Enforce MFA on Windows logon with Intune and Duo
The purpose of this blog post is to inform you how to enforce Multi-Factor Authentication (MFA) via an external device during Windows logon and UAC prompts. A 3rd party tool Duo Security makes this possible.
Requirements:
What is Duo Security?
Duo Security is a part of Cisco. They combine security expertise with a user philosophy to provide two-factor authentication, endpoint remediation, and secure single sign-on tools for the modern era. Duo is built on the promise of doing the right thing for its customers. This promise is as central to their business as the product itself. their four guiding principles are the heart of this sensibility: Easy, Effective, Trustworthy, Enduring
More information about Duo Security can be found here.
Price of Duo Security
Note. these are the prices at the time of writing this blog
Duo Security has several license options. Duo can be used for free up to 10 users. With the most comprehensive license, Duo can limit application access for Intune enrolled devices. In this blog post, I will focus only on Duo MFA
- Duo Free
- (up to 10 users)
- Duo MFA
- $3 / User / Month
- DUO Access
- $6 / User / Month
- Duo Beyond
- $9 / User / Month
For actual prices and features check Pricing | Duo Security
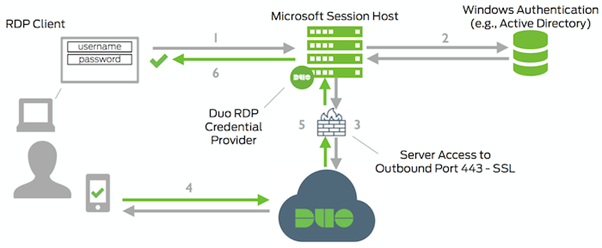
Connection Flow
- A user initiates an RDP connection, Windows logon, or UAC elevation
- Verify the credentials
- DUO Windows Logon credential provider establish a connection to Duo Security over TCP port 443
- Verify secondary authentication via Duo Security’s service and app.
- Duo Windows Logon credential provider receives the authentication response
- RDP, Windows logon, or UAC elevation will be logged in
Create DUO Security Tenant
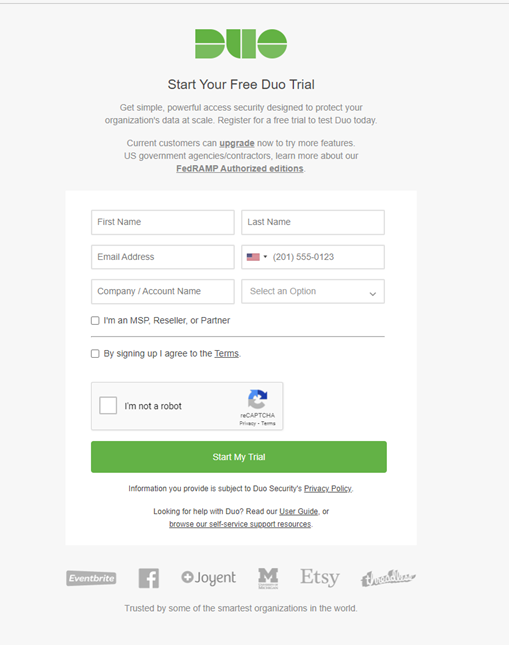
- Create a DUO Security tenant here: Start Your Duo Trial
- Provide all needed information and click on Start my trial
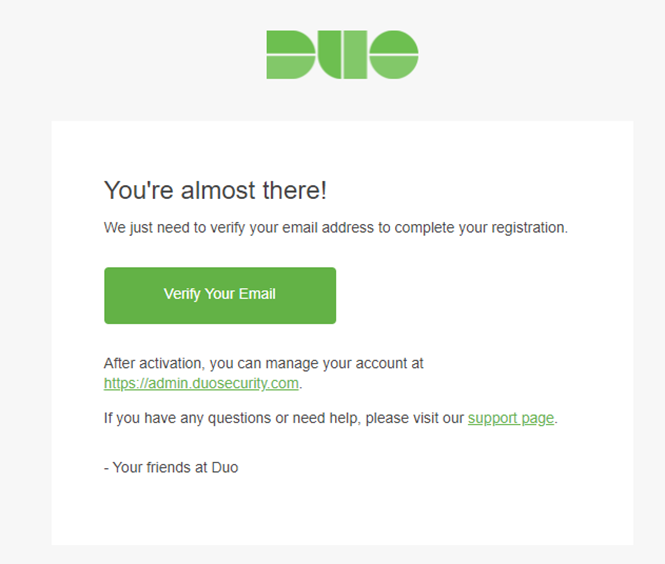
- Check your e-mail and verify your Email
- A new Web browser page will be opened, to walk through the setup. Click on the Get started button.
