Enforce BitLocker startup PIN on Windows with Intune
The purpose of this blog post is to inform you how to enforce a BitLocker startup Pin for standard users. I was inspired by the solution of Oliver Kieselbach, but his solution was user-driven and not enforced so I decided to change some settings, make a proactive remediation script, and create a custom Compliance check to enforce the BitLocker startup pin.
Requirements:
Original solution
By default, a standard user is not able to set a BitLocker startup pin. Only a local admin can set the pin code, so there must be another method. I did some research, and I found the solution of Oliver Kieselbach. You can find his blog and the original content here.
Enforced solution
The solution did not force the user to set the startup pin, but I wanted to enforce it, so I decided to modify his solution. I change some settings in his code, so the user cannot close the pin code diagram anymore. Created the Win32 app and set it as a required install so everything was on the device. The last piece of the puzzle was to enforce it with a proactive remediation script and a custom compliance policy.
What did I change?
File: popup.ps1
Line: 1
Original:
# Author: Oliver Kieselbach (oliverkieselbach.com)Changed to:
# Author: Oliver Kieselbach (oliverkieselbach.com) & Rene Laas (endpointcave.com)File: popup.ps1
Line: 12
Add:
# - 02/23/2022 Added simple PIN i.e. 000000 check # added by Rene Laas - Endpointcave.comFile: popup.ps1
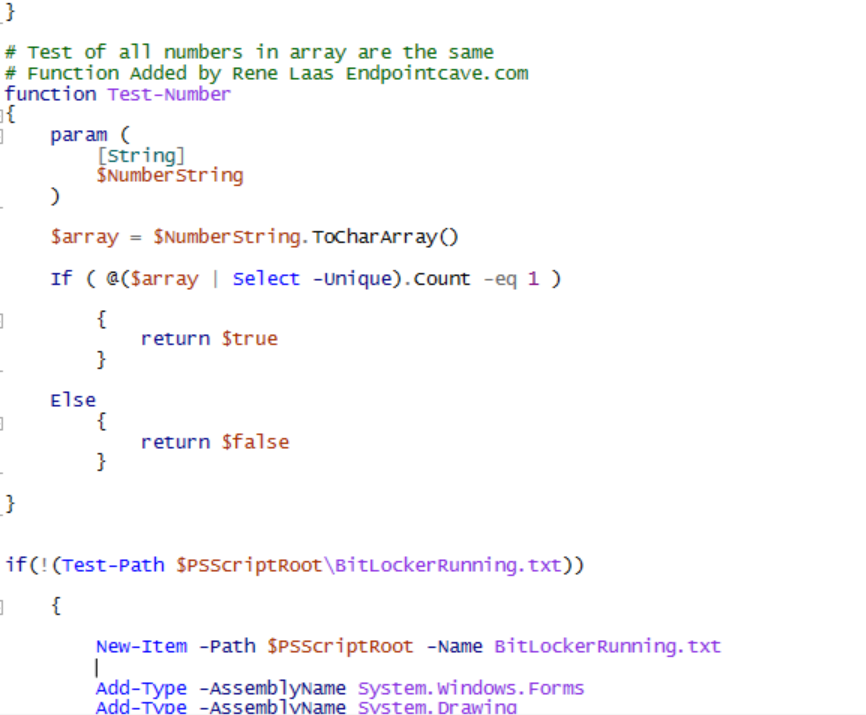
Line: 66
Add:
# Test of all numbers in array are the same
# Function Added by Rene Laas Endpointcave.com
function Test-Number
{
param (
[String]
$NumberString
)
$array = $NumberString.ToCharArray()
If ( @($array | Select -Unique).Count -eq 1 )
{
return $true
}
Else
{
return $false
}
}
if(!(Test-Path $PSScriptRoot\BitLockerRunning.txt))
{File: popup.ps1
Line: 113
Original:
$language = Get-Content language.json -Encoding UTF8 | ConvertFrom-JsonChanged to:
$language = Get-Content "C:\progra~2\BitLockerPINDialog\language.json" -Encoding UTF8 | ConvertFrom-Json # Modified by Rene Laas Endpointcave - Change json locationFile: popup.ps1
