Auto Assign Scope Tags Based on User Location
The purpose of this blog post is to inform you how to assign device scope tags via the assigned user his/her Azure AD attribute Company and thus his/her user location, which can be used for configuring RBAC
Companies with locations in different countries often also have local IT support at these locations. Those local IT support engineers are only allowed to manage their devices. The Intune Administrator role has access to all devices, so we must configure Intune RBAC to scope their access to see only their devices.
In this blog post, I will use an Azure Logic App to assign the device scope tag based on the assigned user its Company attribute in AAD. This solution can also be built via a Power Automate Flow.
Requirements:
Graph API requirements:
What is RBAC?
Role-based access control (RBAC) helps you to manage who has access to your Intune tenant and their access rights. Each Intune role has a set of permissions that determine what users with that role can access and change within your tenant.
More information about Intune RBAC can be found here
What are Scope Tags?
You can use RBAC to set the needed access rights for a user, but this is for all objects in your tenant. With scope tags, you can scope the admins to have the right access and visibility to the right Intune objects.
The RBAC Roles determine what access admins have to which objects. Scope tags determine which objects admins can see and manage.
More information about Scope tags can be found here
What is an Azure Logic App?
Azure Logic Apps is a cloud service that helps you schedule, automate, and orchestrate tasks, business processes, and workflows when you need to integrate apps, data, systems, and services across enterprises or organizations.
More information about Azure Logic Apps can be found here
Create an App Registration in Azure AD
- Open azure.com
- Click on Azure Active Directory
- Click on App Registrationin the left menu
Or use the following link Active Directory | App Registration
- Click on + New registration
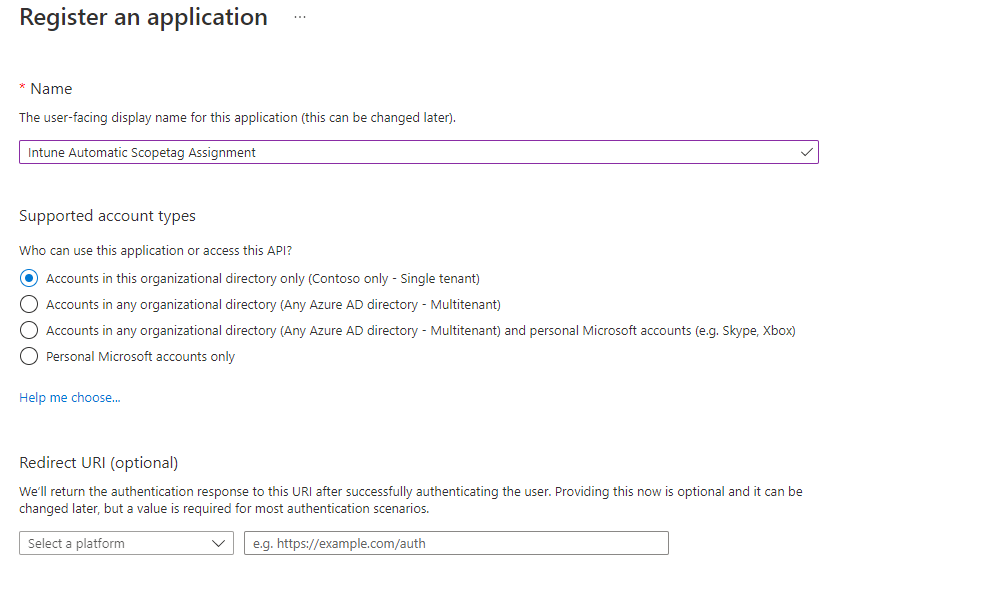
- Configure an app name
- Click on the Register button, the app will be created and automatically opened.
