
Graph API Permissions:
What is an Azure Logic app
Azure Logic Apps is a cloud service that helps you schedule, automate, and orchestrate tasks, sbusiness processes, and workflows when you need to integrate apps, data, systems, and services across enterprises or organizations.
More information about Azure Logic Apps can be found here
Android Managed Google Play store
The Android Managed Google Play is an app platform within the Android ecosystem to make your public and private business apps available to your employees.
Designed to facilitate the deployment, and management of Android apps in your environment, the managed Google Play store provides your users with only the applications and tools authorized by your organization.
Graph API
The Microsoft Graph API provides a set of RESTful endpoints that enable developers to access and manipulate data in Microsoft Intune, a cloud-based service that enables organizations to manage and secure their mobile devices and apps. With the Graph API, administrators can get, create, update, and delete Intune resources such as devices, apps, policies, and profiles.
Administrators can use the Graph API to perform their tasks in Intune, such as retrieving device inventory information, deploying apps and profiles to devices, configuring device compliance policies, and managing device actions like wiping or locking a device. In summary, the Microsoft Graph API provides a powerful and flexible tool for administrators.
Let start with the registration of the application API permissions.
Note. In this example, I have used an App registration with App secret. Keep in mind this is not the most securest way to connect to the Graph API. For production environments please use a managed identity of Certificate.
- Open Microsoft Entra ID
- Open the Identity section in the left menu
- Click on Applications
- Click on App Registration
Or use the following link App registrations – Microsoft Entra admin center
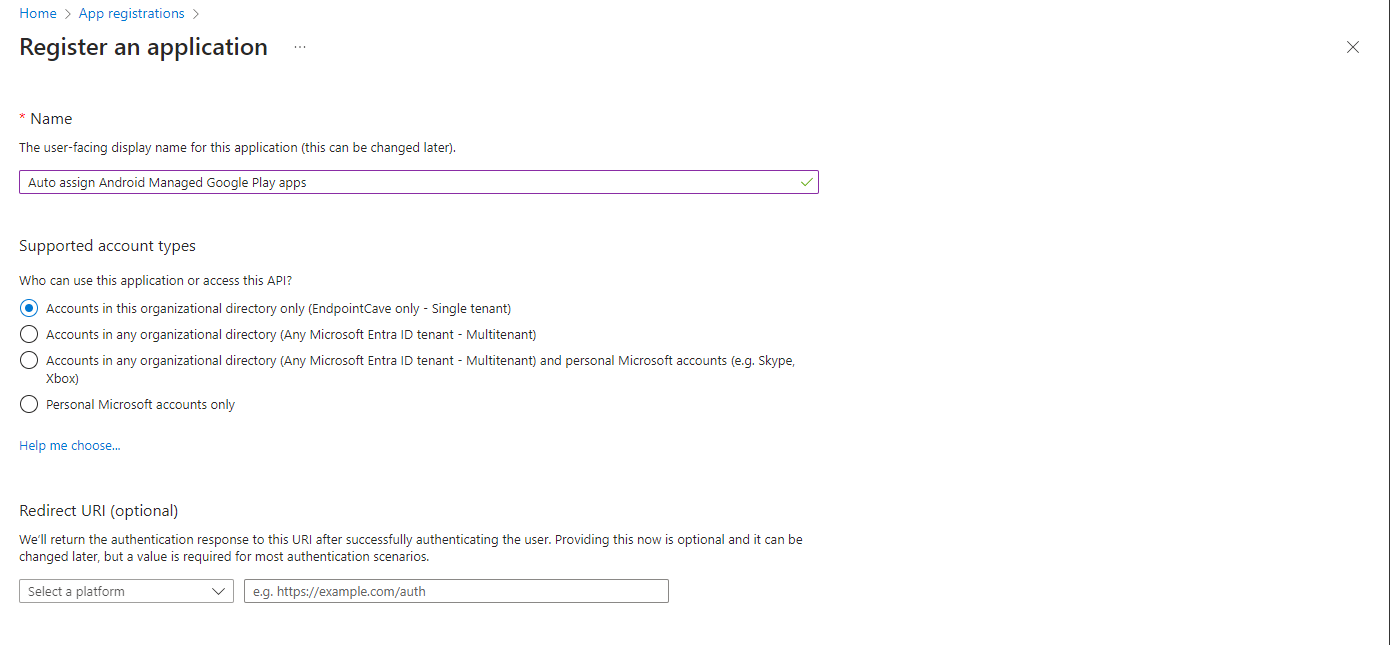
- Click on + New registration
- Configure an app name e.g., Auto assign Android Managed Google Play apps
- Click on the Register button, and the app will be created and automatically opened.