Line: 176
Original:
$pathPINFile = $(Join-Path -Path "$env:SystemRoot\tracing" -ChildPath "168ba6df825678e4da1a.tmp")Changed to:
#$pathPINFile = $(Join-Path -Path "$env:SystemRoot\tracing" -ChildPath "168ba6df825678e4da1a.tmp")
$pathPINFile = "C:\PinTemp\PIN-prompted.txt" # Modified by Rene Laas Endpointcave.comFile: popup.ps1
Line: 183
Add:
Remove-Item -Path $PSScriptRoot\BitLockerRunning.txt -Force # Added by Rene Laas Endpointcave.comFile: popup.ps1
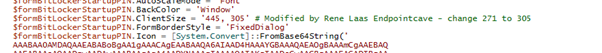
Line: 241
Original:
$formBitLockerStartupPIN.ClientSize = '445, 271'Changed to:
$formBitLockerStartupPIN.ClientSize = '445, 305' # Modified by Rene Laas Endpointcave - change 271 to 305File: popup.ps1
Line: 1783
Add:
$formBitLockerStartupPIN.ControlBox = $False # Added by Rene Laas EndpointcaveFile: popup.ps1
Line: 1794
Original:
$labelPINIsNotEqual.Location = '275, 181'Changed to:
$labelPINIsNotEqual.Location = '275, 210' # Modified by Rene Laas Endpointcave - from 181 to 210File: popup.ps1
Line: 1805
Original:
$labelRetypePIN.Location = '26, 146'Changed to:
$labelRetypePIN.Location = '26, 186' # Modified by Rene Laas Endpointcave - from 146 to 186File: popup.ps1
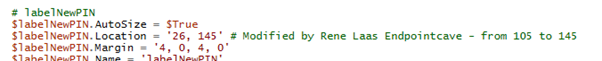
Line: 1815
Original:
$labelNewPIN.Location = '26, 105'Changed to:
$labelNewPIN.Location = '26, 145' # Modified by Rene Laas Endpointcave - from 105 to 145File: popup.ps1
Line: 1834
Original:
$panelBottom.Controls.Add($buttonCancel)Changed to:
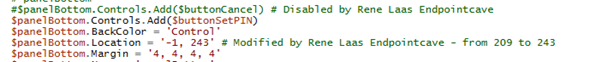
#$panelBottom.Controls.Add($buttonCancel) # Disabled by Rene Laas EndpointcaveFile: popup.ps1
Line: 1837
Original:
$panelBottom.Location = '-1, 209'Changed to:
$panelBottom.Location = '-1, 243' # Modified by Rene Laas Endpointcave - from 209 to 243File: popup.ps1
Line: 1855
Original:
$buttonSetPIN.Location = '225, 17'Changed to:
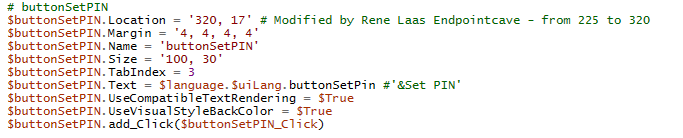
$buttonSetPIN.Location = '320, 17' # Modified by Rene Laas Endpointcave - from 225 to 320File: popup.ps1
Line: 1877
Original:
$textboxRetypedPin.Location = '140, 143'Changed to:
