Get every week a Defender for Endpoint VM recommendation
Published: February 05, 2023 | Author: René Laas
The purpose of this blog post is to inform you how to get every week a Defender for Endpoint Vulnerability Management recommendation
Today’s world security is more important than ever and staying up to date plays a key role in keeping a secure environment. One of the key features of Microsoft Defender for Endpoint is its ability to protect devices against a wide range of threats, including malware, ransomware, phishing attacks, and other types of cyber-attacks. It can also detect vulnerabilities on your devices.
To protect your organisation for getting hacked, you have to mitigate the vulnerabilities. In this blog post, I will explain how to get a weekly teams notification with one of the Defender for Endpoint VM recommendations that you have to mitigate.
Requirements:
Security API Permissions:
Defender for Endpoint Vulnerability Management
Defender for Endpoint Vulnerability Management is a security solution offered by Microsoft that helps organisations identify, assess, and remediate security vulnerabilities on their endpoint devices. Defender scans endpoints for vulnerabilities and provides recommendations for remediation. This helps organisations proactively identify and remediate security weaknesses before they can be exploited by attackers.
Additionally, Defender for Endpoint provides real-time protection against malware, viruses, and other security threats to prevent them from compromising endpoints. It also uses machine learning algorithms and other security technologies to detect and respond to security threats in real-time.
Overall, Defender for Endpoint helps organisations to improve their security posture, increase visibility into endpoint security, and reduces the risk of getting hacked.
What is an Azure Logic App
Azure Logic Apps is a cloud service that helps you schedule, automate, and orchestrate tasks, business processes, and workflows when you need to integrate apps, data, systems, and services across enterprises or organizations.
More information about Azure Logic Apps can be found here
What are adaptive cards?
Adaptive Cards are platform-agnostic snippets of UI, authored in JSON, that apps and services can openly exchange. When delivered to a specific app, the JSON is transformed into a native UI that automatically adapts to its surroundings. It helps design and integrate lightweight UI for all major platforms and frameworks.
More information about Adaptive cards can be found here
Create an Azure AD App Registration
- Open azure.com
- Click on Azure Active Directory
- Click on App Registration in the left menu
Or use the following link Active Directory | App Registration
- Click on + New registration
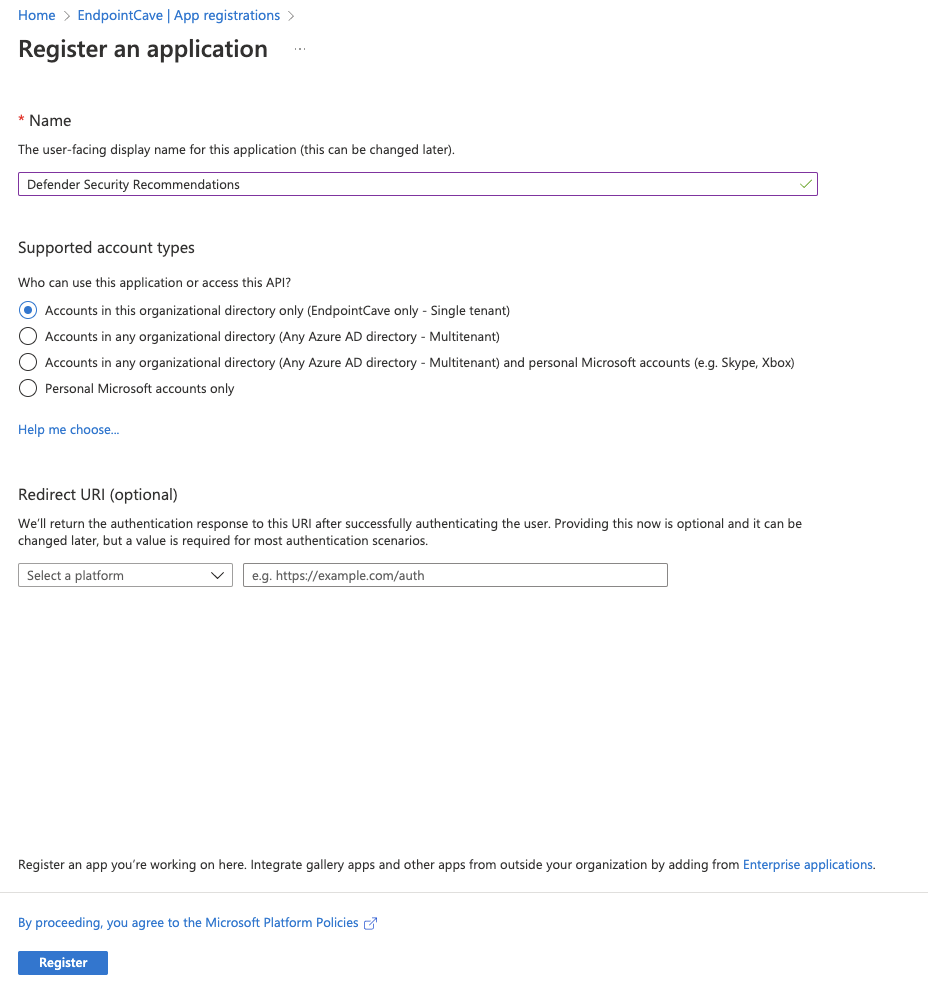
- Configure an app name e.g., Defender Security Recommendations
- Click on the Register button, the app will be created and automatically opened.