- Create and confirm your password
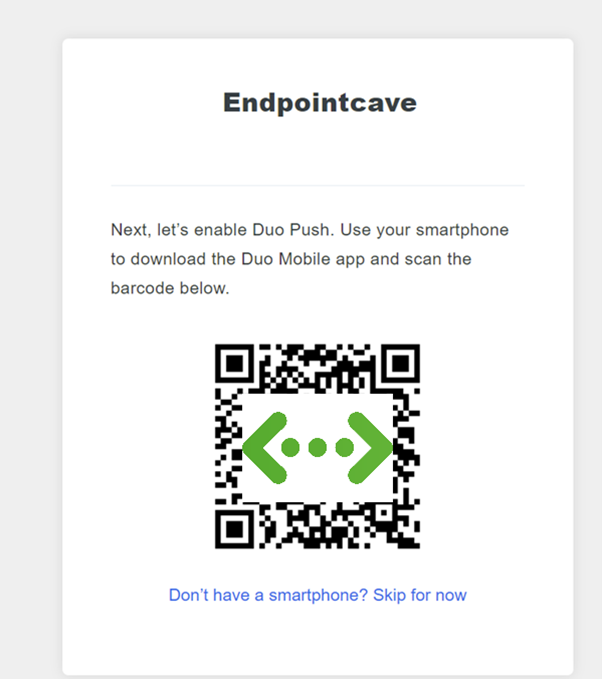
- Download the Duo Mobile app from the app store.
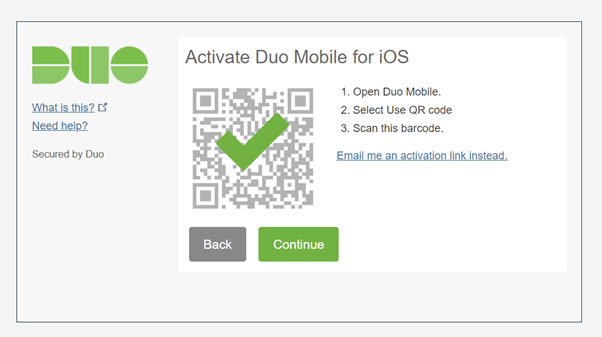
- Open the Duo Mobile app, click on + Add
- Click on Use QR Code and scan the QR Code
- The next step is to enter your phone number and verify your phone with a text message.
- After you verify your phone number, you are ready to go.
- Click on Continue to Duo Admin Panel Login
Protect Windows logon / RPD and elevation prompt with Duo Security
- Open Duo Security portal via https://admin.duosecurity.com/
- Enter your credentials and login to Duo.
- Click on Applications in the menu
- Then click on Protect an application
- Search for Microsoft RDP
- Click on Protect
- Scroll down to Settings, rename Microsoft RDP to Windows Logon MFA
- Set Username normalization to None
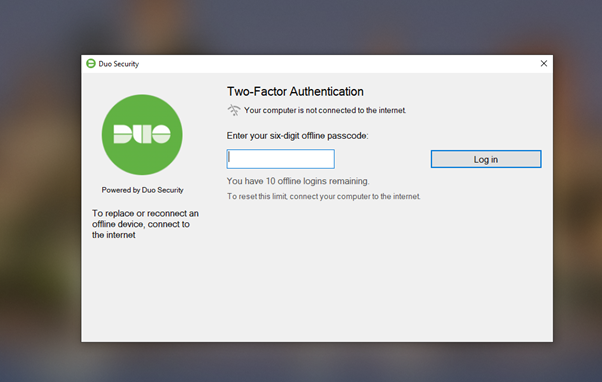
- Scroll down to Offline Access Settings and enable Offline login and enrollment, change settings to meet your organization’s security requirements
- Click on Save
Synchronize Azure AD Users
