Newsletter #5 2024
Published on: March 24, 2024
Hi,
First of all, thank you for subscribing and reading the EndpointCave security newsletter.
I feel honored that you will join me on the journey of this bi-weekly Security Newsletter! My goal is to deliver valuable security content directly to you and your inbox.
But I need your help, do you have any valuable content that needs to be shared with the community? Did you create a security blog post or did you find a security-related news item that needs to be mentioned in my upcoming newsletters?
Please send me a message. You can contact me on X (Twitter) or LinkedIn.
The community has created a lot of content. In this newsletter, I collected and reviewed in the past 4 weeks about 450 items, I selected 46 community blogs and 5 videos. I also highlighted the following items
- 7 Lessons, Kick-start Your Cybersecurity Learning
- Microsoft Copilot & Microsoft Copilot for Security information
- Monitor Microsoft Power Platform with Microsoft Sentinel
- NIST Releases Version 2.0 of Landmark Cybersecurity Framework
- What’s new in Microsoft Entra ID?
Enjoy
Highlights
7 Lessons, Kick-start Your Cybersecurity Learning
In this rapidly changing age of AI technology adoption, it is even more critical to understand how to secure IT systems. This course is designed to teach you fundamental cybersecurity concepts to kick-start your security learning. It is vendor-agnostic and is divided into small lessons that should take around 30-60 mins to complete. Each lesson has a small quiz and links to further reading if you want to dive into the topic a bit more.
More information: Click here
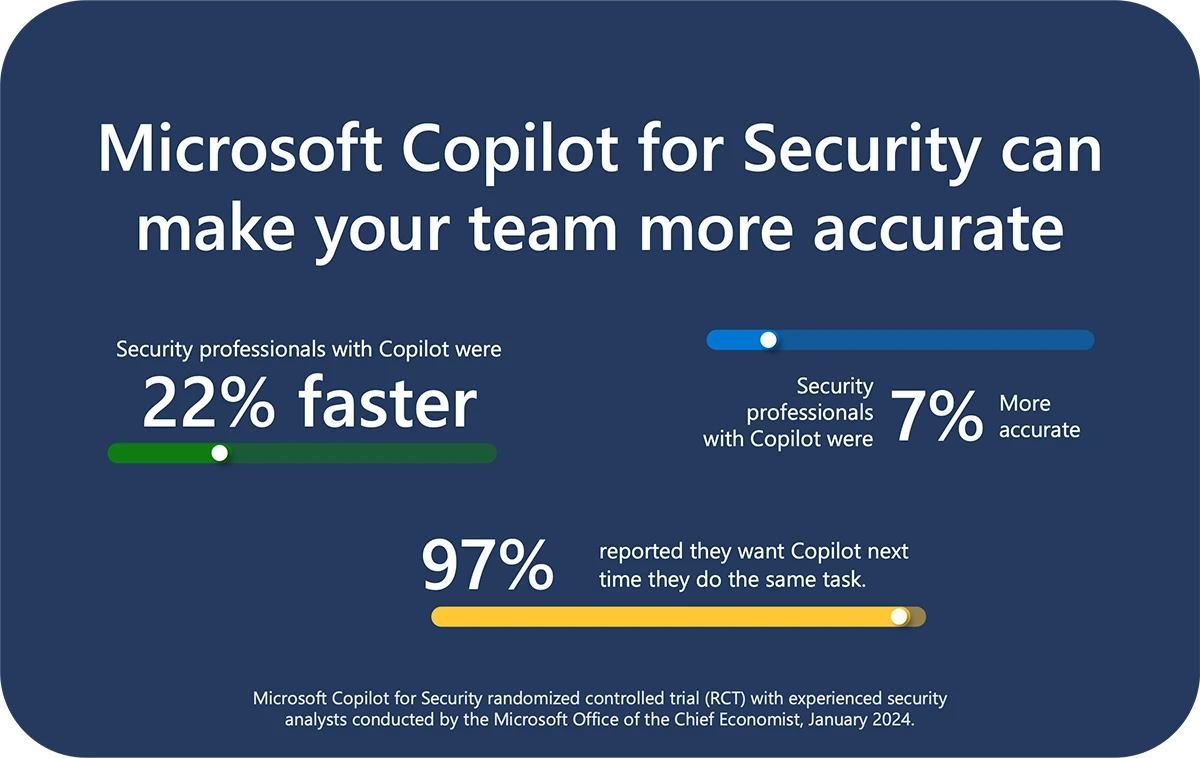
Microsoft Copilot for Security: General Availability details
The emergence of GenAI is changing the world as we know it. This ‘once in a generation’ technology leap is already helping defenders see more and move faster, complementing human ingenuity and expanding our capabilities to protect beyond what was possible yesterday.