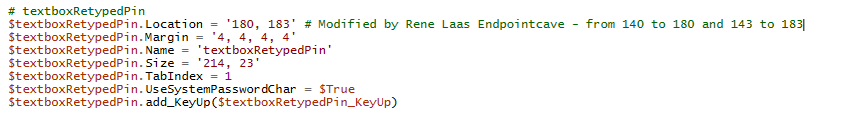
$textboxRetypedPin.Location = '180, 183' # Modified by Rene Laas Endpointcave - from 140 to 180 and 143 to 183File: popup.ps1
Line: 1886
Original:
$textboxNewPin.Location = '140, 102'Changed to:
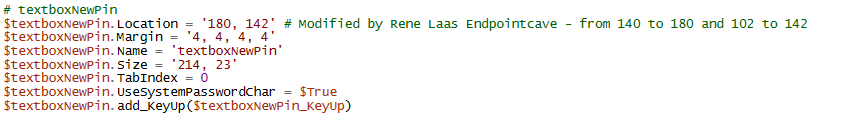
$textboxNewPin.Location = '180, 142' # Modified by Rene Laas Endpointcave - from 140 to 180 and 102 to 142File: popup.ps1
Line: 1901
Add:
}
Else
{
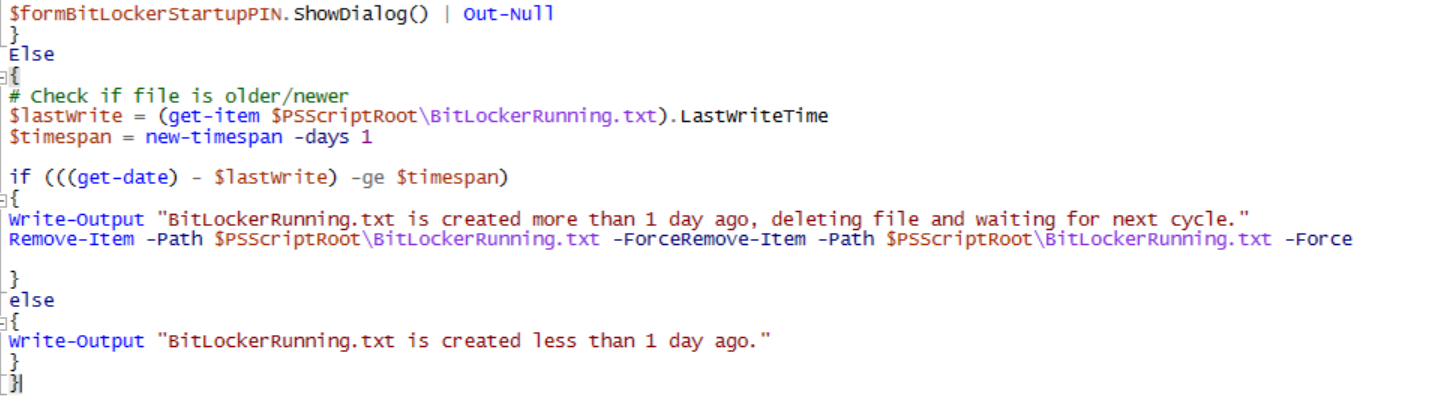
# Check if file is older/newer
$lastWrite = (get-item $PSScriptRoot\BitLockerRunning.txt).LastWriteTime
$timespan = new-timespan -days 1
if (((get-date) - $lastWrite) -ge $timespan)
{
Write-Output "BitLockerRunning.txt is created more than 1 day ago, deleting file and waiting for next cycle."
Remove-Item -Path $PSScriptRoot\BitLockerRunning.txt -ForceRemove-Item -Path $PSScriptRoot\BitLockerRunning.txt -Force
}
else
{
Write-Output "BitLockerRunning.txt is created less than 1 day ago."
}
}File: Setbitlockerpin.ps1
Line: 13
Original:
.\ServiceUI.exe -process:Explorer.exe "$env:SystemRoot\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -Ex bypass -file "$PSScriptRoot\Popup.ps1"Changed to:
C:\progra~2\BitLockerPINDialog\ServiceUI.exe -process:Explorer.exe "$env:SystemRoot\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -Ex bypass -file "C:\progra~2\BitLockerPINDialog\Popup.ps1" # Modified by Rene Laas Endpointcave - Path modifiedFile: Setbitlockerpin.ps1
Line: 19
Original:
$pathPINFile = $(Join-Path -Path "$env:SystemRoot\tracing" -ChildPath "168ba6df825678e4da1a.tmp")Changed to:
#$pathPINFile = $(Join-Path -Path "$env:SystemRoot\tracing" -ChildPath "168ba6df825678e4da1a.tmp")
$pathPINFile = "C:\PINtemp\PIN-prompted.txt" # Modified by Rene Laas EndpointcaveAdd install/uninstall script to the source?
For the correct working of the script, some files must be present on the device. I have added therefore a PowerShell installation and an uninstallation script that will make sure the needed files are in the required subdirectory of the program files directory or can be deleted.