- Click on Users in the menu and then on Directory Sync
- Click on + Add New Azure Active Directory Sync
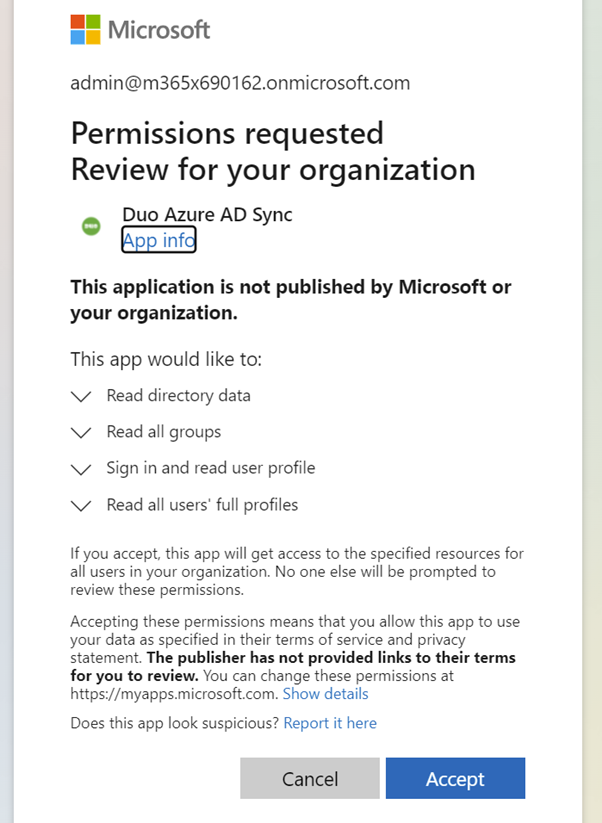
- You need to grant Duo permission to read from your organization’s Azure Active Directory.
- Click on Authorize connection
- Logon to you Azure AD Tenant with a Global Admin
- Provide Duo Azure AD Sync access to your organization. Click on Accept
- Configure the username as the userPrincipalName attribute under Synced attributes
- Turn off Normalize usernames before importing them under Normalize usernames
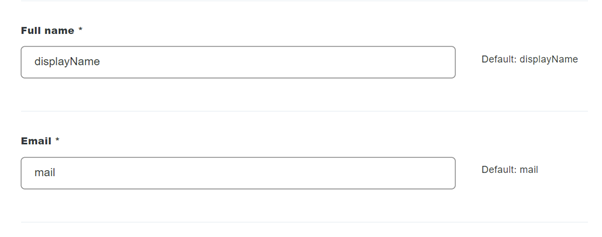
- Set Full name to DisplayName Attribute
- Set Email to mail attribute
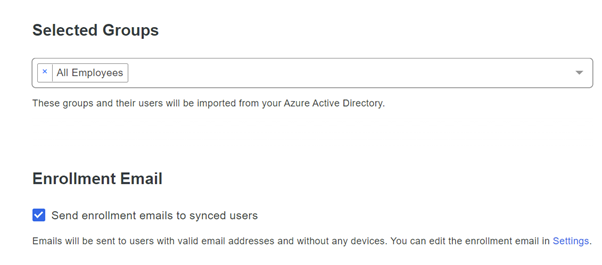
- Scroll down till selected groups, and select your Azure AD group to synchronize your users
- Select Send enrollment emails to synced users under Enrollment Email
- Click on Save Directory at the top of the page
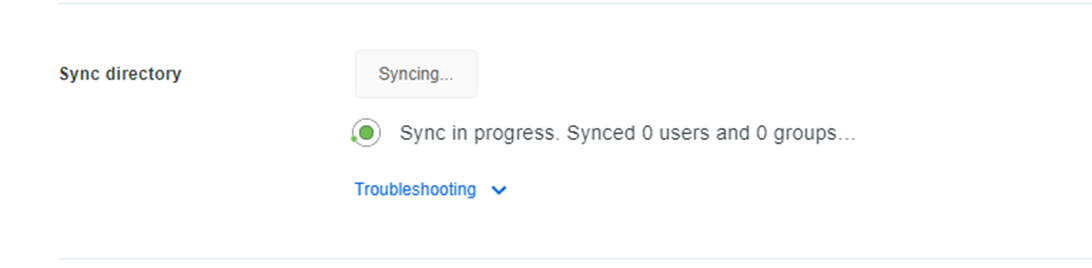
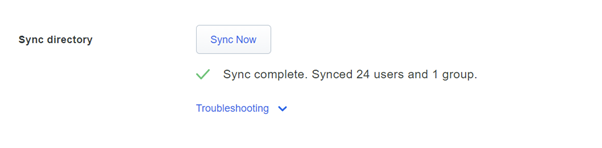
- Now you can click on the Sync Now button
- After a few minutes, the Sync is completed.
