Onboard devices to Defender for Endpoint via Intune connector
Published: February 16, 2023 | Author: René Laas
The purpose of this blog post is to inform you how to onboard your Intune-managed devices to Defender for Endpoint via the built-in Intune connector.
In today’s world security is more important than ever and staying up to date plays a key role in keeping a secure environment. One of the key features of Microsoft Defender for Endpoint is its ability to protect devices against a wide range of threats, including malware, ransomware, phishing attacks, and other types of cyber-attacks. It can also detect vulnerabilities on your devices.
In this blog post, I will explain how to onboard your device to Defender for Endpoint. There are several options to onboard your devices. In this blog post, I will explain the different options and I will give you an explanation of why I prefer the connector option. I will explain in this blog also how to configure the built-in option.
Requirements:
Defender for Endpoint
Defender for Endpoint is a cloud-based endpoint security solution developed by Microsoft.
It provides advanced threat protection, proactive threat hunting, and vulnerability management for endpoints, such as desktops, laptops, and mobile devices. It uses artificial intelligence and machine learning algorithms to detect and respond to threats in real time, including zero-day attacks and fileless malware.
With Defender for Endpoint, you are also able to configure features like device control, application control, and network protection to prevent your organization against for instance security breaches and unwanted software.
Microsoft Defender for Endpoint integrates with other Microsoft products and can be managed through the Microsoft 365 Security portal.
Onboard devices to Defender for Endpoint options
Defender for Endpoint offers several onboarding options to help organizations quickly deploy and configure the solution:
Windows 10
- Group Policy
- Microsoft Intune connector
- Microsoft Intune configuration profile
- Microsoft Endpoint Configuration Manager
- Local Script (for up to 10 devices)
- Script for VDI Non-persistent devices
Windows Server
- Group Policy