Install.ps1:
New-Item -ItemType Directory -Force -Path C:\progra~2\BitLockerPINDialog\
Move-Item -Path .\*.* -Destination C:\progra~2\BitLockerPINDialog\Uninstall.ps1:
Remove-Item -Path C:\progra~2\BitLockerPINDialog -RecurseHow to configure the BitLocker settings
- Open Microsoft Endpoint manager
- In the menu select Endpoint security
- Under Manage, select Disk encryption
Or use the following link Disk encryption – Microsoft Endpoint Manager admin center - Click on + Create Policy
- Select Windows 10 and later as the platform and BitLocker as the profile
- Click on create
- Set a name and optionally the description and click on Next
- Configure the following settings
BitLocker – Base settings
| Setting | Value |
|---|---|
| Enable full disk encryption for OS and fixed data drives | Yes |
| Require storage cards to be encrypted (mobile only) | Not configured |
| Hide prompt about third-party encryption | Yes |
| Allow standard users to enable encryption during Autopilot | Yes |
| Configure client-driven recovery password rotation | Enable rotation on Azure AD and Hybrid-joined devices |
Bitlocker OS Drive Settings
| Setting | Value |
|---|---|
| BitLocker system drive policy | Configure |
| Startup authentication required | Yes |
| Compatible TPM startup | Allowed |
| Compatible TPM startup PIN | Allowed |
| Compatible TPM startup key | Blocked |
| Compatible TPM startup key and PIN | Blocked |
| Disable BitLocker on devices where TPM is incompatible | Not configure |
| Enable preboot recovery message and URL | Not configure |
| System drive recovery | Configure |
| Recovery key file creation | Allowed |
| Configure BitLocker recovery package | Password and key |
| Require device to back up recovery information to Azure AD | Yes |
| Recovery password creation | Allowed |
| Hide recovery options during BitLocker setup | Yes |
| Enable BitLocker after recovery information to store | Yes |
| Block the use of certificate-based data recovery agent (DRA) | Not configure |
| Minimum PIN length | 6 |
| Configure encryption method for Operating System drives | AES 256bit XTS |
Note. I recommended to configure BitLocker – Fixed Drive Settings and BitLocker – Removable Drive Settings as well, but both are not required for the BitLocker Startup Pin
How to create the BitLocker Startup Pin package
- Download the SetBitLockerPin files of Oliver his Github page.
Link: Intune/Win32/SetBitLockerPin at master · okieselbach/Intune · GitHub - Copy the SetBitLockerPin files to an empty folder
- Modify the files that are mentioned in the paragraph What did I change?
- Create the .intunewin package with the Intune content preparation tool with the following command:
{directory of WinappUtil}\IntuneWinAppUtil.exe -c { directory of SetBitLockerPin files } -s install.ps1 -o .\ -qOr
- Download the modified SetBitLockerPin files from my Github page
Link: EndpointCave.com/BitLockerStartupPin at main · Renelaas/EndpointCave.com · GitHub - Copy the SetBitLockerPin files to an empty folder
- Create the .intunewin package with the Intune content preparation tool with the following command:
{directory of WinappUtil}\IntuneWinAppUtil.exe -c {directory of SetBitLockerPin files} -s install.ps1 -o .\ -qOr
- Download the .intunewin package here
How to install BitLocker solution
- Open Microsoft Endpoint manager
- In the menu select Apps
- Under Apps, select Windows
Or use the following link Windows Apps – Microsoft Endpoint Manager admin center - Click on + Add
- Select the App Type Windows App (Win32) and click on Select
- Click on the Select app package file and click on the blue directory icon
- The file explorer will open and browse to the .Intunewin file that you have created.