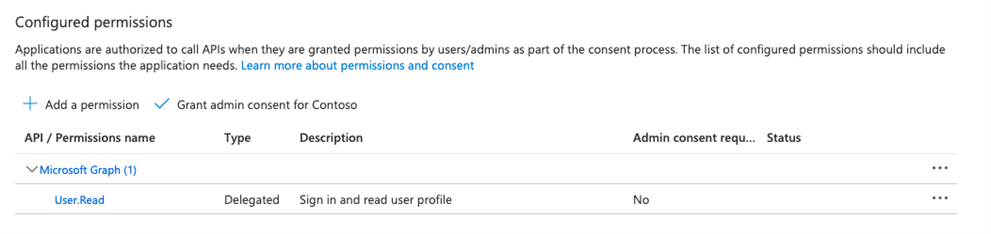
- In the menu click on API Permissions
- Click on+ Add a permission
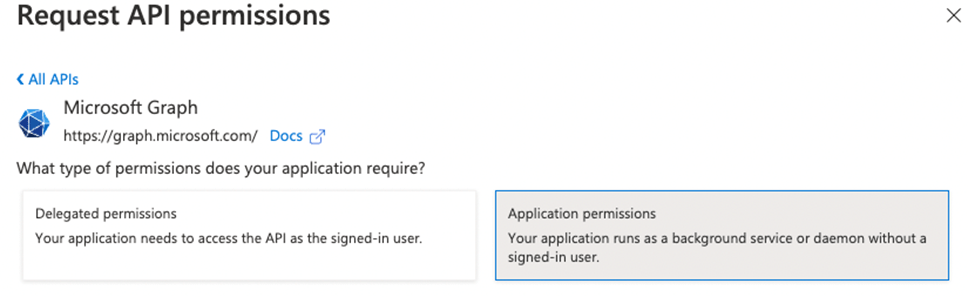
- Select Microsoft Graph and select Application permissions
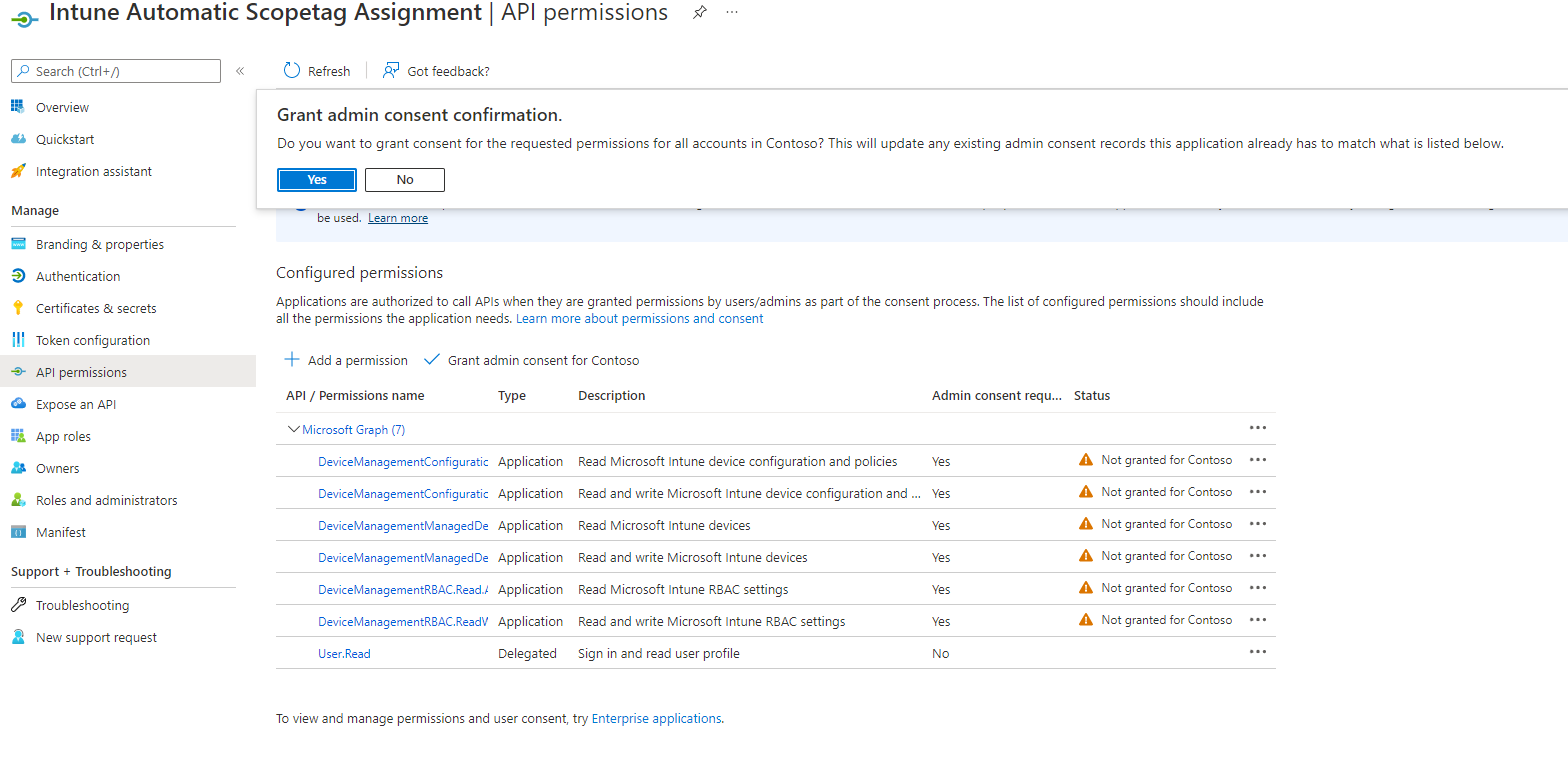
- Search and add the following permissions
DeviceManagementConfiguration.Read.All
DeviceManagementConfiguration.ReadWrite.All
DeviceManagementManagedDevices.Read.All
DeviceManagementManagedDevices.ReadWrite.All
DeviceManagementRBAC.Read.All
DeviceManagementRBAC.ReadWrite.All- Grant admin consent for your organization
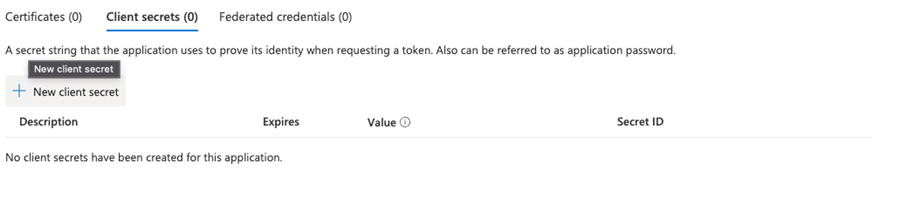
- In the menu click on Certificates & Secrets
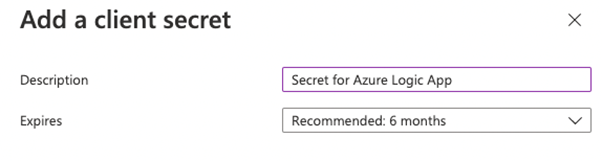
- Click on + New Client secret
- Set a description and the expiry of the secret and click on Add
- Copy the value of the secret, the secret is needed for the flow.
- Go to the overview page and copy the Client ID and Tenant ID, those are also needed in the flow.
Create a scope tag
- Open endpoint.microsoft.com
- Click on Tenant administration
- Click on Roles
- Click on Scope (Tags) in the menu
Or use the following link: Endpoint Manager roles – Microsoft Endpoint Manager admin center - Click on + Create
- Create the required scope tags for your organization e.g.:
| Name | Netherlands | Germany |
| Description | All Dutch devices | All German devices |
| Assignment | – | – |
Create an Azure Logic App for the Conditional Access changes notifications
Note. Rename every Azure Logic App action to match the screenshots!