- In the menu click on API Permissions
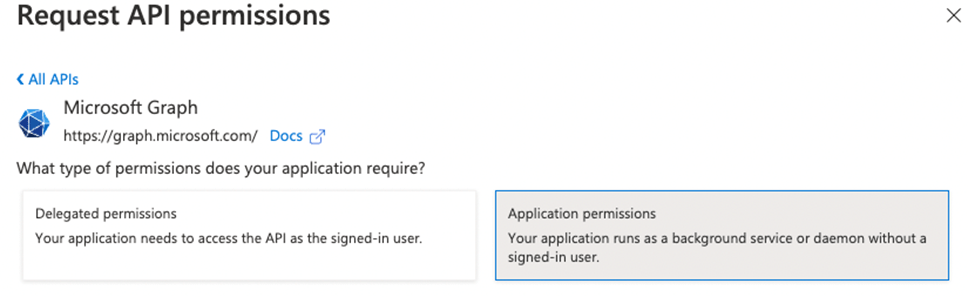
- Click on+ Add a permission
- Select Microsoft Graph and select Application permissions
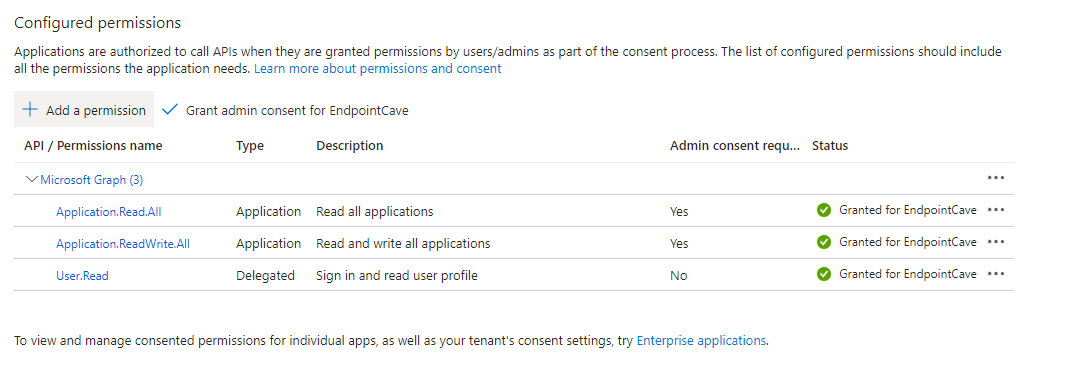
- Search and add the following permissions:
Application.Read.All
Application.ReadWrite.All- Grant admin consent for your organization
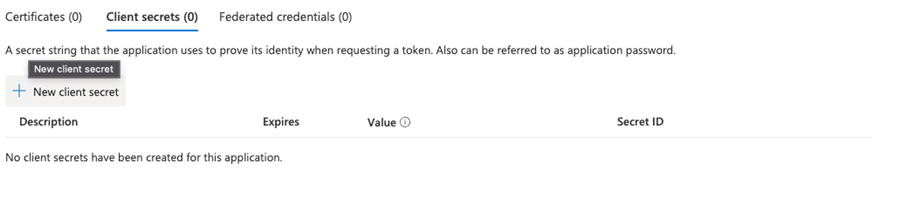
- In the menu, click on Certificates & Secrets
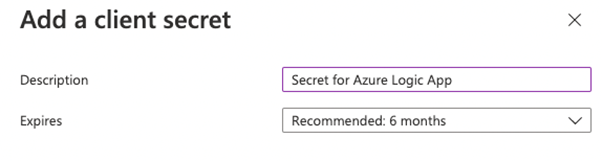
- Click on + New Client secret
- Set a description and the expiry of the secret and click on Add
- Copy the value of the secret,
- Go to the overview page and copy the Client ID and Tenant ID
Let start Automate your retire actions and report via an Azure Logic App
Note. Rename every Azure Logic App action to match the screenshots!