- Click on OK
- Set a name, description, and publisher of the app
- Click on Next
- Set the following Install and uninstall commands
Install:
powershell.exe -executionpolicy bypass -file ".\install.ps1"Uninstall:
powershell.exe -executionpolicy bypass -file ".\uninstall.ps1"- Select 64-bit as the operating system architecture
- Select Windows 10 20H2 as the minimum Operating system
- Select Manually configure detection rules as the rules format
- Click on + Add and configure the following detection rule
| Setting | Value |
|---|---|
| Rule Type | File |
| Path | C:\progra~2\BitLockerPINDialog\ |
| File or folder | ServiceUI.exe |
| Detection method | File or folder exists |
| Associated with a 32-bit app on 64-bit clients | No |
- Click on Next and on the Dependencies and Supersedence section click also next
- Set the assignment to require for all devices
- Click on next. Check the app configuration and click on Create.
- The app will be created and uploaded
Proactive Remediation Scripts that need to be uploaded to Intune
Detection Script:
$pin = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.KeyProtectorType -eq 'TpmPin' }
if (((Get-BitLockerVolume -MountPoint $env:SystemDrive).VolumeStatus) -ne "FullyDecrypted")
{
Write-Output "Encryption enabled"
if ($pin -ne $null)
{
Write-Output "TPM Pin set"
Exit 0
}
else
{
Write-Output "TPM Pin is not set"
Exit 1
}
}
else
{
Write-Output "Encryption not yet started"
Exit 0
}Remediation Script:
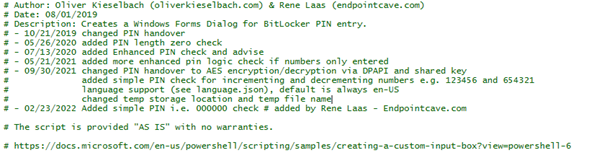
#Author: Oliver Kieselbach (oliverkieselbach.com) & Rene Laas (endpointcave.com)
# Date: 08/01/2019
# Description: Starts the Windows Forms Dialog for BitLocker PIN entry and receives the PIN via exit code to set the additional key protector
# - 10/21/2019 changed PIN handover
# - 02/10/2020 added content length check
# - 09/30/2021 changed PIN handover to AES encryption/decryption via DPAPI and shared key
# added simple PIN check for incrementing and decrementing numbers e.g. 123456 and 654321
# language support (see language.json), default is always en-US
# changed temp storage location and temp file name
# The script is provided "AS IS" with no warranties.
# Added by Rene Laas endpoincave
if (!(Test-Path "C:\PINtemp"))
{
New-Item -Path 'C:\PINtemp' -ItemType Directory
Write-output "Temp directory created"
}
else
{
Write-output "Temp directory already exist"
}
# Added by Rene Laas Endpointcave
# Pin temp file
$PathPINtemp = "C:\PINtemp\"
$pathPINFile = $PathPINtemp + "PIN-prompted.txt"
#######################
C:\progra~2\BitLockerPINDialog\ServiceUI.exe -process:Explorer.exe "$env:SystemRoot\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -Ex bypass -file "C:\progra~2\BitLockerPINDialog\SetBitLockerPin.ps1" # Modified by Rene Laas Endpointcave
$exitCode = $LASTEXITCODE
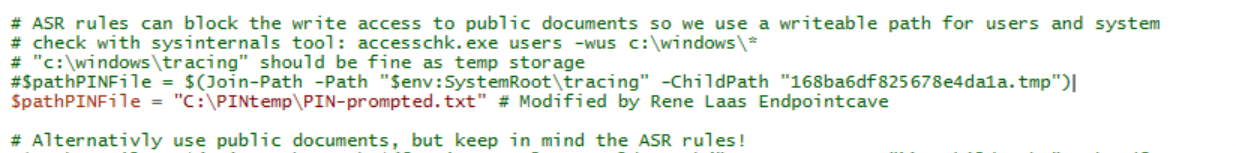
# ASR rules can block the write access to public documents, so we use a writeable path for users and system
# Check with sysinternals tool: accesschk.exe users -wus c:\windows\*
# "c:\windows\tracing" should be fine as temp storage
#$pathPINFile = $(Join-Path -Path "$env:SystemRoot\tracing" -ChildPath "168ba6df825678e4da1a.tmp")