- Microsoft Endpoint Configuration Manager
- Local Script (for up to 10 devices)
- Script for VDI Non-persistent devices
MacOS
- Microsoft Intune connector
- Microsoft Intune configuration profile
- Jamf
- Local Script (for up to 10 devices)
Mobile devices (Android, iOS)
- Microsoft Intune connector
- Microsoft Intune VPN Configuration Profile
- Defender for Endpoint App
Preferred option
As you can read there are several options to onboard your device to Defender for Endpoint. I prefer the Microsoft Intune connector for Mobile devices, laptops, and desktops because using the Intune connector to onboard devices to Microsoft Defender for Endpoint provides a more streamlined and integrated approach.
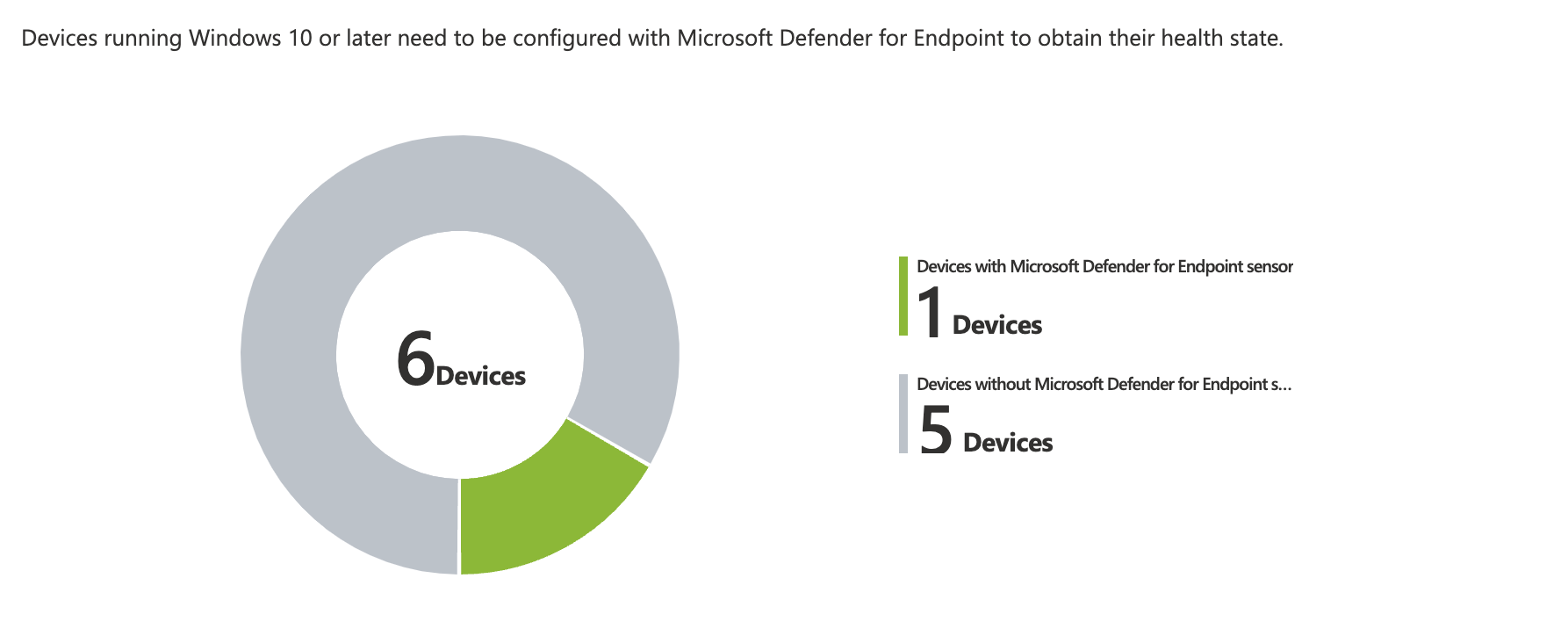