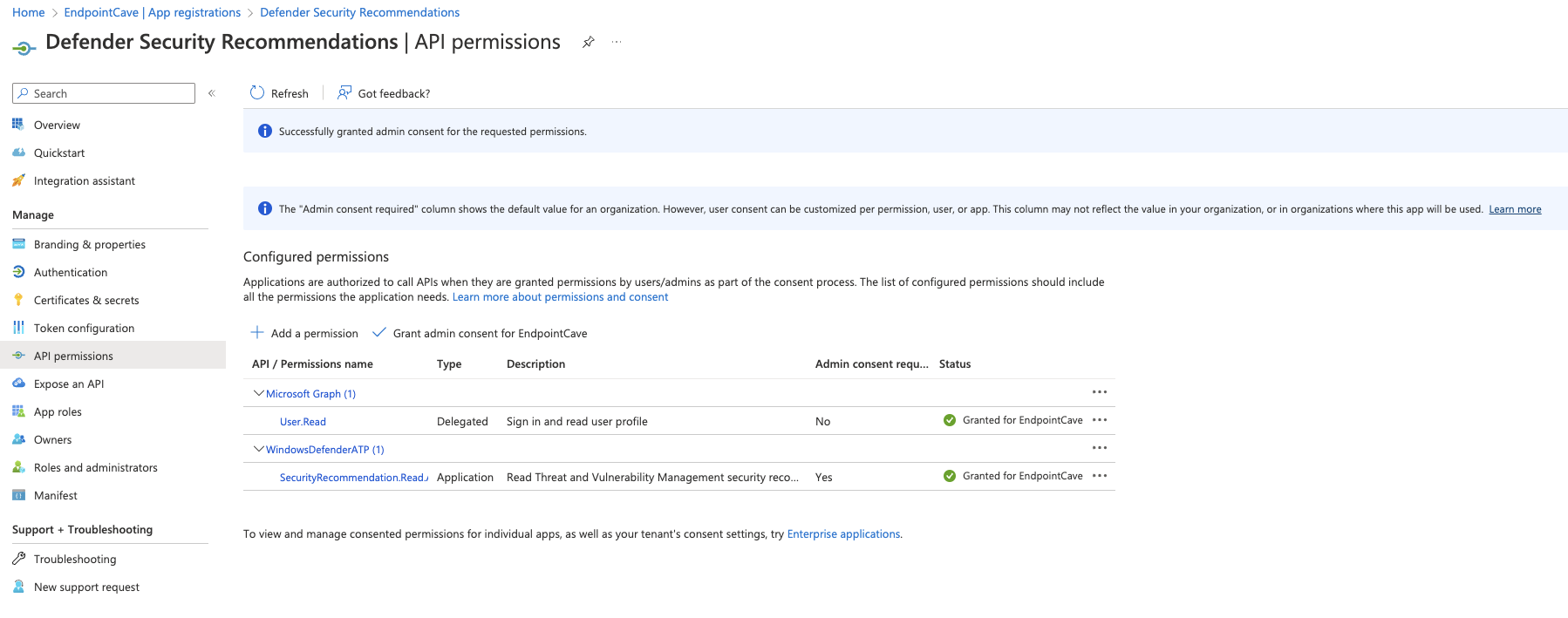
- In the menu click on API Permissions
- Click on+ Add a permission
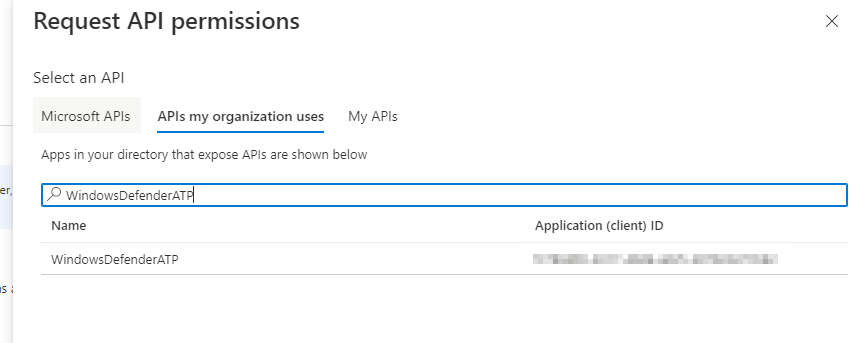
- Select APIs my organization uses and search for WindowsDefenderATP
- Search and add the following permissions
SecurityRecommendation.Read.All- Grant admin consent for your organisation
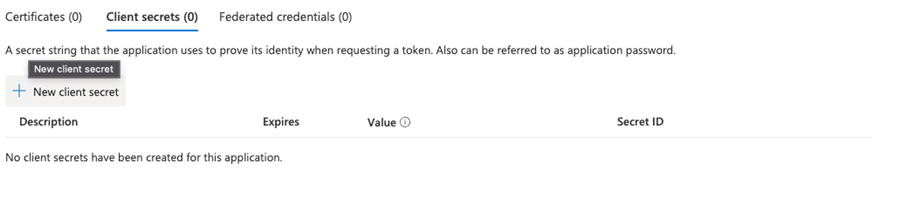
- In the menu click on Certificates & Secrets
- Click on + New Client secret
- Set a description and the expiry of the secret and click on Add
- Copy the value of the secret, the secret is needed for the flow.
- Go to the overview page and copy the Client ID and Tenant ID, those are also needed in the flow.
Create a Teams Channel Webhook
- Open Microsoft Teams
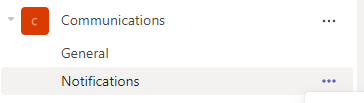
- Click on Teams in the menu and select the correct team
- Click on the 3 bullets behind a Teams channel
- In the menu click on Connectors
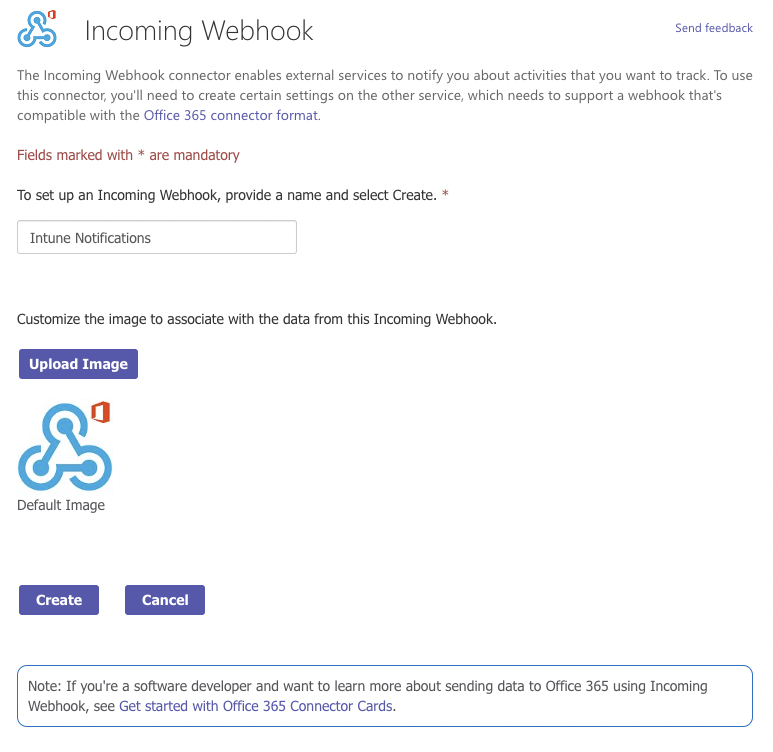
- The connectors screen will pop up and search for “Incoming Webhook” and select Configure
- The connector will be added to the channel, but first, we must provide a name.
Note. This name will be displayed for every notification.
- Upload another logo if needed.
- Click on create
- A Webhook URL will automatically be created, copy this URL because it is needed in the flow.
- Click on Done
Create an Azure Logic App for Defender for Endpoint recommendations
Note. Rename every Azure Logic App action to match the screenshots!
