Newsletter #1 2024
Published on: January 14, 2024
Hi,
First of all, thank you for subscribing and reading the EndpointCave security newsletter.
I feel honored that you will join me on the journey of this bi-weekly Security Newsletter! My goal is to deliver valuable security content directly to you and your inbox.
But I need your help, do you have any valuable content that needs to be shared with the community? Did you create a security blog post or did you find a security-related news item that needs to be mentioned in my upcoming newsletters?
Please send me a message. You can contact me on Twitter (X) or LinkedIn.
2023 was a wonderful year, but also a busy one. I created for the community 7 security newsletters, spoke at 2 public events, recorded 4 podcasts, and wrote 19 blogs.
So I decided to take some rest and visit New York City and a small city in Germany. This was a great contrast between the two different cities and countries. But now I am back with full of energy and a lot of inspiration.
The year 2024 could not have started better for me. I have been awarded as an MVP. What an honor to be part of this group of passionate Microsoft IT Professionals.
The community has created a lot of content. In this newsletter, I selected 36 community blogs and 7 videos. I also highlighted the following items:
- 28835 CVEs were published last year
- Become a Microsoft Unified SOC Platform Ninja
- Activate eligible PIM roles via Microsoft Graph and PowerShell
- New ITDR Dashboard in Microsoft Defender XDR
Enjoy
Highlights
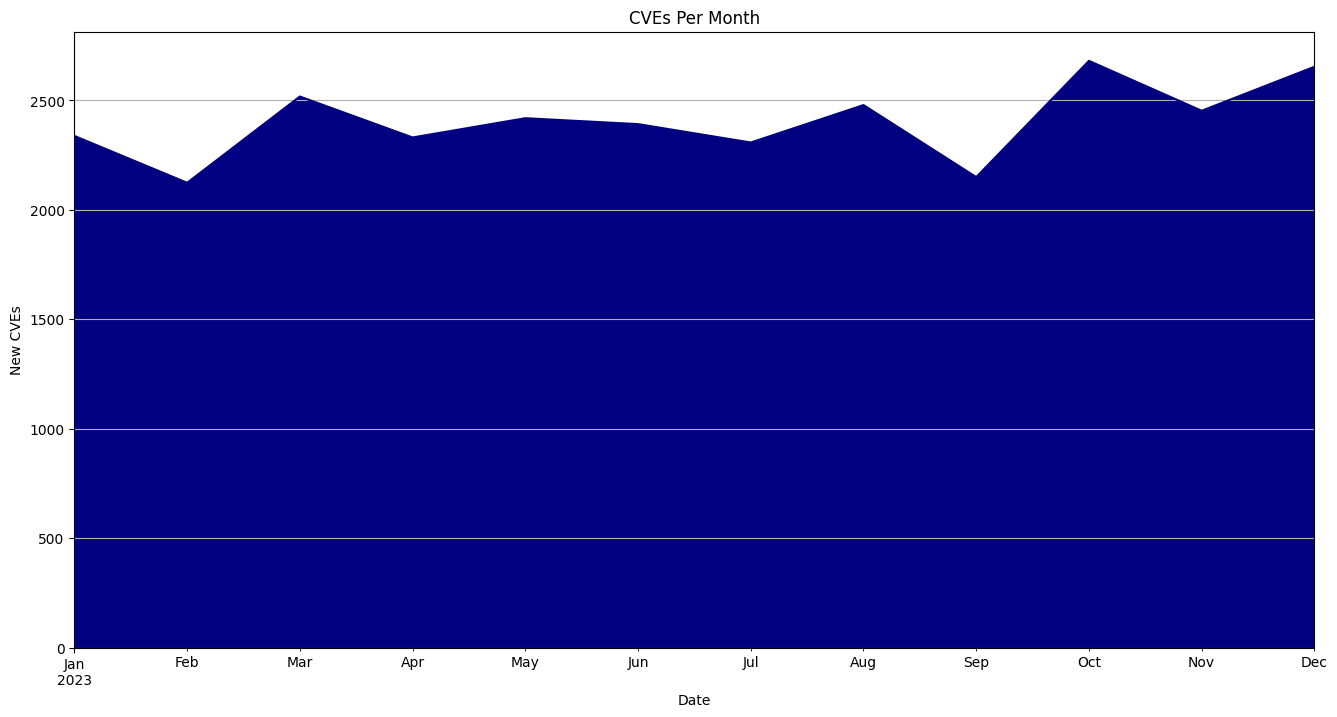
28835 CVEs were published last year
Total Number of CVEs: 28835
Average CVEs Per Day: 79.0
Average CVSS Score: 7.13
More information: Click here
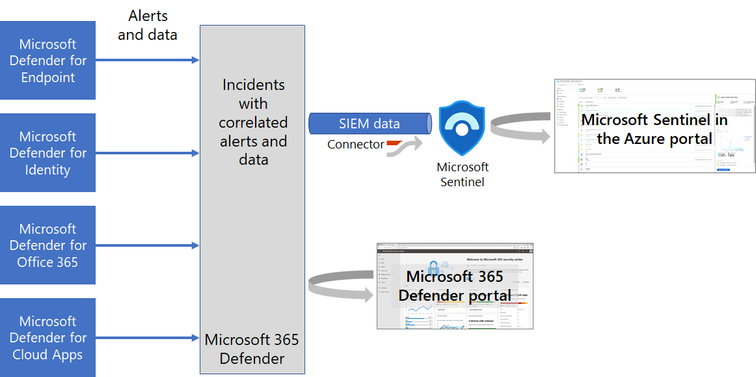
Become a Microsoft Unified SOC Platform Ninja
What is happening to Microsoft Sentinel and Defender XDR?