But this can also be achieved with all the other options, but I really like the overview and report of how many Intune devices are not onboarded to Defender for Endpoint. I don’t have to take care of the onboarding package etc. Keep it simple and let Microsoft do the hard work.
How to configure onboard devices to Defender for Endpoint
- Open Microsoft Intune
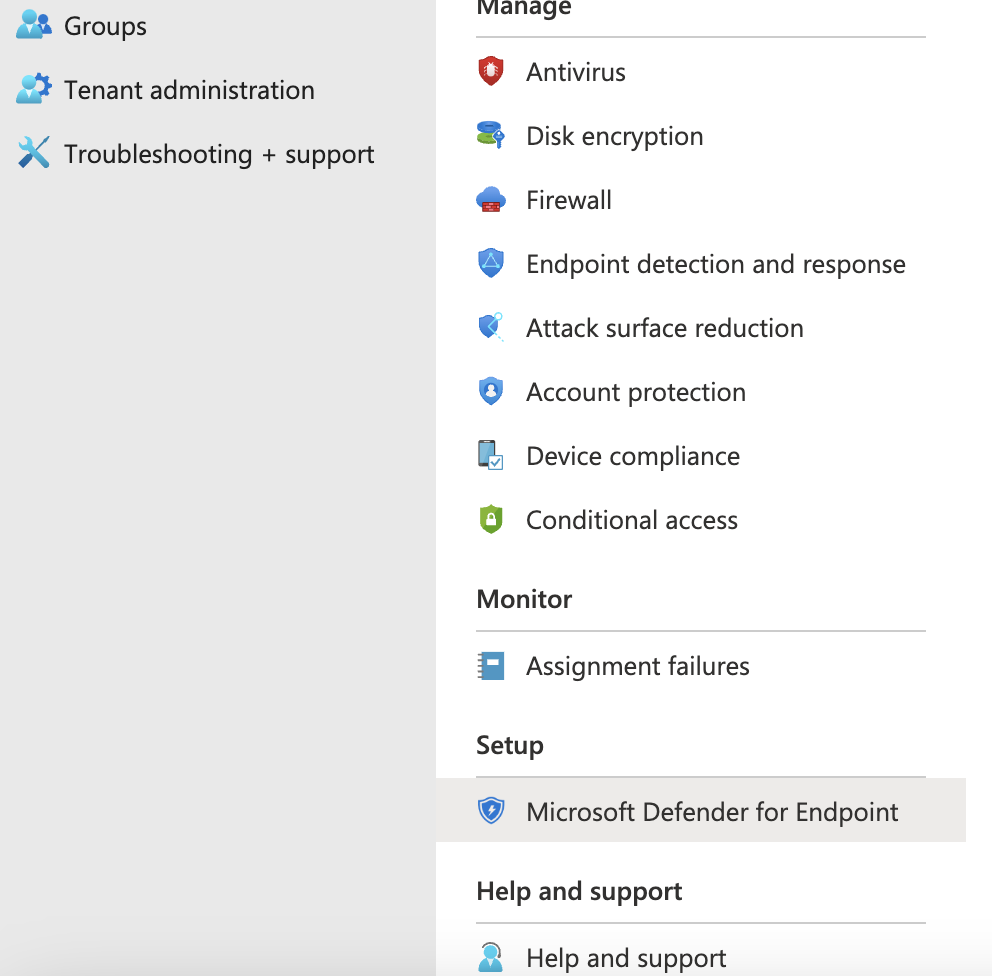
- In the menu select Endpoint Security
- In the submenu, Click on Microsoft Defender for Endpoint
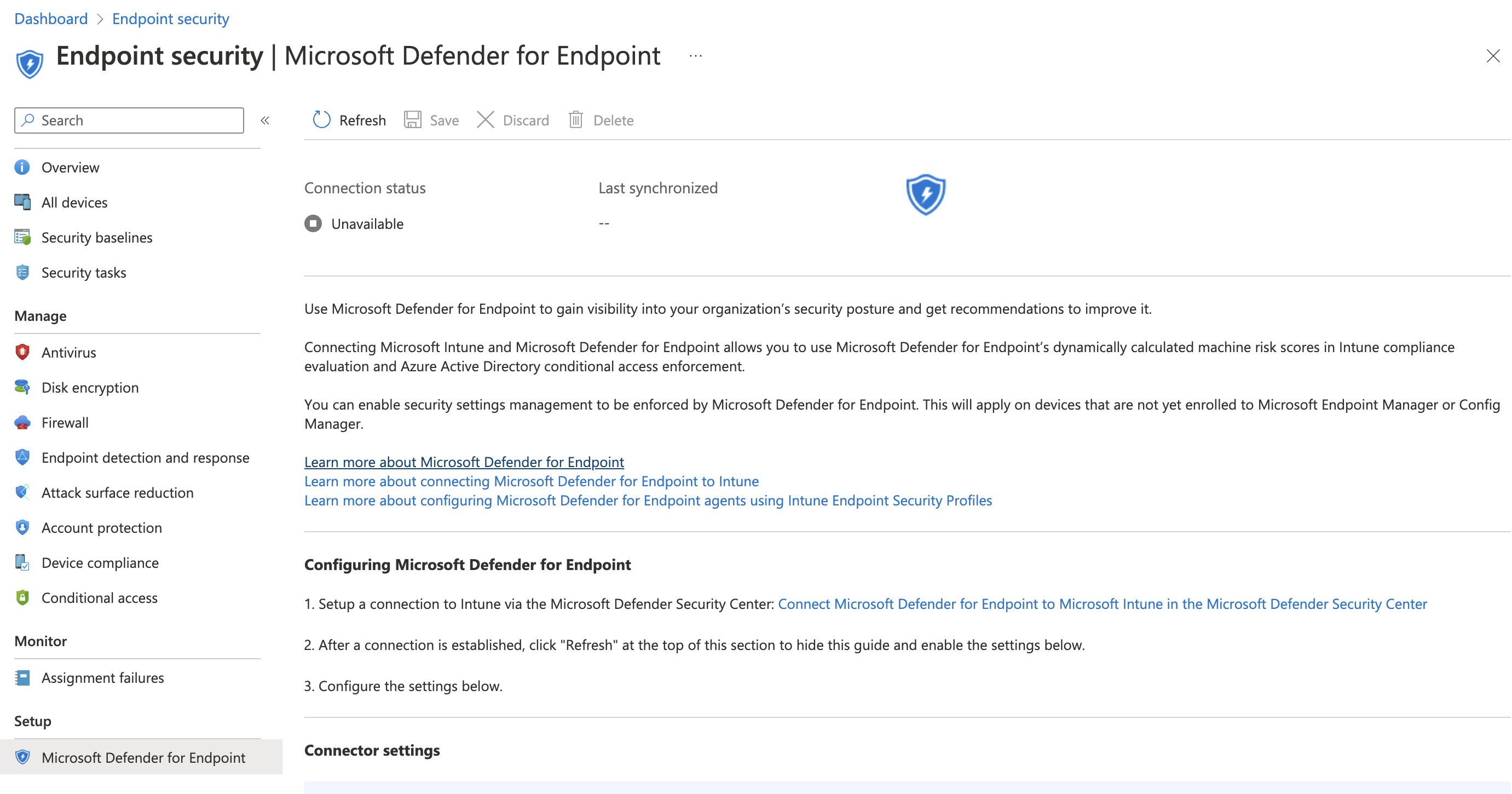
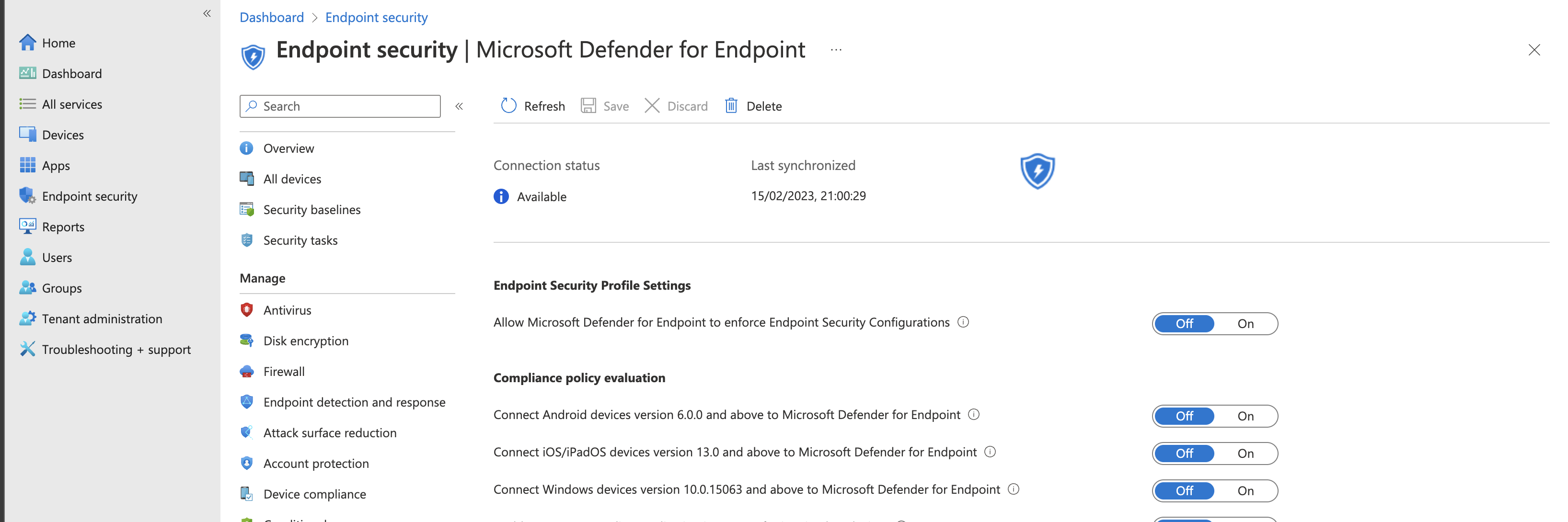
- The connection status of the Defender for Endpoint connector is still Unavailable
- In the menu scroll down and click on Settings
