Newsletter #6 2024
Published on: April 7, 2024
Hi,
First of all, thank you for subscribing and reading the EndpointCave security newsletter.
I feel honored that you will join me on the journey of this bi-weekly Security Newsletter! My goal is to deliver valuable security content directly to you and your inbox.
But I need your help, do you have any valuable content that needs to be shared with the community? Did you create a security blog post or did you find a security-related news item that needs to be mentioned in my upcoming newsletters?
Please send me a message. You can contact me on X (Twitter) or LinkedIn.
The community has created a lot of content. In this newsletter, I reviewed about 217 items, I selected 38 community blogs and 4 videos. I also highlighted the following 5 items:
- License enforcement for Microsoft Purview Information Protection for Sensitivity Labels
- Welcome to the exclusive discovery webinar series on Data Security with Microsoft Purview!
- Microsoft Security Community Webinars
- Microsoft Copilot for Security is now generally available
- Most of the Microsoft Defender XDR and SIEM products and capabilities
Enjoy
Highlights
License enforcement for Microsoft Purview Information Protection for Sensitivity Labels
Welcome to the exclusive discovery webinar series on Data Security with Microsoft Purview!
𝐒𝐞𝐬𝐬𝐢𝐨𝐧 1
Apr 4, 11:00 – 11:30 AM (GMT+01:00)
In this session, Jan Willem and Anela will show how Office Messages Encryption and Do not Forward functionalities work!
Register here: You have missed this session already
𝐒𝐞𝐬𝐬𝐢𝐨𝐧 2
Apr 11, 11:00 – 11:30 AM (GMT+01:00)
In this session, Jan Willem and Anela will show how to protect your information with sensitivity labels, how encryption works, how to collaborate with external users, and how Data Loss Prevention works.
Register here: Microsoft Event
𝐒𝐞𝐬𝐬𝐢𝐨𝐧 3
Apr 18, 11:00 – 11:30 AM (GMT+01:00)
In this session, Jan Willem and Anela will show how to use Data Lifecycle Management to protect files and e-mails from accidental deletion. And you will find out how to find those files when the end-user cannot find them anymore.
Register here: Microsoft Event
𝐒𝐞𝐬𝐬𝐢𝐨𝐧 4
Apr 25, 11:00 – 11:30 AM (GMT+01:00)
In this session, Jan Willem and Anela will show how to migrate to the cloud. We will discuss what to do with all the data you have on-prem, how to classify it, and how to decide what data to migrate to the cloud. In this episode, you will learn more about the AIP scanner and Microsoft Purview data classification.
Register here: Microsoft Event
Microsoft Security Community Webinars
APR 11 Microsoft Defender Threat Intelligence | TI at Machine Speed: Using MDTI in Copilot for Security
APR 16 Microsoft Defender for Cloud | Defender CSPM Planning, Operationalization and Best Practices
APR 18 Microsoft Sentinel | What’s New in Microsoft Sentinel & Unified Portal Enhancements
APR 23 Azure Network Security | Building a DDoS Response Plan
APR 23 Microsoft ITDR | POCaaS Session 1: ITDR Introduction and Prevention Capabilities
APR 24 Microsoft ITDR | POCaaS Session 2: Detection
APR 25 Microsoft Defender for Cloud | Defender CSPM Internet Exposure Analysis
APR 30 Microsoft ITDR | POCaaS Session 3: Investigation and Hunting
MAY 1 Microsoft ITDR | POCaaS Session 4: Response
May 2 Microsoft Sentinel | Splunk to Microsoft Sentinel Migration Experience
MAY 16 Azure Network Security | Updating Your Azure Web Application Firewall Ruleset: Common Pitfalls and How to Avoid Them
May 21 Microsoft Sentinel | Optimizing Your Security Operations: Manage Your Data, Costs and Protections with SOC Optimizations in Microsoft Sentinel
MAY 22 Microsoft Defender for Cloud | Simplifying Servers Security in Microsoft Defender for Cloud
JUN 4 Microsoft Sentinel | Log Everything with Log Analytics Multi-Tier Capabilities
JUN 12 Azure Network Security | What’s New in Azure Firewall
JUN 13 Microsoft Defender for Cloud | Shift Left with Microsoft Defender for Cloud
JUN 20 Microsoft Defender for Cloud | Elevate Cloud Security Using Permissions Management in Microsoft Defender for Cloud
Microsoft Copilot for Security is now generally available
Microsoft Copilot for Security is the first generative AI security product that empowers security and IT teams to protect at the speed and scale of AI. As announced at Microsoft Secure last month, Copilot for Security is now available for purchase as of April 1, 2024. Customers can get started by provisioning capacity to run all Copilot workloads, both for standalone and for those embedded in our security products beginning with Microsoft Defender XDR.