To help you seize this opportunity, Microsoft is excited to announce the general availability of Microsoft Copilot for Security (Copilot) on April 1st. This industry-leading product is the only generative AI solution that helps security and IT professionals amplify their skills, collaborate more, see more, and respond faster.
Read more about the GA of Security Copilot
Check out the following blog post for more information about Microsoft Copilot.
- Protect at the speed and scale of AI with Copilot for Security in Microsoft Purview
More information: Click here
- Copilot for Security Prompt Samples, Templates, and Promptbooks
More information: Click here
- Apply principles of Zero Trust to Microsoft Copilot for Microsoft 365
More information: Click here
- Microsoft Copilot for Microsoft 365 – best practices with SharePoint
More information: Click here
Monitor Microsoft Power Platform with Microsoft Sentinel
The Microsoft Sentinel solution for Power Platform allows you to monitor and detect suspicious or malicious activities in your Power Platform environment. The solution collects activity logs from different Power Platform components and inventory data.
Check out the following Microsoft documentation to get started with monitoring your Microsoft Power Platform environment.
- Deploy the Microsoft Sentinel solution for Microsoft Power Platform
More information: Click here
- Microsoft Sentinel solution for Microsoft Power Platform: security content reference
More information: Click here
- Microsoft Sentinel solution for Microsoft Power Platform overview
More information: Click here
NIST Releases Version 2.0 of Landmark Cybersecurity Framework
The National Institute of Standards and Technology (NIST) has updated the widely used Cybersecurity Framework (CSF), its landmark guidance document for reducing cybersecurity risk. The new 2.0 edition is designed for all audiences, industry sectors, and organization types, from the smallest schools and nonprofits to the largest agencies and corporations — regardless of their degree of cybersecurity sophistication.
More information: Click here
What’s new in Microsoft Entra ID?
- General Availability – Identity Protection and Risk Remediation on the Azure Mobile App
More information: Click here - General Availability – New premium user risk detection, Suspicious API Traffic, is available in Identity Protection
More information: Click here
And a lot of other features have become available. For the list of new features check out this page
Security topics to watch
Block Personal Computers with Conditional Access in Microsoft 365
Wouldn’t it be great to just simply block the use of personal computers in Microsoft 365? This would mean that access to Microsoft 365 could only be done on company-owned devices that were part of Intune. You can do this by using a conditional access policy and Jonathan will show you in this video.
Search for & delete M365 Copilot Data with Microsoft Purview eDiscovery Premium
In this video, Peter delves into the powerful capabilities of Microsoft Purview eDiscovery Premium and how it can be used to search for and delete M365 Copilot data.
Securing Your Office 365 Before Activating Microsoft 365 Copilot
Before you dive into the exciting world of Microsoft 365 Copilot, it’s crucial to lay down a rock-solid security foundation. In this video, Peter will walk you through the essential steps to ensure your environment is fortified and ready for Copilot.
Optimizing your SOC’s threat coverage and data value
Senior Product Manager Michal Shechter is with us to introduce SOC optimization, an exciting new feature designed to offer security operations center (SOC) teams’ valuable recommendations for enhancing their environment. The focus is on data value and threat coverage, with the possibility to expand into other categories in the future. Join us as we unveil compelling topics, including ensuring accurate data ingestion into your security information and event management system, optimizing data ingestion and costs, and ensuring comprehensive coverage against pertinent threats.
Bypassing windows defender | Malware development
In this video, Hicham will showcase how to bypass Windows Defender by getting a reverse shell that was created in C++ from GitHub and making it undetectable based on what we have learned in the video. we are going to learn about Windows internals, Windows API functions, how to use socket library, how Windows Defender works, how obfuscation works, what is obfuscation
Blogs from the community
This is the end of this newsletter. Thank you for reading the Endpoint Security newsletter, I hope you have found valuable content that you can use.
Do you have any feedback? Please feel free to share your thoughts and suggestions with me for future editions. Any valuable content of blogs that I need to monitor or share. Please send me a message. You can contact me on X (Twitter) or LinkedIn.
Kind Regards,
René Laas – MVP
EndpointCave

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands. Andrea De Santis
Andrea De Santis