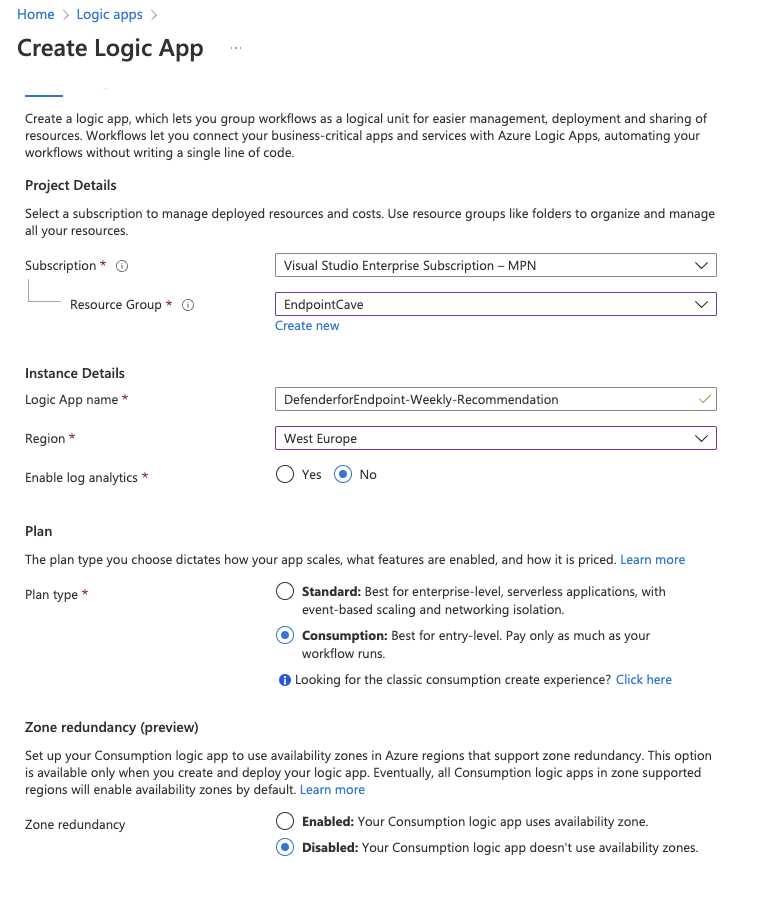
- Open portal.azure.com
- Search for Logic App
- Click on + Add
- Select an existing Resource Group or create a new Resource Group
- Select the instance Type (I have chosen for Consumption, but check the Azure Calculator which option fits your environment)
- Select your region and click on Review + Create
- Check the details on the Review + Create page and click on Create
- After the deployment is completed, go to your new Logic App via Go to Resource button
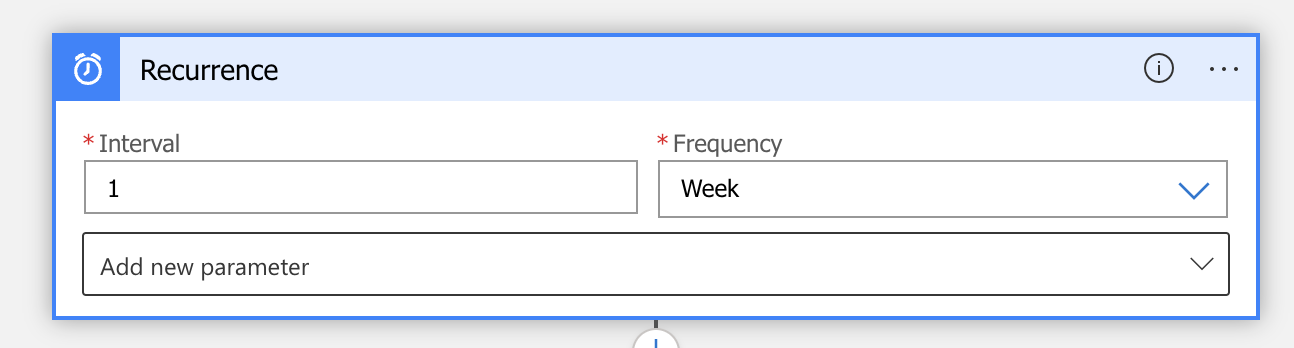
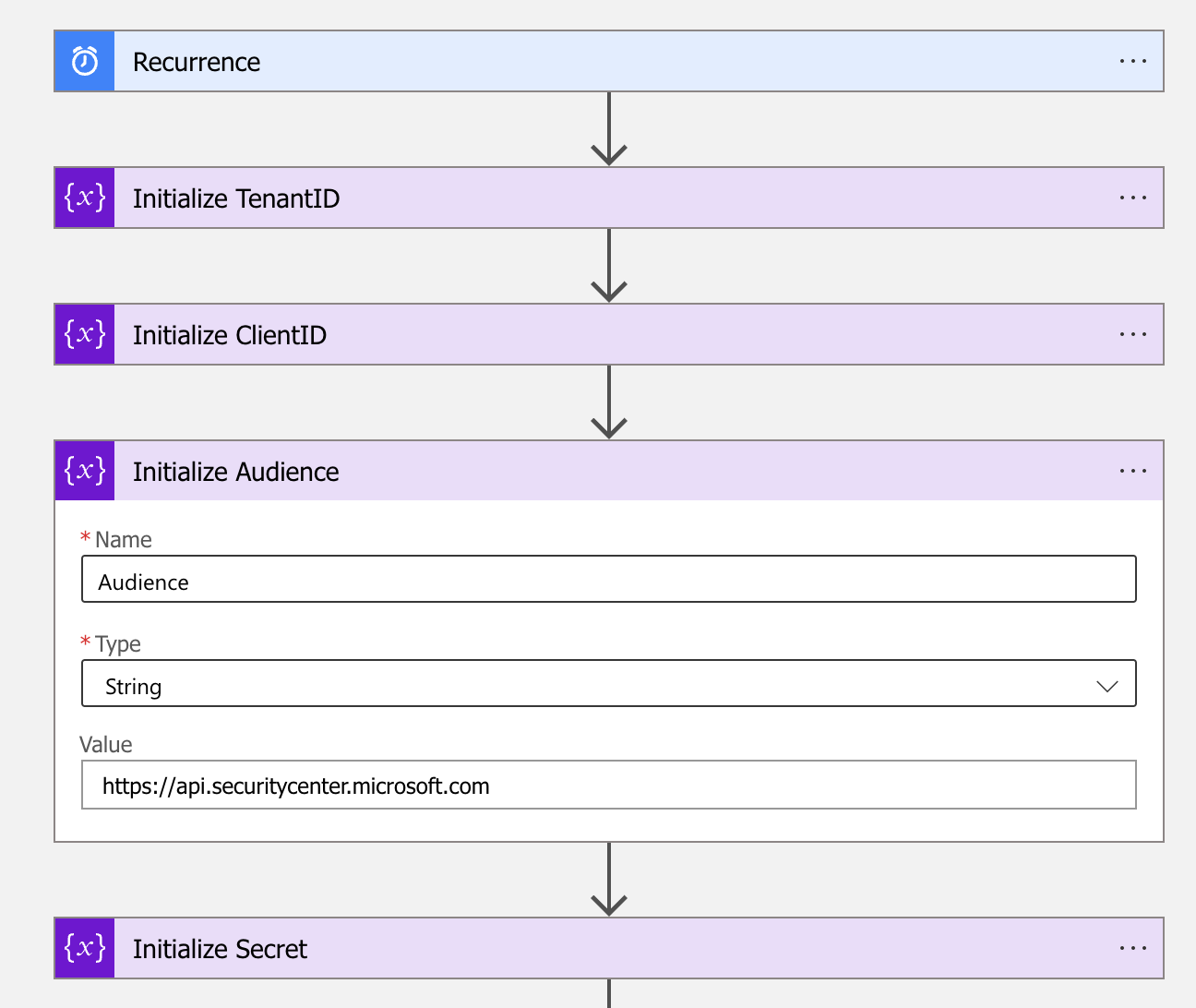
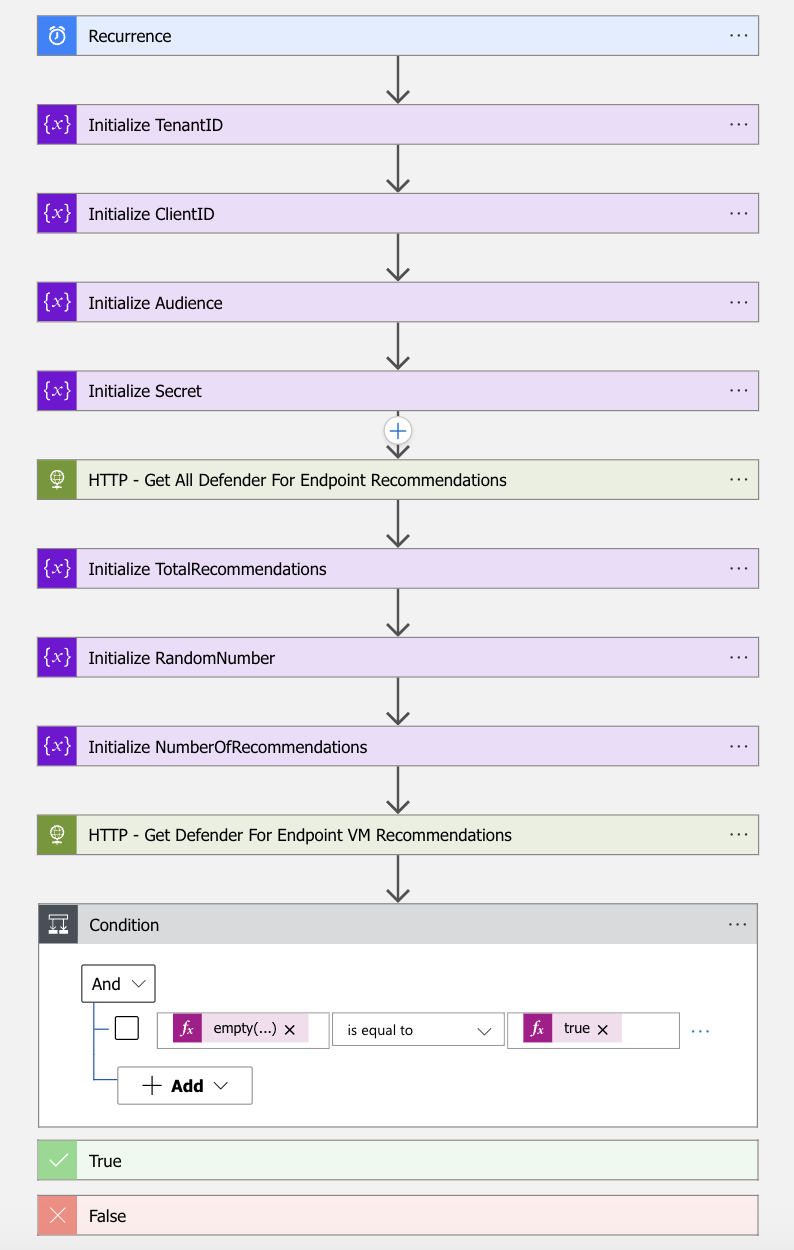
- The first step of the workflow is the Recurrence trigger, based on the desired interval