- On the settings page, click on Endpoints
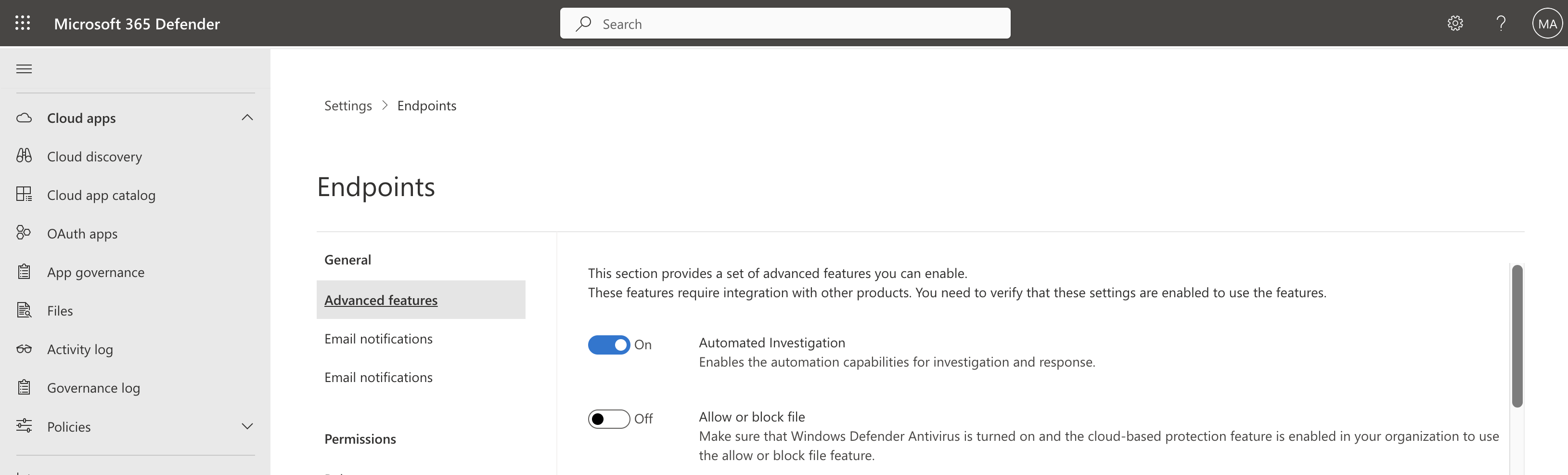
- On the Endpoint page, click on Advanced features under General
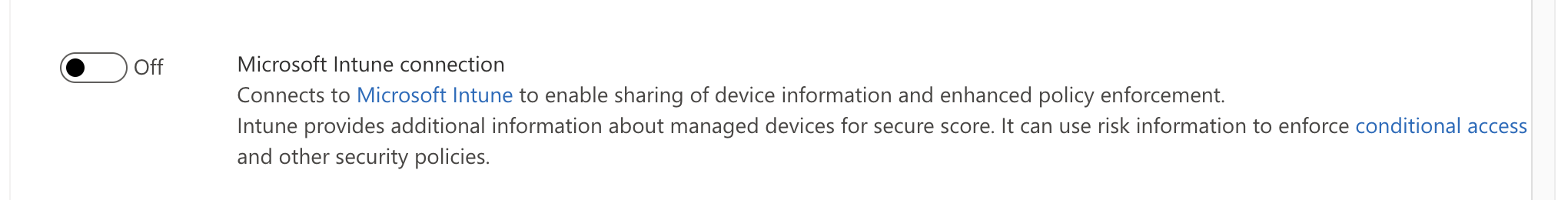
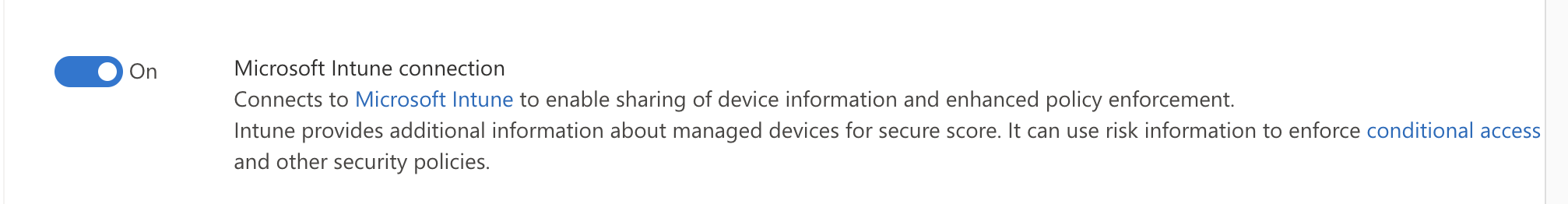
- In the Advanced features section, Scroll down to the Intune connector
- Turn on the toggle of the Intune connector
- Click on Save preferences at the end of the page
- Open Microsoft Intune
- In the menu select Endpoint Security
- In the submenu, Click on Microsoft Defender for Endpoint
- The connection status of the Defender for Endpoint connector is now Available instead of Unavailable
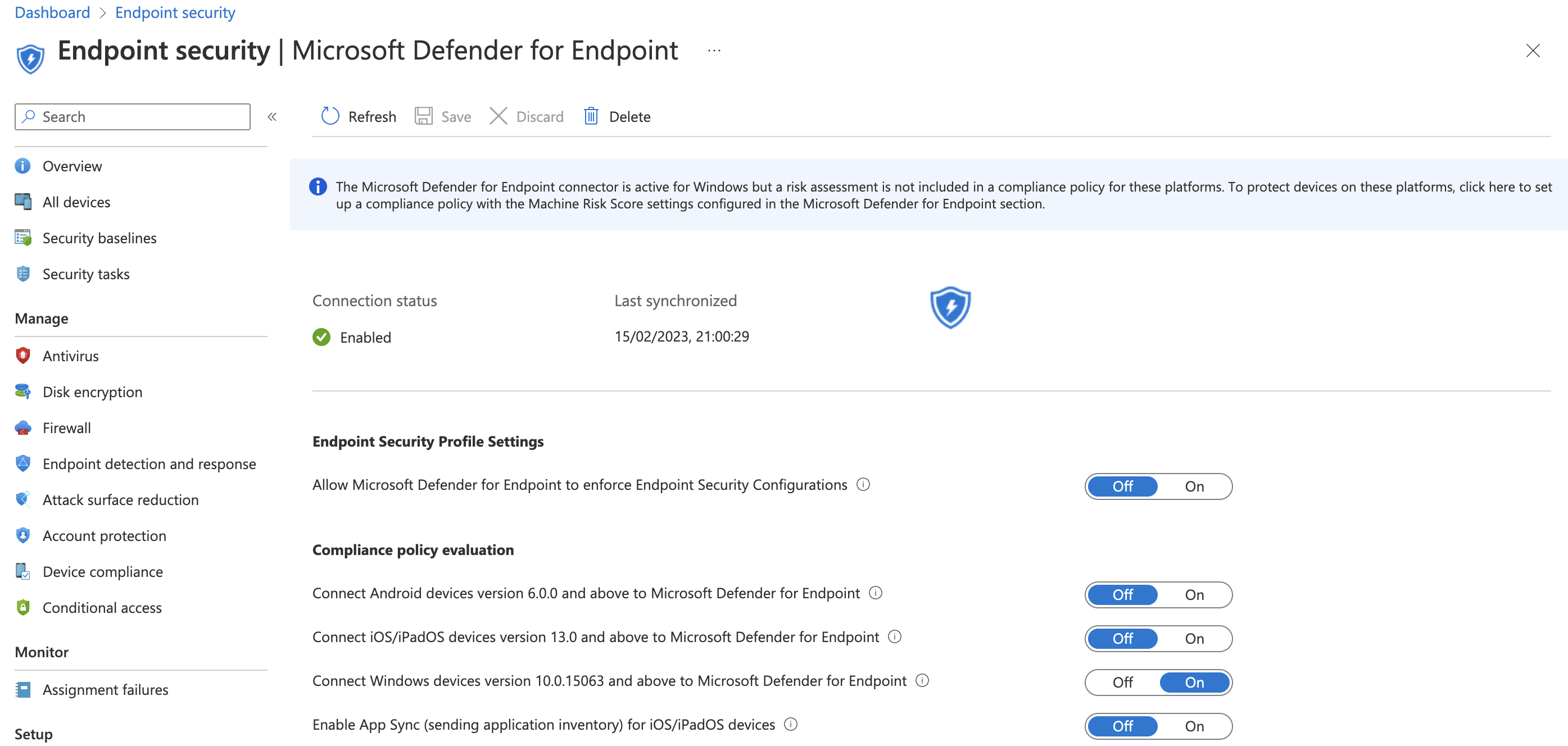
- Turn on the toggle of the Connect Windows devices version 10.0.15063 and above to Microsoft Defender for Endpoint setting