- Open portal.azure.com
- Search for Logic App
- Click on + Add
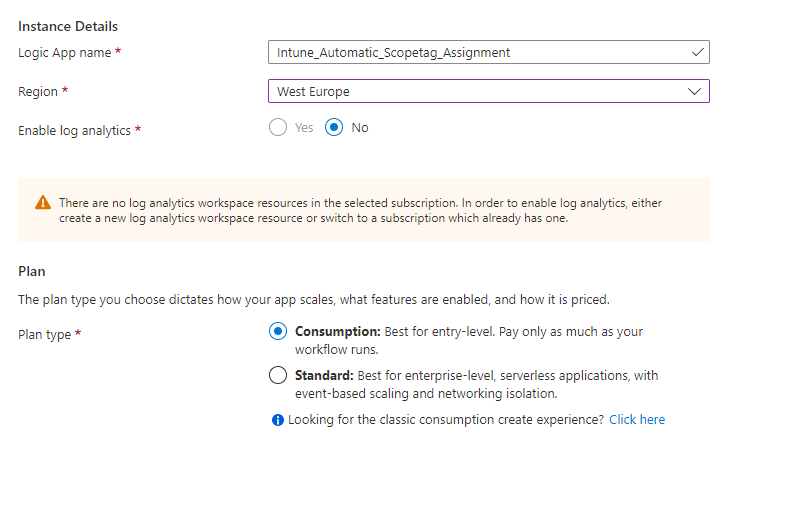
- Select an existing Resource Group or create a new Resource Group
- Select the instance Type (I have chosen for Consumption, but check the Azure Calculator which option fits your environment)
- Select your region and click on Review + Create
- Check the details on the Review + Create page and click on Create
- After the deployment is completed, go to your new Logic App via Go to Resource button
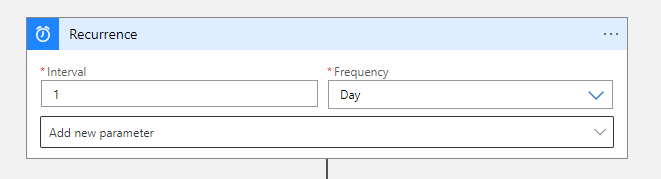
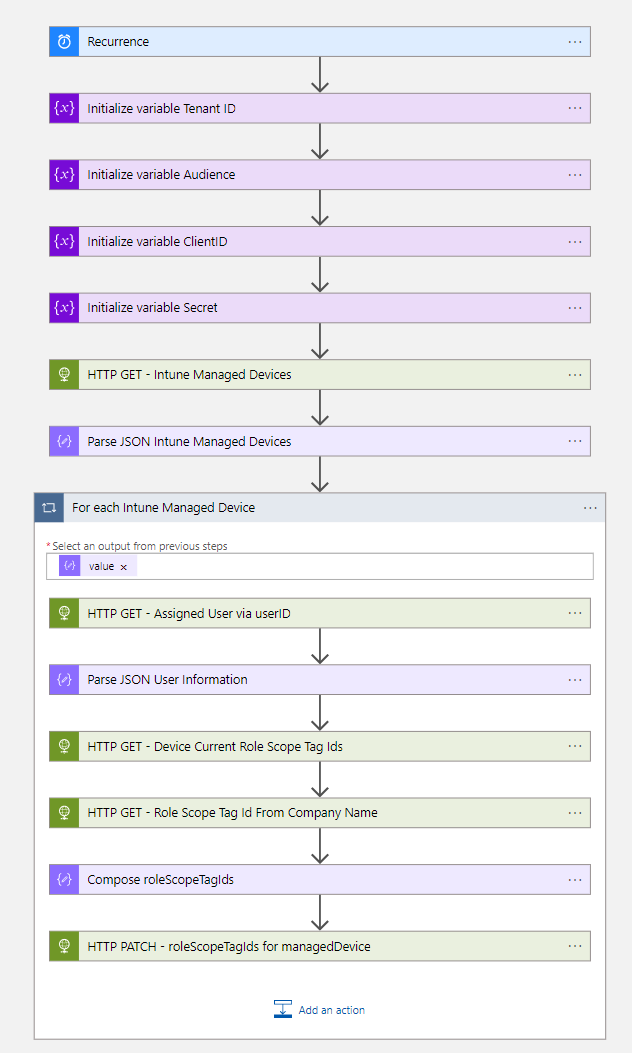
- The first step of the workflow is the Recurrence trigger, based on the desired interval
Note. I have used a 1-day interval in this blog.
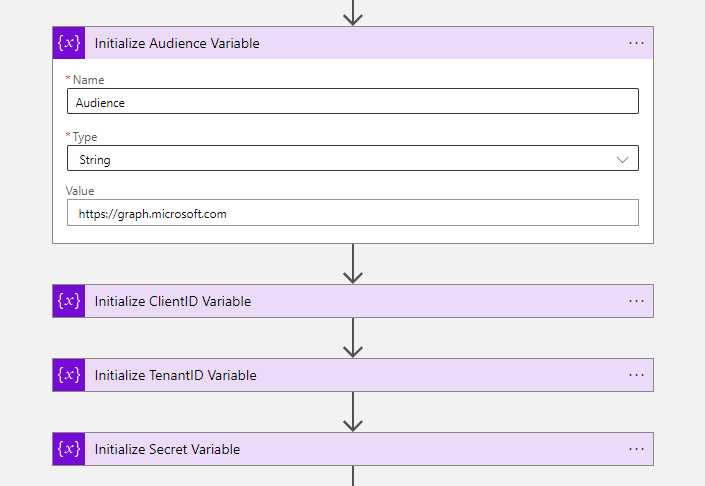
- The next four steps of the workflow are to initialize variables.