Note. I have used a 1 week interval in this blog.
- The next four steps of the workflow are to initialize variables.
| Initialize Audience Variable | Initialize TenantID Variable | Initialize ClientID Variable | Initialize Secret Variable | |
|---|---|---|---|---|
| Name | Audience | ClientID | TenantID | Secret |
| Type | String | String | String | String |
| Value | https://api.securitycenter.microsoft.com | {Paste your Tenant ID} | {Paste your Client ID} | {Paste your Secret} |
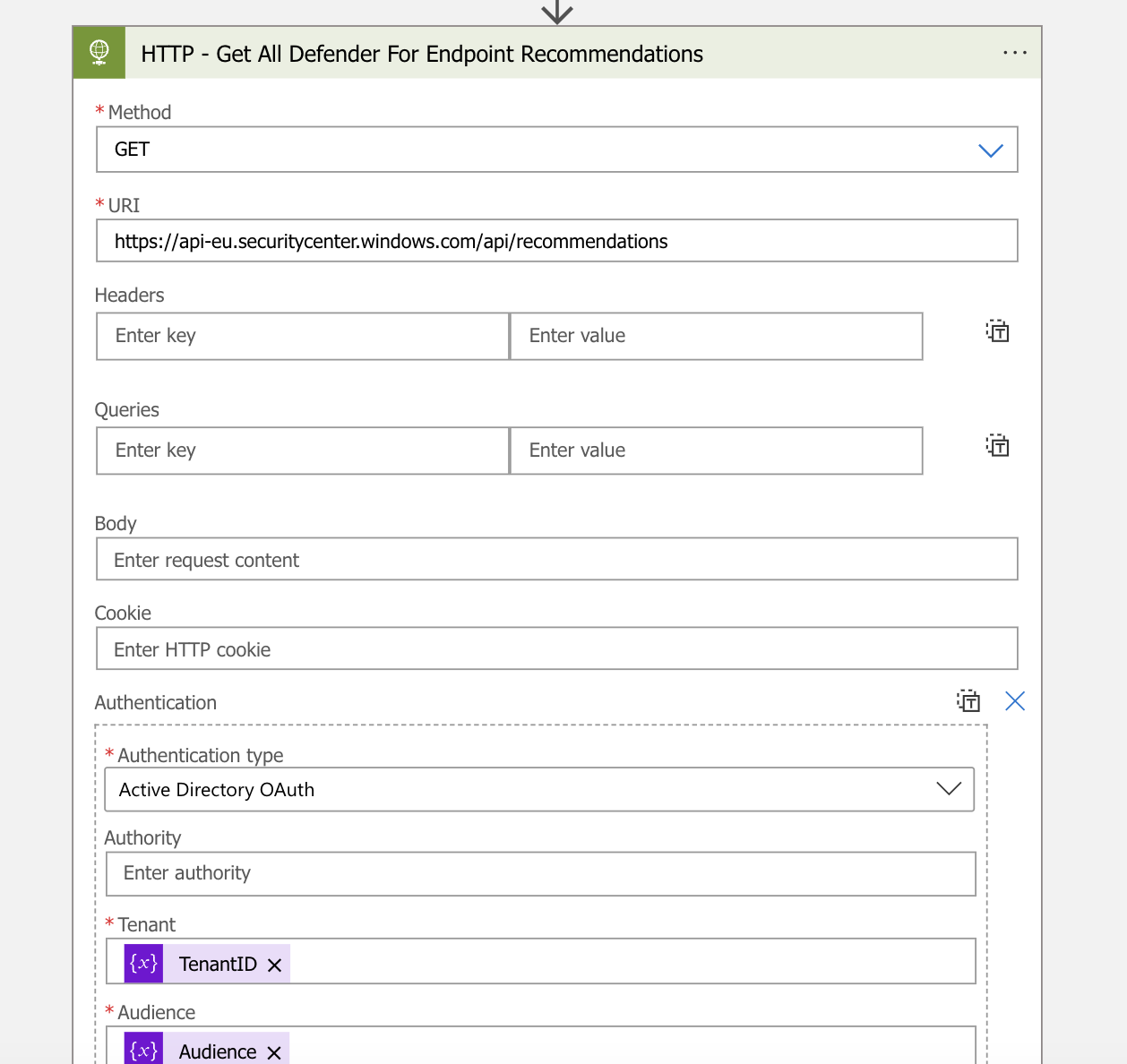
- The next step is to get all Defender for Endpoint VM recommendations via a HTTP action, set the below HTTP configuration
URI:
https://api-eu.securitycenter.windows.com/api/recommendations| Method | GET |
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
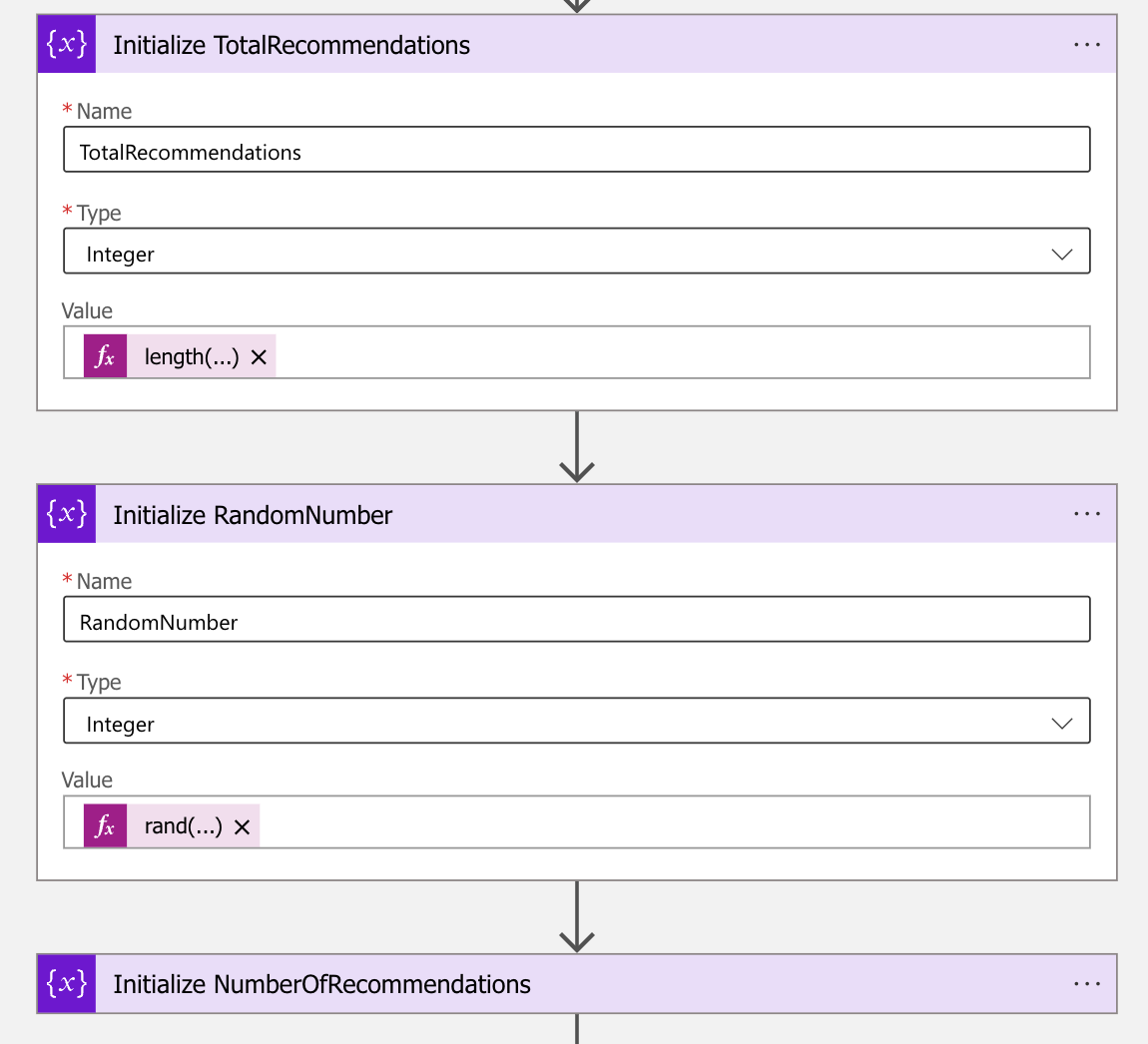
- After the HTTP – Get All Defender For Endpoint Recommendations action you need to initialize three more variables
| Initialize TotalRecommendations | Initialize RandomNumber | Initialize NumberOfRecommendations | |
|---|---|---|---|
| Name | TotalRecommendations | RandomNumber | NumberOfRecommendations |
| Type | Integer | Integer | Integer |
| Value | length(body(‘HTTP_-_Get_All_Defender_For_Endpoint_Recommendations’)?[‘value’]) | rand(1,variables(‘TotalRecommendations’)) | 1 |
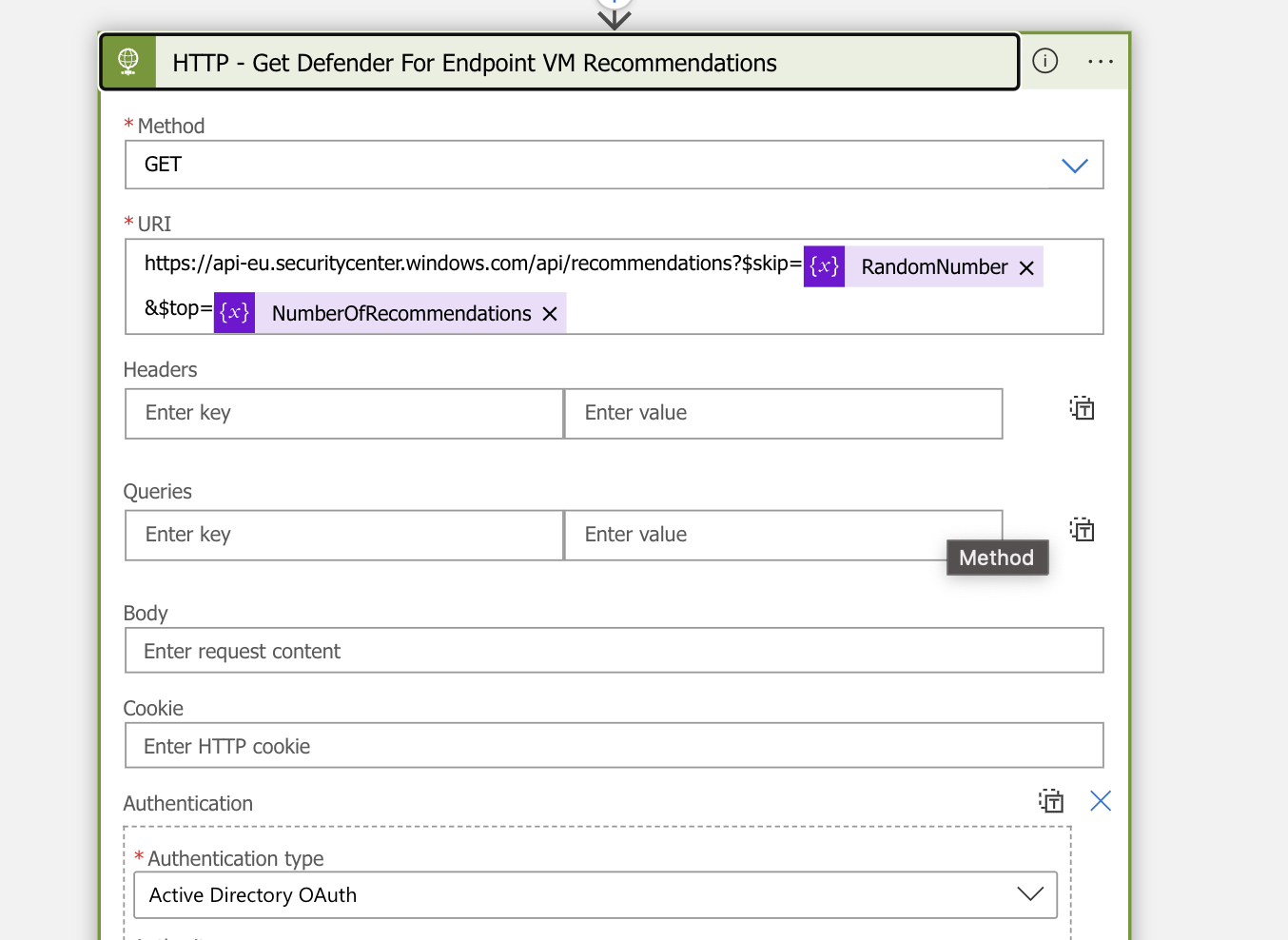