- Open Microsoft Azure.
- Search for Logic App
- Click on + Add
- Select an existing Resource Group or create a new Resource Group
- Select the instance Type (I have chosen Consumption, but check the Azure Calculator which option fits your environment)
- Select your region and click on Review + Create
- Check the details on the Review + Create page and click on Create
- After the deployment is completed, go to your new Logic App via Go to Resource button
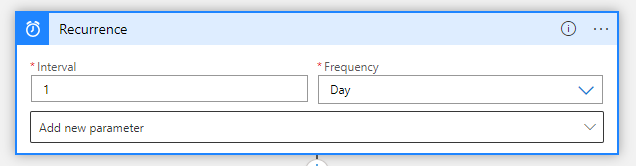
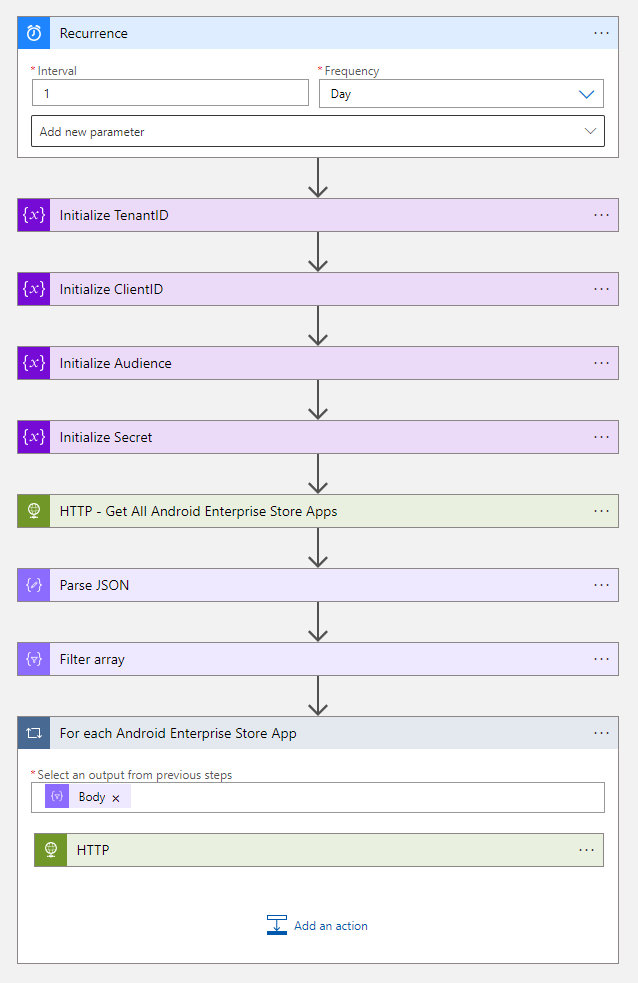
- The first step of the workflow is the Recurrence trigger, based on the desired interval
Note. I have used a daily interval in this blog.
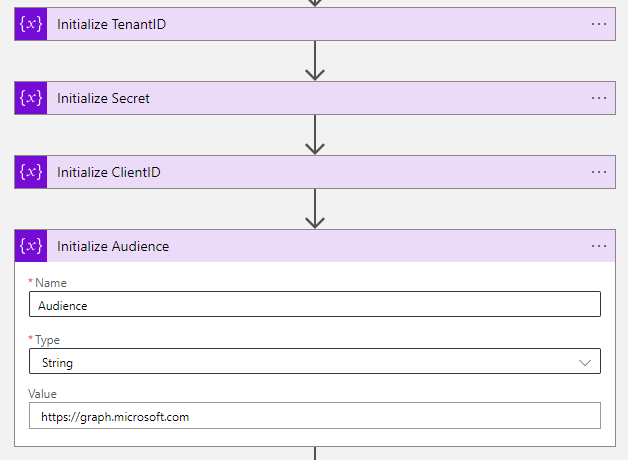
- The next four steps of the workflow are to initialize variables.