| Initialize Audience Variable | Initialize TenantID Variable | Initialize ClientID Variable | Initialize Secret Variable | |
|---|---|---|---|---|
| Name | Audience | ClientID | TenantID | Secret |
| Type | String | String | String | String |
| Value | https://graph.microsoft.com | {Paste your Tenant ID} | {Paste your Client ID} | {Paste your Secret} |
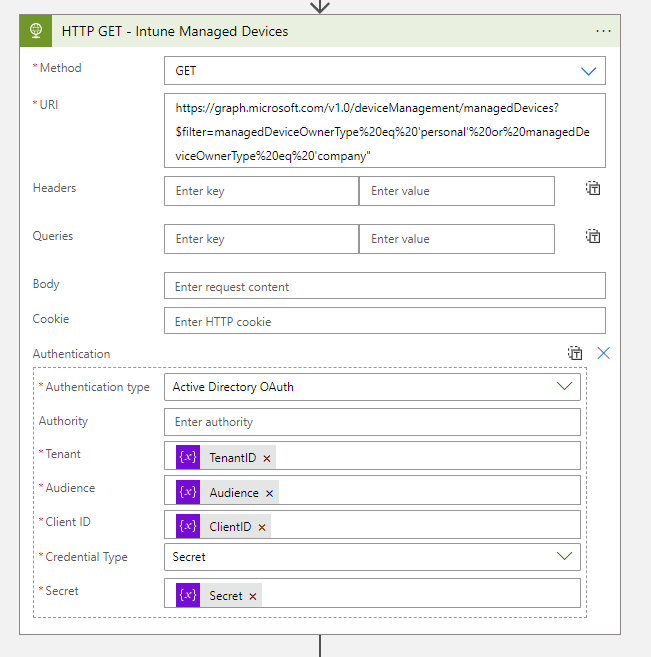
- The next step is to Get all Intune Managed devices via an HTTP Get request
| Method | GET |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
- URI:
https://graph.microsoft.com/v1.0/deviceManagement/managedDevices?$filter=managedDeviceOwnerType%20eq%20'personal'%20or%20managedDeviceOwnerType%20eq%20'company"- Now we must parse the body of the HTTP action to get the required information as a variable
{
"properties": {
"value": {
"items": {
"properties": {
"deviceCategoryDisplayName": {
"type": "string"
},
"deviceName": {
"type": "string"
},
"id": {
"type": "string"
},
"userDisplayName": {
"type": "string"
},
"userId": {
"type": "string"
},
"userPrincipalName": {
"type": "string"
}
},
"required": [
"id",
"userId",
"deviceName",
"deviceCategoryDisplayName",
"userPrincipalName",
"userDisplayName"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
}- Create a for each loop, with the value variable from the parse action
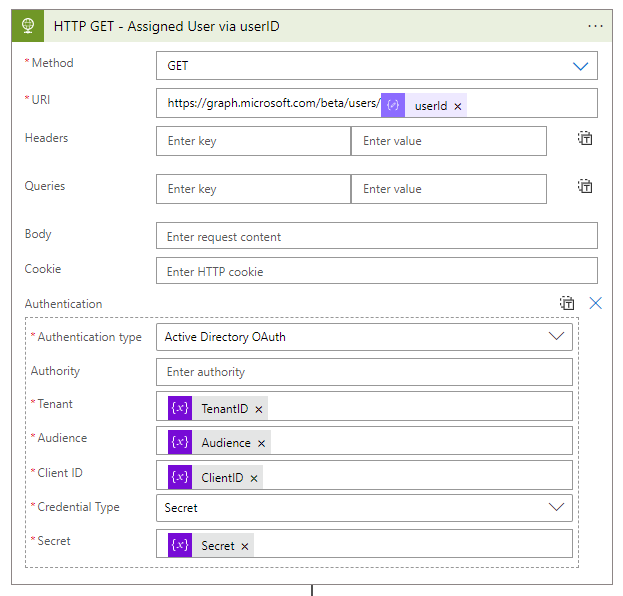
- In the for each loop, we create an HTTP action to get the assigned user.