- After the Initialize NumberOfRecommendations action, create a HTTP action to get the recommendation, set the below HTTP configuration
URI:
https://api-eu.securitycenter.windows.com/api/recommendations?$skip=@{variables('RandomNumber')}&$top=@{variables('NumberOfRecommendations')}| Method | GET |
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
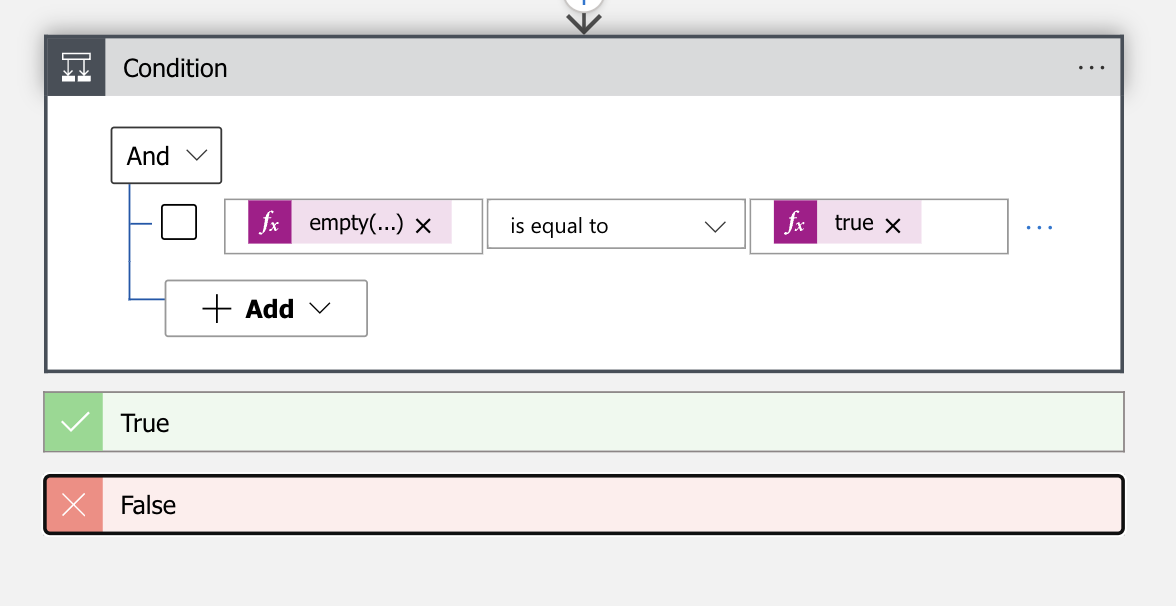
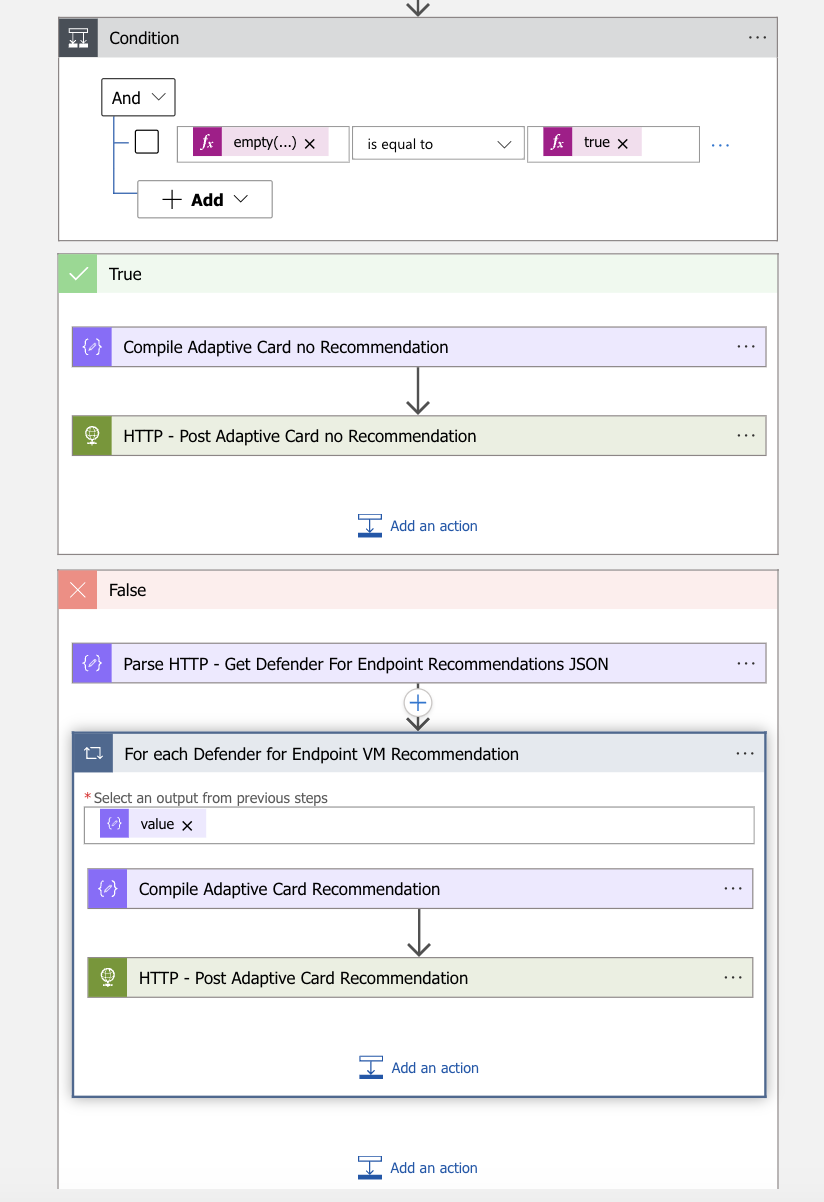
- After the HTTP – Get Defender For Endpoint VM Recommendations action, create a condition action
- set the following condition parameter
empty(body('HTTP_-_Get_Defender_For_Endpoint_VM_Recommendations')?['value']) equals true- Create compose action in the true part of the condition action.