| Name | Type | Value | |
|---|---|---|---|
| Initialize TenantID | TenantID | String | {Paste your Tenant ID} |
| Initialize ClientID | ClientID | String | {Paste your Client ID} |
| Initialize Audience | Audience | String | https://graph.microsoft.com |
| Initialize Secret | Secret | String | {Paste your Secret} |
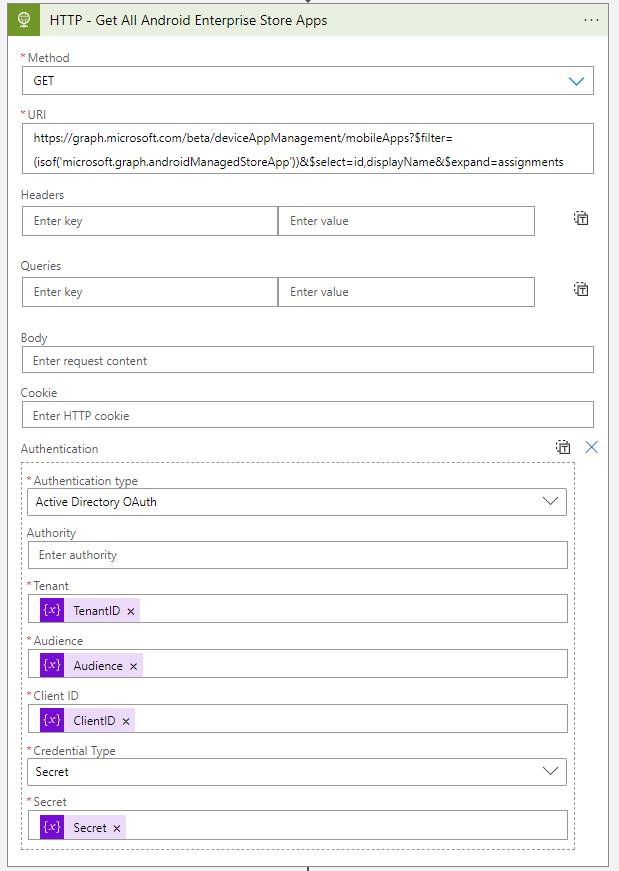
- The first action after the four variables is the HTTP action. With the HTTP connector, the logic app will connect to the Graph API
URI:
https://graph.microsoft.com/beta/deviceAppManagement/mobileApps?$filter=(isof('microsoft.graph.androidManagedStoreApp'))&$select=id,displayName&$expand=assignments| Method | GET |
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
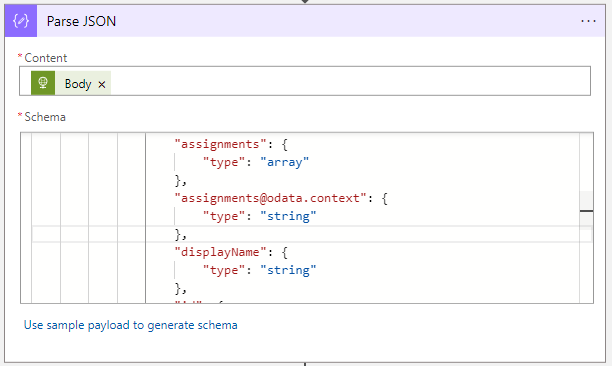
@{body('HTTP_-_Get_All_Android_Enterprise_Store_Apps')}Schema:
{
"properties": {
"@@odata.context": {
"type": "string"
},
"@@odata.count": {
"type": "integer"
},
"value": {
"items": {
"properties": {
"@@odata.type": {
"type": "string"
},
"assignments": {
"type": "array"
},
"[email protected]": {
"type": "string"
},
"displayName": {
"type": "string"
},
"id": {
"type": "string"
}
},
"required": [
"@@odata.type",
"id",
"displayName",
"[email protected]",
"assignments"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
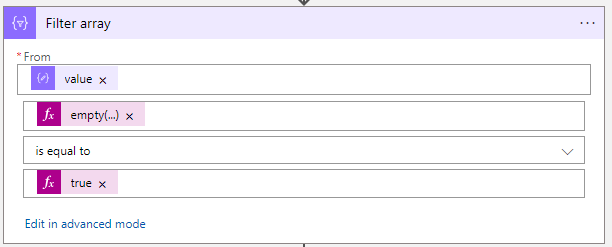
}- After the Parse JSON action, create a Filter array action.