- Click on Save
- The connection status of the Defender for Endpoint connector is now Enabled
- Go to Endpoint detection and response in the menu under Manage
- Click on + Create Policy
- Select Windows 10 and later as the Platform
- Select Endpoint detect and response as the Profile
- Click on Create at the bottom of the pop-up
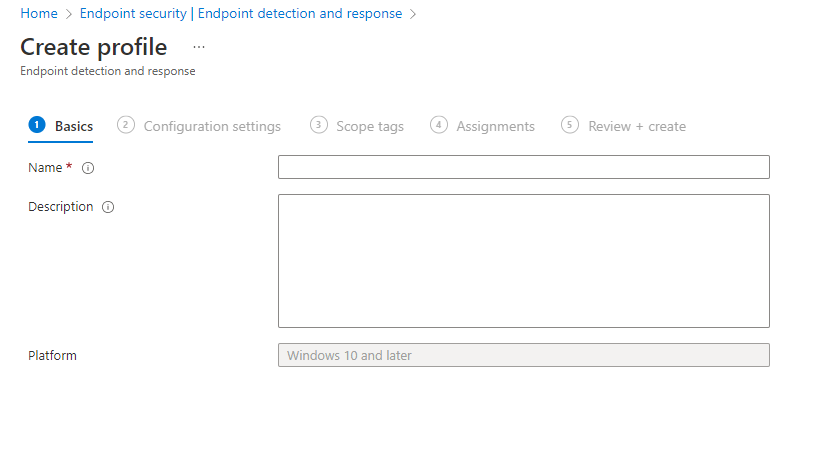
- Provide a Policy name, I use the following name “EndpointCave-PRD-Onboard Device To Defender”
- Set a Description if needed
- Click on Next
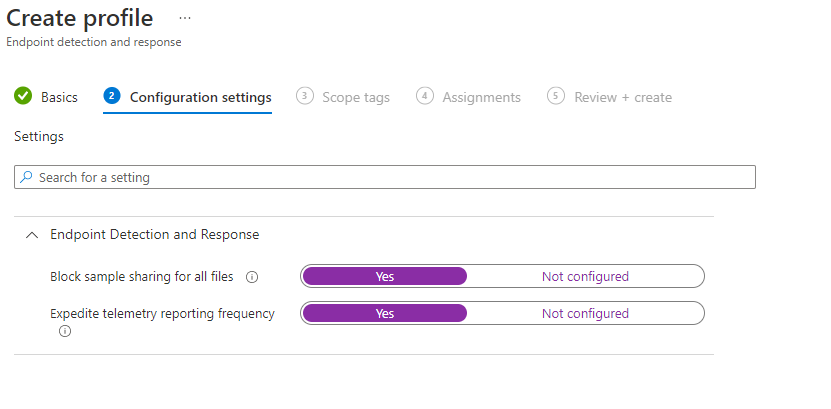
- Enable the Expedite telemetry setting
- Enable sample sharing for all files also if you want to submit unknown files to Defender for Endpoint for deep analysis