- set the following adaptive card code in the Compile Adaptive Card no Recommendation action
{
"$schema": "http://adaptivecards.io/schemas/adaptive-card.json",
"body": [
{
"bleed": true,
"columns": [
{
"items": [
{
"size": "Medium",
"text": "Defender for Endpoint VM Recommendation",
"type": "TextBlock",
"weight": "Bolder"
},
{
"columns": [
{
"items": [
{
"facts": [
{
"title": "Date:",
"value": "@{formatDateTime(utcNow(), 'yyyy-MM-dd')}"
}
],
"type": "FactSet"
}
],
"type": "Column",
"width": "stretch"
}
],
"type": "ColumnSet"
}
],
"type": "Column",
"width": "stretch"
}
],
"style": "accent",
"type": "ColumnSet"
},
{
"items": [
{
"fontType": "Monospace",
"horizontalAlignment": "Center",
"isSubtle": true,
"size": "Medium",
"spacing": "None",
"style": "columnHeader",
"text": "No recommendation",
"type": "TextBlock",
"weight": "Bolder",
"wrap": true
}
],
"spacing": "Large",
"type": "Container"
},
{
"items": [
{
"spacing": "None",
"text": "fortunately, you have no longer Defender for Endpoint Vulnerabilities Management recommendations",
"type": "TextBlock",
"wrap": true
},
{
"actions": [
{
"title": "Open Microsoft Defender For Endpoint VM",
"type": "Action.OpenUrl",
"url": "https://security.microsoft.com/security-recommendations"
}
],
"type": "ActionSet"
}
],
"type": "Container"
}
],
"msteams": {
"width": "Full"
},
"type": "AdaptiveCard",
"version": "1.5"
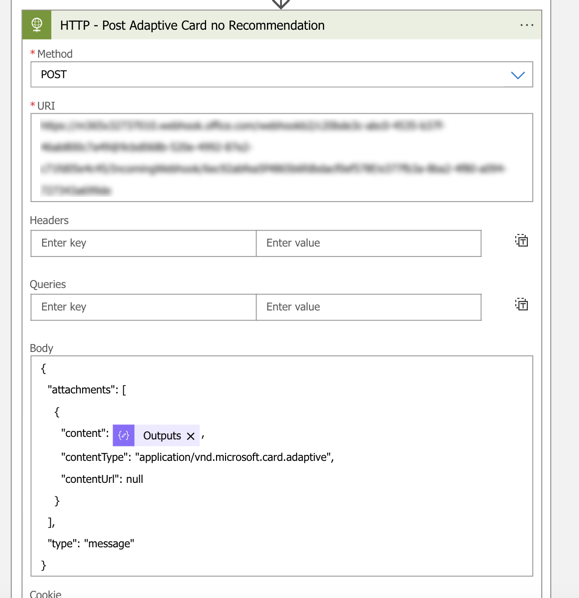
}- The latest step of the true part of the condition is to post the Adaptive Card with no recommendation in Microsoft Teams
- Add a HTTP action set the following configuration
| Method | POST |
| URI | {Webhook URL} |
| Authentication Type | None |
- Use the below code for the body of the HTTP – Post Adaptive Card no Recommendation action
{
"attachments": [
{
"content": @{outputs('Compile_Adaptive_Card_no_Recommendation')},
"contentType": "application/vnd.microsoft.card.adaptive",
"contentUrl": null
}
],
"type": "message"
}- The true part of the condition is now finished, let go move on with the false part
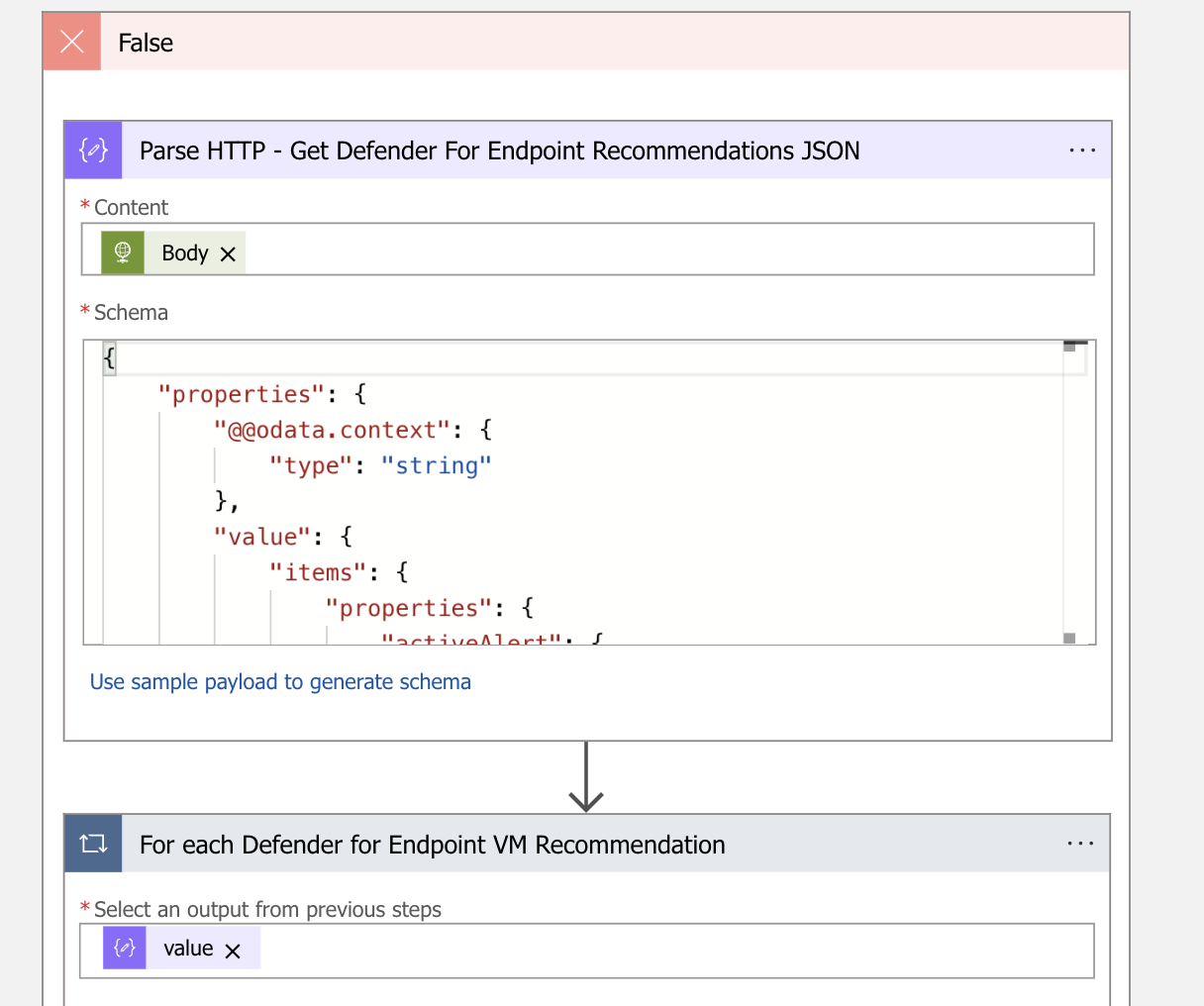
- Create parse JSON with the body of the HTTP – Get Defender For Endpoint VM Recommendations action in the false part of the condition action.