| Method | GET |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
- URI:
https://graph.microsoft.com/beta/users/@{items('For_each_Intune_Managed_Device')?['userId']}- Now we must parse the body of the HTTP action to get the user information as a variable
{
"properties": {
"@@odata.context": {
"type": "string"
},
"companyName": {
"type": "string"
},
"id": {
"type": "string"
},
"userPrincipalName": {
"type": "string"
}
},
"type": "object"
}- The next step is to get the current role scope via an HTTP action
| Method | GET |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
- URI:
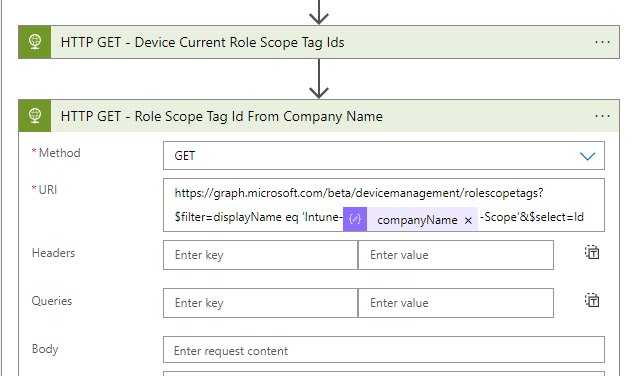
https://graph.microsoft.com/beta/devicemanagement/managedDevices/@{items('For_each_Intune_Managed_Device')?['id']}?$select=roleScopeTagIds- Now we have the current scope tag, now we must get the scope tag based on the company name of the user. This will also be done via an HTTP action
| Method | GET |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
- URI:
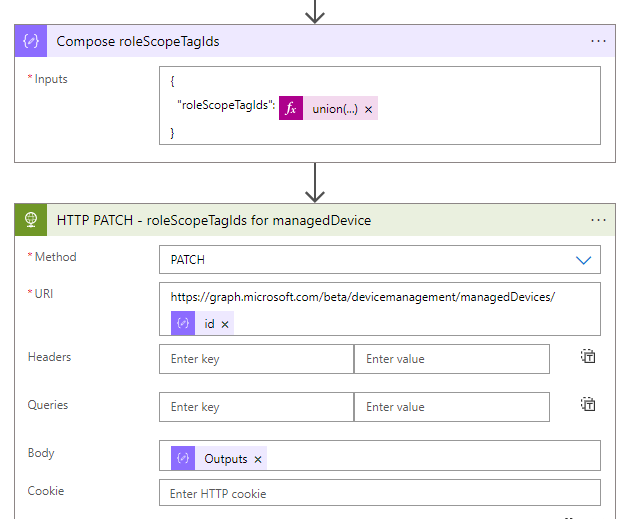
https://graph.microsoft.com/beta/devicemanagement/rolescopetags?$filter=displayName eq 'Intune-@{body('Parse_JSON_User_Information')?['companyName']}-Scope'&$select=Id- We have the required information, let’s compose the right role scope tag.
{
"roleScopeTagIds": @{union(array(body('HTTP_GET_-_Device_Current_Role_Scope_Tag_Ids')?['roleScopeTagIds']),array(body('HTTP_GET_-_Role_Scope_Tag_Id_From_Company_Name')?['value'][0]?['Id']))}
}- The final step of the Logic App is an HTTP action, to set the right role scope tag for the device
| Method | GET |
|---|---|
| Authentication Type | Active Directory OAuth |
| Tenant | @{variables(‘TenantID’)} |
| Audience | @{variables(‘Audience’)} |
| Client ID | @{variables(‘ClientID’)} |
| Credential Type | Secret |
| Secret | @{variables(‘Secret’)} |
- URI:
https://graph.microsoft.com/beta/devicemanagement/managedDevices/@{items('For_each_Intune_Managed_Device')?['id']}- Save the Logic App and Click on Run Trigger





 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.

thanks. i intend to try this to auto assign scope tag to intune devices based on enrolled user’s extensionattribute and country. i read that you mentioned it can be done using power automate too. could you share with me on how to create it using power automate please? thanks
Hi Jeff,
yes, it is possible with PowerAutomate, but you need a PowerPlatform P2 license because the flow will use multiple HTTP premium connectors. All actions are exactly the same in PowerAutomate except for the for each loop, you should use the apply to each action in PowerAutomate.
Good luck, if you have questions. Please let me know.
Kind regards,
Rene