Microsoft is bringing the Microsoft Defender products together to deliver the most optimized and unified security operations platform. This experience will combine the full power of Microsoft Sentinel with Microsoft Defender XDR into a single portal enhanced with more comprehensive features, AI, automation, guided experiences, and curated threat intelligence. Customers will enjoy a fully integrated toolset to protect, detect, investigate, and respond to threats across every layer of digital estate.
Microsoft has been on a mission to empower security operations teams by unifying the many tools essential for protecting a digital estate and delivering them into an effective solution driven by AI and automation.
To become a Microsoft Unified SOC Platform Ninja, you must follow this training.
More information: Click here
Activate eligible PIM roles via Microsoft Graph and PowerShell
This script activates eligible Privileged Identity Management (PIM) roles for the current user using Microsoft Graph API.
It retrieves the eligible roles for the user and then activates each role with a specified duration and justification.
So this PowerShell script can be super handy for developers who work a lot with PowerShell and need to activate their permissions via PIM. With this script, you don’t have to log on to the portal anymore to activate your admin rights.
More information: Click here
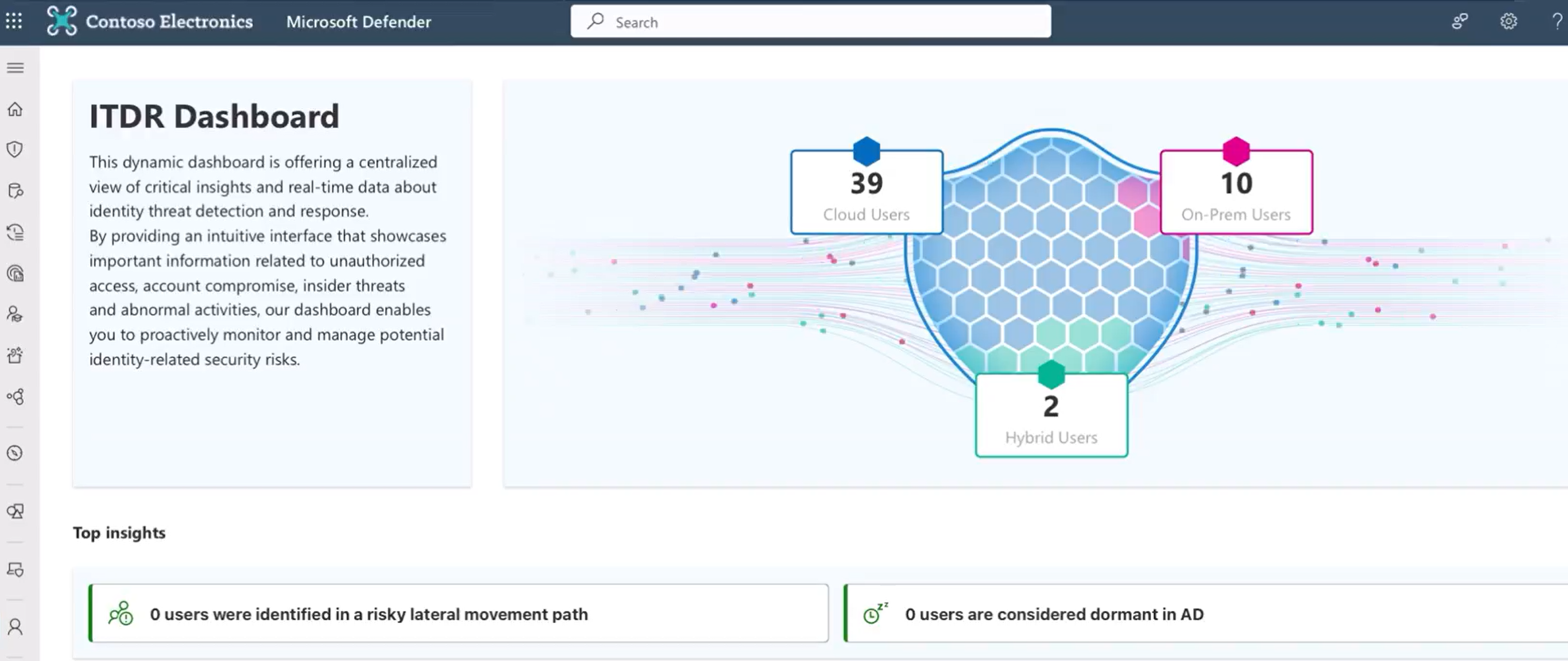
New ITDR Dashboard in Microsoft Defender XDR
This dynamic dashboard is offering a centralized view of critical insights and real-time data about identity threat detection and response. By providing an intuitive interface that showcases important information related to unauthorized access, account compromise, insider threats, and abnormal activities, our dashboard enables you to proactively monitor and manage potential identity-related security risks.
More information: Click here
Security topics to watch
Microsoft Defender for Identity Inc FULL DEMO
In this episode, Andy takes a deep dive into Microsoft Defender for Identity. Including a full demo on how to set it up and configure it. He will also show a demo of an Advisory In the Middle Attack AiTM and demonstrate how Microsoft’s XDR platform can not only detect these attacks but also how AI & machine learning can help thwart such attacks by undertaking a constant behavioral analysis of every user and their login attempts. This is a session packed with demos, so if you’re preparing for certification or simply looking to learn. Then this will be an invaluable session for you.
Level up your identity protection: Building an ITDR practice for modern business