Enroll end-user with Duo Security
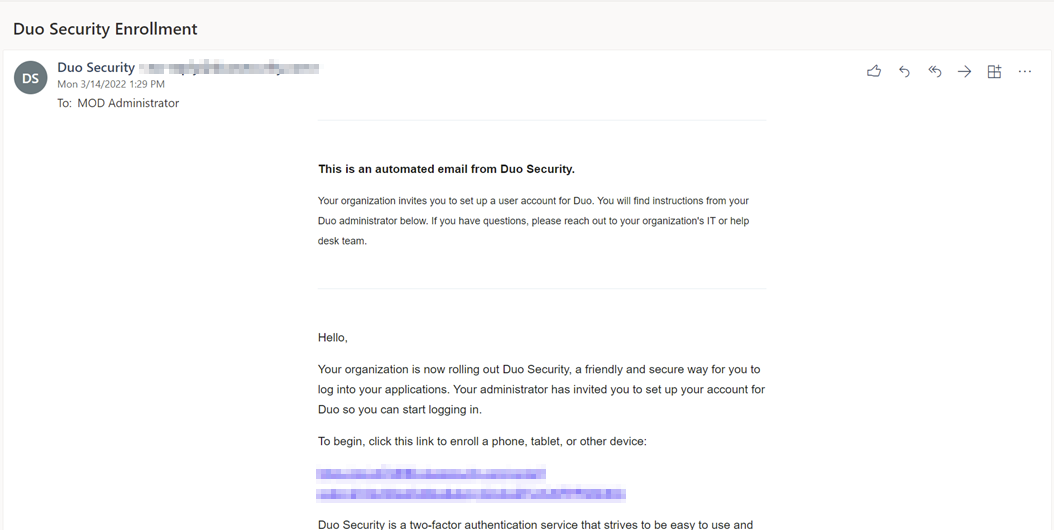
- All synced users have received an email from Duo to enable and enroll their accounts.
- The user must click on the link in the email. The Browser will be opened, and the enrollment starts.
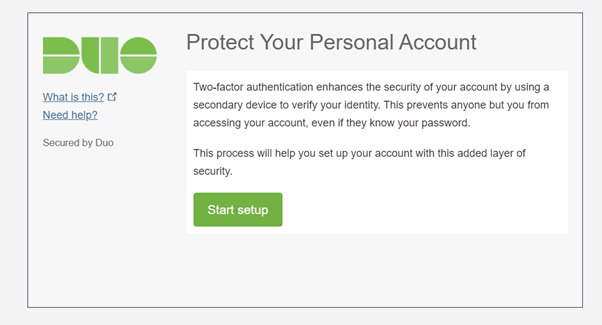
- Click on Start setup
- The user must select a region and enter their phone number.
- Click on Continue
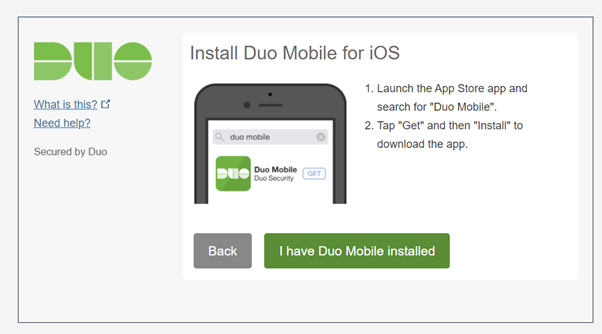
- The user must download Duo Mobile and clicks on I have Duo Mobile installed
- The user opens the Duo Mobile app, clicks on + Add
- Clicks on Use QR Code and scan the QR Code
- Then clicks on Continue, in the next screen the user must set their preferred option to authenticate. Notification or SMS and clicks on Finish Enrollment
Create Duo Security installer for Intune deployment
- Download here Duo Authentication for Windows Logon and RDP files
Duo Authentication for Windows Logon and RDP | Duo Security
Direct download link: https://dl.duosecurity.com/duo-win-login-latest.exe - Copy the duo-win-login-X.X.X.exe to an empty folder
- Create the .intunewin package with the Intune content preparation tool with the following command:
{directory of WinappUtil}\IntuneWinAppUtil.exe -c {directory of duo-win-login-x.x.x.exe } -s duo-win-login-x.x.x.exe -o .\ -qNote. Replace version x.x.x with the current version. I have used version 4.2.0 in this blog post
Deploy Duo installer via Microsoft Intune
- Open Microsoft Endpoint manager
- In the menu select Apps
- Under Apps, select Windows
Or use the following link Windows Apps – Microsoft Endpoint Manager admin center - Click on + Add
- Select the App Type Windows App (Win32)and click on Select
- Click on the Select app package file and click on the blue directory icon
- The file explorer will open and browse to the .Intunewin file that you have created.