- Click on Next
- Set a Scope tag if needed
- Click on Next
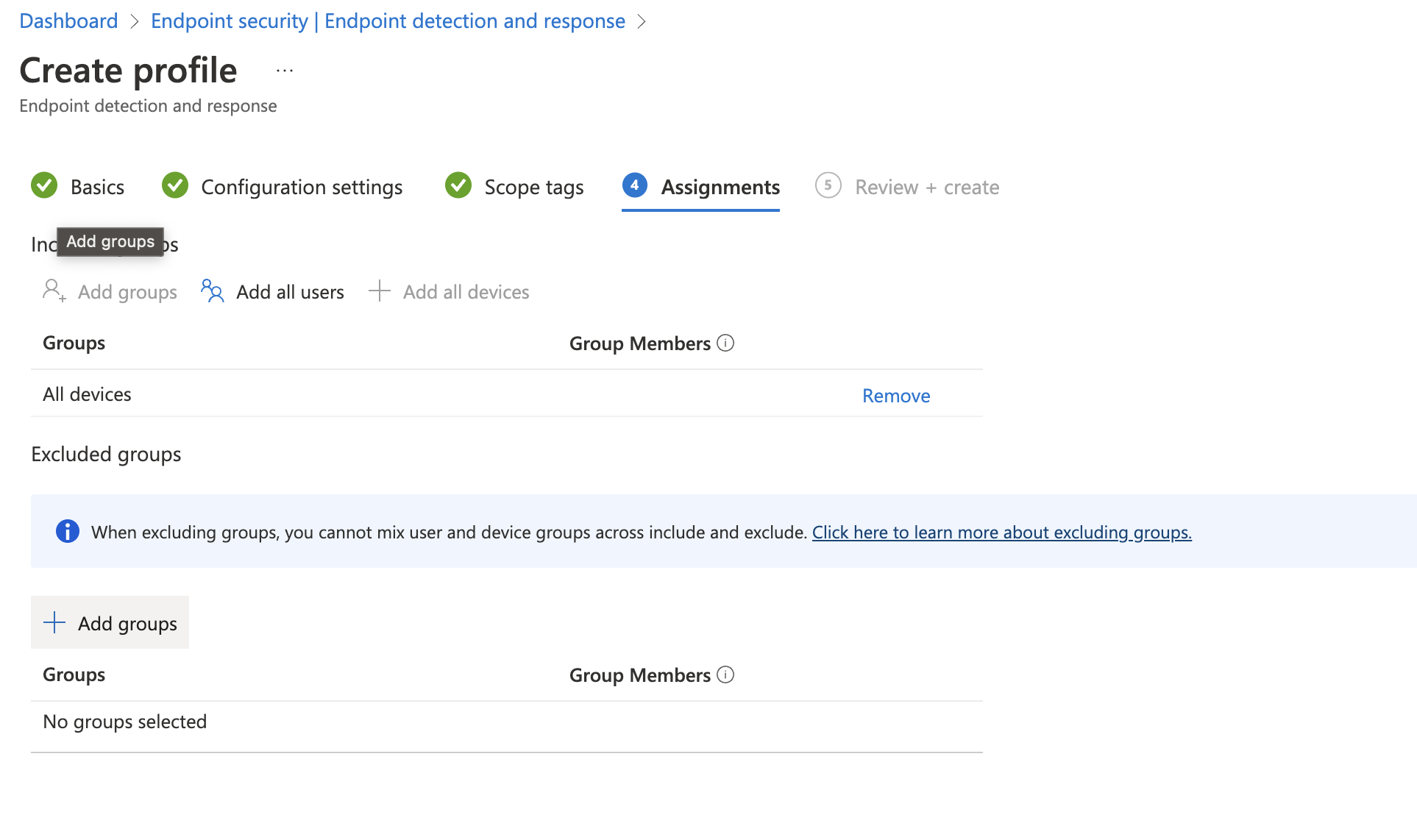
- Assign the policy to All devices or to a Device group with devices that needs to be onboarded to Defender for Endpoint
- Click on Next and review your Endpoint detection and response profile
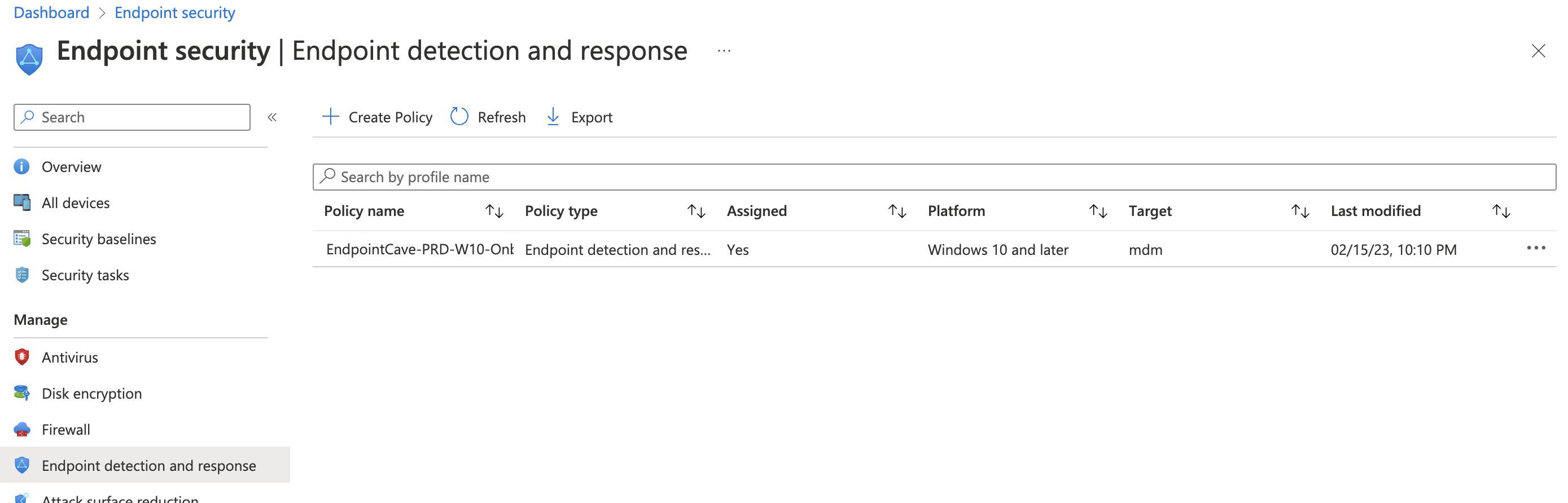
- On the Review + Create page, select Create
- All Devices or the Devices in the Device group will now automatically be onboarded to Defender for Endpoint

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands. GuerrillaBuzz Blockchain PR Agency
GuerrillaBuzz Blockchain PR Agency  Hannah Wright
Hannah Wright
Leave a Reply
Want to join the discussion?Feel free to contribute!