| Field | Value |
|---|---|
| From | @body(‘Parse_JSON’)?[‘value’] |
| Choose a value | @empty(item()?[‘assignments’]) |
| Is equal to | |
| Choose a value | @true |
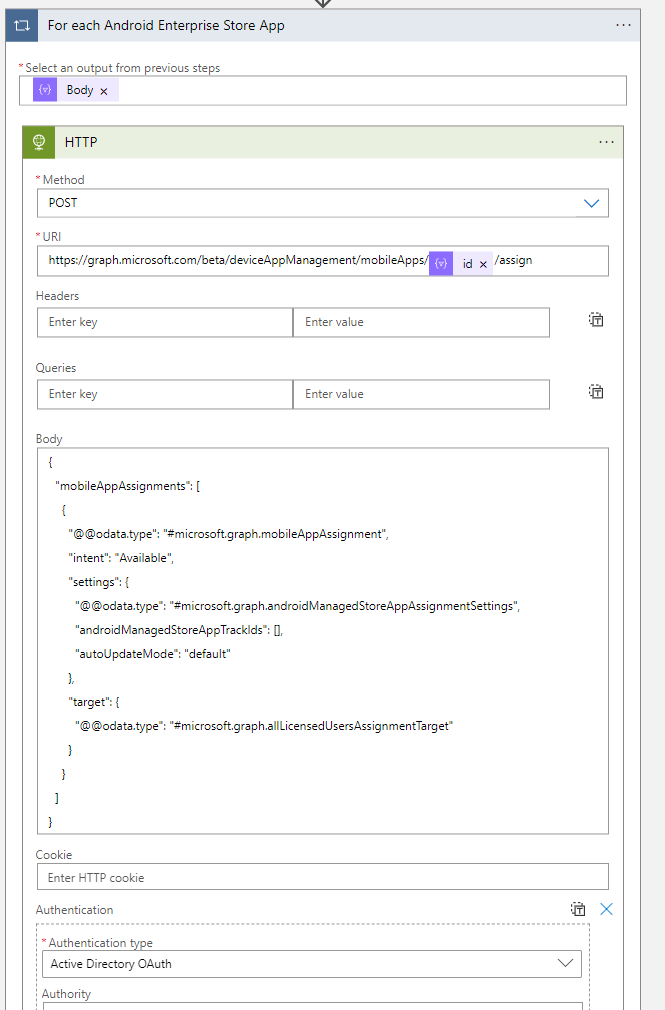
- After the Filter Array action. Create a for each loop with the output of the Body property of the Filter array action.
- Within the For each Android Enterprise Store App loop action, create another HTTP action.
| Field | Value |
|---|---|
| Method | POST |
URI:
https://graph.microsoft.com/beta/deviceAppManagement/mobileApps/@{items('For_each_Android_Enterprise_Store_App')?['id']}/assignBody:
{
"mobileAppAssignments": [
{
"@@odata.type": "#microsoft.graph.mobileAppAssignment",
"intent": "Available",
"settings": {
"@@odata.type": "#microsoft.graph.androidManagedStoreAppAssignmentSettings",
"androidManagedStoreAppTrackIds": [],
"autoUpdateMode": "default"
},
"target": {
"@@odata.type": "#microsoft.graph.allLicensedUsersAssignmentTarget"
}
}
]
}| SETTING | VALUE |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
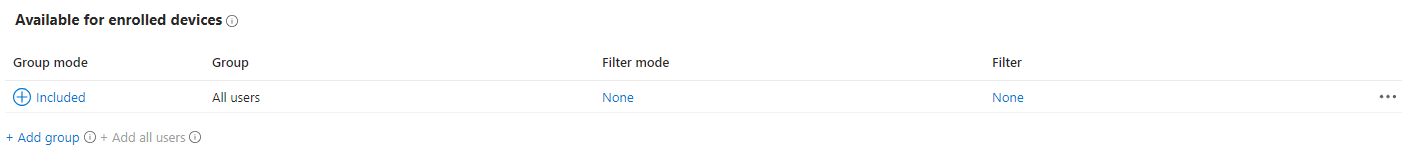
- The logic app will now run every day. It will search for unassigned managed Google Play apps. If an app is not assigned, it will automatically assigned to the All user group to the Available for Enrolled Devices assignment method of the app.



 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands. Albert Stoynov
Albert Stoynov
Leave a Reply
Want to join the discussion?Feel free to contribute!