- Click on OK
- Set a name, description, and publisher of the app
- Click on Next
- Set the following Install and uninstall commands
Install
duo-win-login-x.x.x.exe /S /V" /qn IKEY="{Application Windows Logon MFA integration key}" SKEY="{Application Windows Logon MFA Secret key}" HOST="{Application Windows Logon MFA API hostname}" AUTOPUSH="#0" UAC_PROTECTMODE="#2" USERNAMEFORMAT="#0" FAILOPEN="#0" SMARTCARD="#0" ENABLEOFFLINE="#1" RDPONLY="#0""Note. Installation commands can be found here
Uninstall
duo-win-login-x.x.x.exe /x /s /v/qnNote. Replace version x.x.x with the current version. I have used version 4.2.0 in this blog post
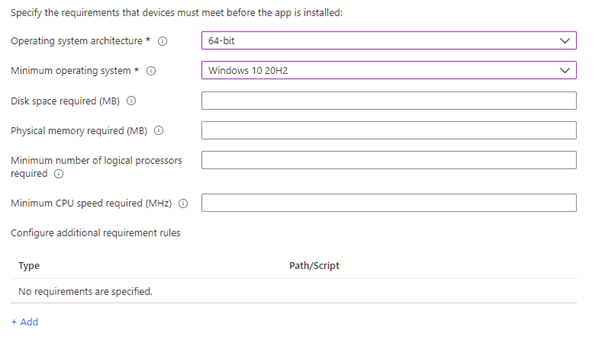
- Select 64-bit as the operating system architecture
- Select Windows 10 20H2 as the minimum Operating system
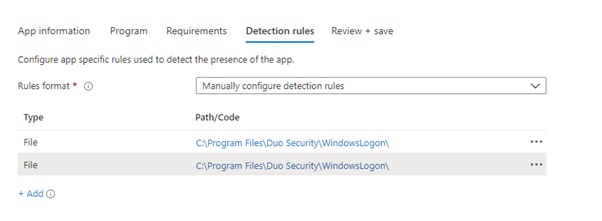
- Select Manually configure detection rules as the rules format
- Click on + Add and configure the following detection rule
| Rule type | File | File |
| Path | C:Program FilesDuo SecurityWindowsLogon | C:Program FilesDuo SecurityWindowsLogon |
| File or folder | DuoCredFilter.dll | DuoCredProv.dll |
| Detection method | File or folder exists | File or folder exists |
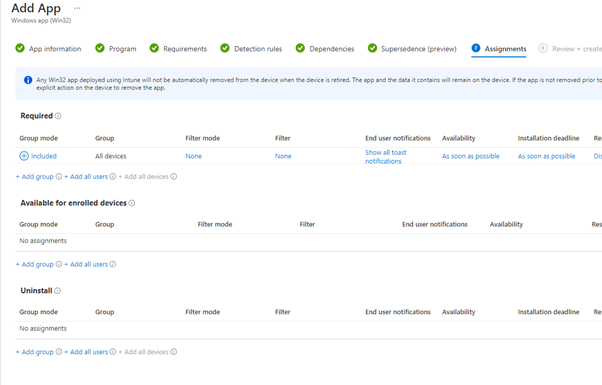
- Set the assignment to require for all devices
- Click on Next and on the Dependencies and Supersedence section click also next
- Click on next. Check the app configuration and click on Create.
- The app will be created and uploaded
More information
- Pricing | Duo Security
- Multi-Factor Authentication (MFA) | Duo Security
- Duo Authentication for Windows Logon and RDP | Duo Security
- Can I silently install or update Duo Authentication for Windows Logon from a command line or PowerShell?
- Duo Authentication for Windows Logon and RDP | Duo Security
- How do I silently uninstall Duo Authentication for Windows Logon?
- Add and assign Win32 apps to Microsoft Intune | Microsoft Docs
- Azure AD app consent experiences – Microsoft identity platform | Microsoft Docs








 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.

Leave a Reply
Want to join the discussion?Feel free to contribute!