More information about Microsoft Copilot for Security:
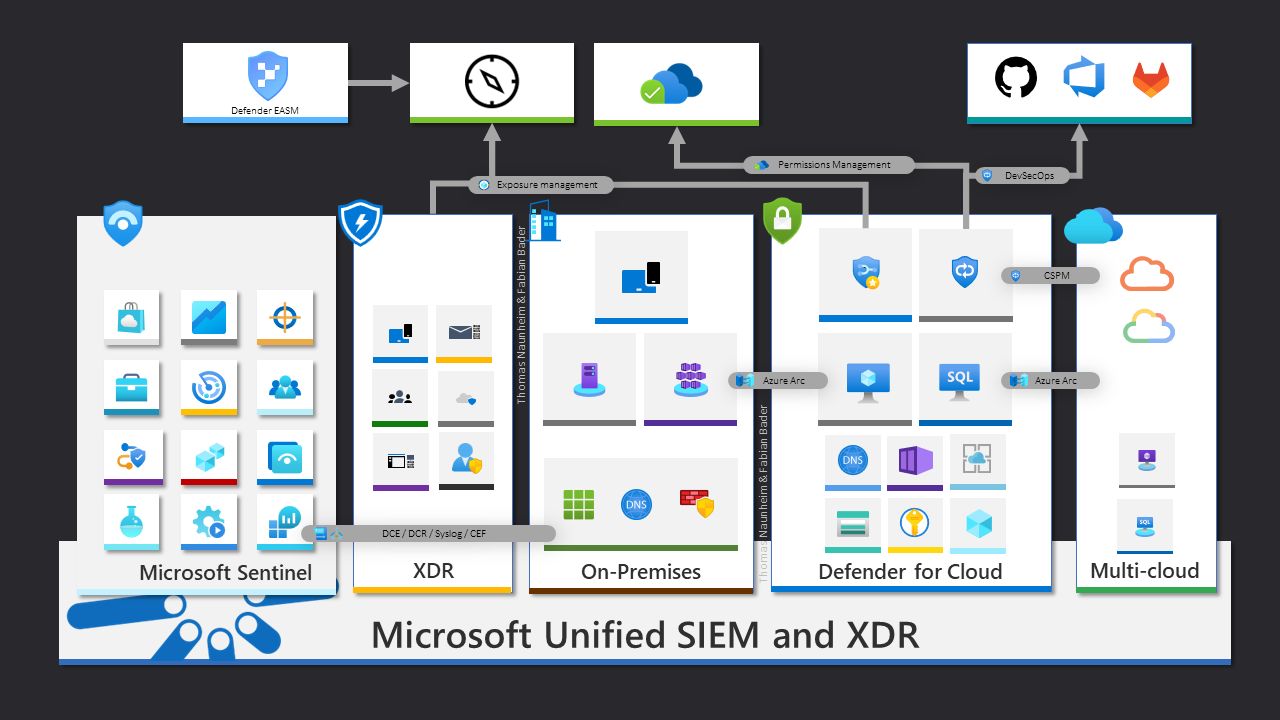
Most of the Microsoft Defender XDR and SIEM products and capabilities
Fabian Bader and Thomas Naunheim created an overview of most of the Microsoft Defender XDR and Microsoft SIEM products and capabilities.
With the announcement of the new “Unified SIEM and XDR” last year at Ignite and the public preview of security exposure management we recently updated it to reflect the new integration possibilities.
Security topics to watch
How hackers are breaking into MFA enabled Microsoft 365 accounts
How do attackers break into MFA-enabled Microsoft 365 accounts? Check out how the attack works, and what we’re doing to stop it using tools including HuskyHacks’ Clarion
Entra ID New Features That You Simply MUST Know!
In this episode, Andy will bring you up to date in the world of Microsoft Entra ID including news of some recently released features along with a look at what they can do. Andy will take a look at enhancements in conditional access, including new Insider Risk settings, passkey support, and authentication flows. So if you’re keen to learn this is one session that you should not miss out on.
Sentinel Analytic Rules Management Script
In this video, Stefano will explain what the Sentinel Analytic Rules Management Script (https://aka.ms/sarms) can do and how it can be used. He also shows how the script code is organized. Finally, He provided a fairly comprehensive demo of using the script for its different features.
Protecting Your Data from Malicious Actors: The Importance of Compliance!
Discover why compliance is crucial in safeguarding your data from ransomware, encryption, and unauthorized access. Stay ahead of evolving threats and learn how malicious actors are leveraging AI. Protect your device and identity with effective security measures
Blogs from the community
This is the end of this newsletter. Thank you for reading the Endpoint Security newsletter, I hope you have found valuable content that you can use.
Do you have any feedback? Please feel free to share your thoughts and suggestions with me for future editions. Any valuable content of blogs that I need to monitor or share. Please send me a message. You can contact me on X (Twitter) or LinkedIn.
Kind Regards,
René Laas – MVP
EndpointCave

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