- set the following code in the schema of the Parse HTTP – Get Defender For Endpoint Recommendations JSON
{
"properties": {
"@@odata.context": {
"type": "string"
},
"value": {
"items": {
"properties": {
"activeAlert": {
"type": "boolean"
},
"associatedThreats": {
"items": {
"type": "string"
},
"type": "array"
},
"configScoreImpact": {
"type": "integer"
},
"exposedMachinesCount": {
"type": "integer"
},
"exposureImpact": {
"type": "number"
},
"id": {
"type": "string"
},
"nonProductivityImpactedAssets": {
"type": "integer"
},
"productName": {
"type": "string"
},
"publicExploit": {
"type": "boolean"
},
"recommendationCategory": {
"type": "string"
},
"recommendationName": {
"type": "string"
},
"recommendedVersion": {
"type": "string"
},
"relatedComponent": {
"type": "string"
},
"remediationType": {
"type": "string"
},
"severityScore": {
"type": "integer"
},
"status": {
"type": "string"
},
"subCategory": {
"type": "string"
},
"totalMachineCount": {
"type": "integer"
},
"vendor": {
"type": "string"
},
"weaknesses": {
"type": "integer"
}
},
"required": [
"id",
"productName",
"recommendationName",
"weaknesses",
"vendor",
"recommendedVersion",
"recommendationCategory",
"subCategory",
"severityScore",
"publicExploit",
"activeAlert",
"associatedThreats",
"remediationType",
"status",
"configScoreImpact",
"exposureImpact",
"totalMachineCount",
"exposedMachinesCount",
"nonProductivityImpactedAssets",
"relatedComponent"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
}- After the Parse JSON action, create a For each Defender for Endpoint VM Recommendation loop with the value of the Parse HTTP – Get Defender For Endpoint Recommendations JSON action
- Create compose action in the For each Defender for Endpoint VM Recommendation in the false part of the condition action.
- set the following adaptive card code in the Compile Adaptive Card Recommendation action
{
"$schema": "http://adaptivecards.io/schemas/adaptive-card.json",
"body": [
{
"bleed": true,
"columns": [
{
"items": [
{
"size": "Medium",
"text": "Random recommendation from Defender for Endpoint VM Recommendation",
"type": "TextBlock",
"weight": "Bolder"
},
{
"columns": [
{
"items": [
{
"facts": [
{
"title": "Date:",
"value": "@{formatDateTime(utcNow(), 'yyyy-MM-dd')}"
},
{
"title": "Total:",
"value": "@{variables('TotalRecommendations')} recommendations"
}
],
"type": "FactSet"
}
],
"type": "Column",
"width": "stretch"
}
],
"type": "ColumnSet"
}
],
"type": "Column",
"width": "stretch"
}
],
"style": "accent",
"type": "ColumnSet"
},
{
"items": [
{
"fontType": "Monospace",
"horizontalAlignment": "Center",
"isSubtle": true,
"size": "Medium",
"style": "columnHeader",
"text": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['recommendationName']}",
"type": "TextBlock",
"weight": "Bolder",
"wrap": true
}
],
"spacing": "Large",
"type": "Container"
},
{
"facts": [
{
"title": "Vendor:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['vendor']}"
},
{
"title": "Category:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['recommendationCategory']}"
},
{
"title": "Product:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['productName']}"
}
],
"spacing": "Medium",
"type": "FactSet"
},
{
"facts": [
{
"title": "Public exploit:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['publicExploit']}"
},
{
"title": "Remediation:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['remediationType']}"
},
{
"title": "Total Devices:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['totalMachineCount']}"
}
],
"spacing": "Medium",
"type": "FactSet"
},
{
"facts": [
{
"title": "Weakness Score:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['weaknesses']}"
},
{
"title": "Impact Score:",
"value": "@{items('For_each_Defender_for_Endpoint_VM_Recommendation')?['exposureImpact']}"
}
],
"spacing": "Medium",
"type": "FactSet"
},
{
"actions": [
{
"title": "Open Microsoft Defender For Endpoint VM Portal",
"type": "Action.OpenUrl",
"url": "https://security.microsoft.com/security-recommendations"
}
],
"type": "ActionSet"
}
],
"msteams": {
"width": "Full"
},
"type": "AdaptiveCard",
"version": "1.5"
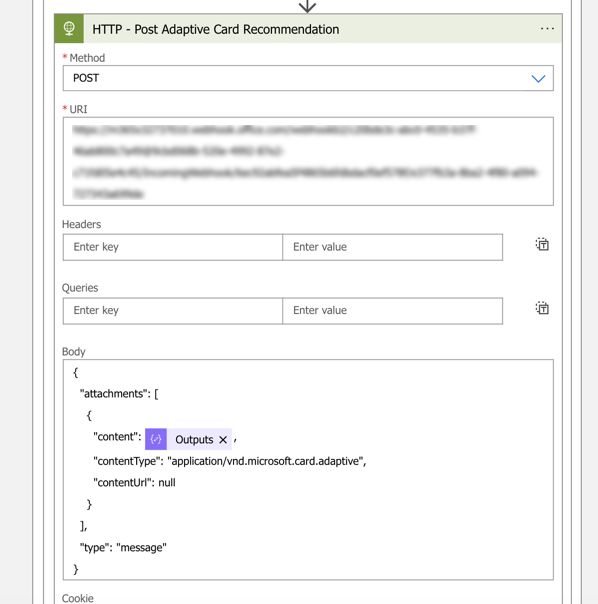
}- The latest step of the false part of the condition is to post the Adaptive Card with the recommendation in Microsoft Teams
- Add a HTTP action set the following configuration
| Method | POST |
| URI | {Webhook URL} |
| Authentication Type | None |
- Use the below code for the body of the HTTP – Post Adaptive Card Recommendation action
{
"attachments": [
{
"content": @{outputs('Compile_Adaptive_Card_Recommendation')},
"contentType": "application/vnd.microsoft.card.adaptive",
"contentUrl": null
}
],
"type": "message"
}

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands. Brian Yurasits
Brian Yurasits Etienne Boulanger
Etienne Boulanger
Leave a Reply
Want to join the discussion?Feel free to contribute!