Attackers don’t break in, they log in. Get an in-depth look at Microsoft’s point of view on identity threat detection and response (ITDR). Identities have become the new corporate security boundary and protecting your organization against these evolving threats requires a comprehensive strategy spanning capabilities both pre- and post-breach. Join this session for a detailed look at how we can help you implement comprehensive Identity protection across your unique identity landscape.
Understanding the Microsoft Cybersecurity Reference Architectures!
In this video, Peter takes a walkthrough of the Microsoft Cybersecurity Reference Architectures, which are an absolutely essential resource for any organization looking to implement their end to end Cybersecurity strategy in line with the principles of Zero Trust
Microsoft Sentinel All In One – A complete Deployment Guide!
In this video, Peter looks at how the wonderful GitHub Microsoft Sentinel All-in-one Deployment tool works. This simplifies the process of setting up a Microsoft Sentinel Instance for you, allowing you to customize the connectors and settings you want and have everything you need setup using one powerful wizard!
Conditional Access Filters and Templates
A dive into the recent filtering and template capability of Conditional Access.
How to onboard Macs to Microsoft Defender for Endpoint
If you need to, return all your gifts. Also, let’s get those Macs onboarded into Defender for Endpoint.
Understanding Microsoft Entra Protected Actions
Understanding Microsoft Entra Protected Actions In this video John is going to introduce you to Microsoft Entra Protected Actions and show how they can be used to trigger the evaluation of Conditional Access policies when a particular task is performed within the directory.
This allows you to specify additional security measures when an administrator executes a specific task. This video is demo-orientated and he will show you how a conditional access administrator, can view policies from anywhere. But only create/update/delete a policy when working from the London office.
Blogs from the community
This is the end of this newsletter. Thank you for reading the Endpoint Security newsletter, I hope you have found valuable content that you can use.
Do you have any feedback? Please feel free to share your thoughts and suggestions with me for future editions. Any valuable content of blogs that I need to monitor or share. Please send me a message. You can contact me on Twitter (X) or LinkedIn.
Kind Regards,
René Laas – MVP
EndpointCave

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands. Jon Tyson
Jon Tyson