# Alternativly use public documents, but keep in mind the ASR rules!
#$pathPINFile = $(Join-Path -Path $([Environment]::GetFolderPath("CommonDocuments")) -ChildPath "168ba6df825678e4da1a.tmp")
If ($exitCode -eq 0 -And (Test-Path -Path $pathPINFile)) {
$encodedText = Get-Content -Path $pathPINFile
if ($encodedText.Length -gt 0) {
# Using DPAPI with a random generated shared 256-bit key to decrypt the PIN
$key = (43,155,164,59,21,127,28,43,81,18,198,145,127,51,72,55,39,23,228,166,146,237,41,131,176,14,4,67,230,81,212,214)
$secure = ConvertTo-SecureString $encodedText -Key $key
# Code for PS7+
#$PIN = ConvertFrom-SecureString -SecureString $secure -AsPlainText
# Code for PS5
$PIN = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($secure))
Add-BitLockerKeyProtector -MountPoint $env:SystemDrive -Pin $(ConvertTo-SecureString $PIN -AsPlainText -Force) -TpmAndPinProtector
}
}
# Cleanup ###
# Modified by Rene Laas Endpointcave
if((Test-Path $pathPINFile))
{
Remove-Item -Path $pathPINFile -Force -Recurse
Write-output "Encrypted Pin file deleted"
}
if((Test-Path $PathPINtemp))
{
Remove-Item -Path $PathPINtemp -Force -Recurse
Write-Output "Deleted temp folder"
}How to enforce BitLocker Startup pin via Intune with Proactive Remediation Scripts
- Open Microsoft endpoint manager
- In the menu select Reports
- Click on Endpoint analytics in the menu under Analytics
- Click on Proactive remediations
Or use the following link Endpoint analytics – Microsoft Endpoint Manager admin center - Click on Create script package
- Provide a Name script name
- Set a description, so that everyone with access to the portal knows the purpose of the script
- Click on Next
- Upload the Detection scripts and Remediation scripts.
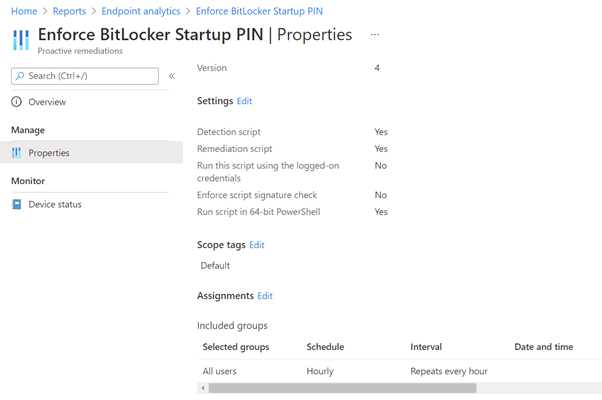
- Configure the following PowerShell script settings
| Setting | Value |
|---|---|
| Run this script using the logged on credentials | No |
| Enforce script signature check | No |
| Run script in 64-bit PowerShell Host | Yes |
- Click on Nextand on the Scope tags section click on Next
- Assign remediation script to All User
- Change the schedule via the 3 bullets and Click on Edit
- Click on the dropdown list and change the frequency from Daily to Hourly and click on Next
- Check on the review + create page if all settings are configured correctly and click on Create
Result:
Create a Custom Compliance check
- Open Microsoft endpoint manager
- In the menu select Devices
- Click on Compliance Policies under Policy in the new menu
- In the menu click on Scripts
or use the following link: Compliance policies – Microsoft Endpoint Manager admin center - Click on + Add and select Windows 10 and later
- Fill in the following settings
| Setting | Value |
|---|---|
| Name | BitLockerPin |
| Description | Custom compliance check for BitLocker Startup Ping |
| Publisher | Endpointcave.com |
- Click on next
- Configure the following Custom script settings
Detection script Script
$BLinfo = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.KeyProtectorType -eq 'TpmPin' }
$hash = @{KeyProtectorType = $BLinfo.KeyProtectorType}
return $hash | ConvertTo-Json -Compress| Setting | Value |
|---|---|
| Run this script using the logged on credentials | No |
| Enforce script signature check | No |
| Run script in 64-bit PowerShell Host | Yes |
- Click on Next, review the configuration, and click on Create
- The next step is to open an existing compliance policy
- In the menu click on policies
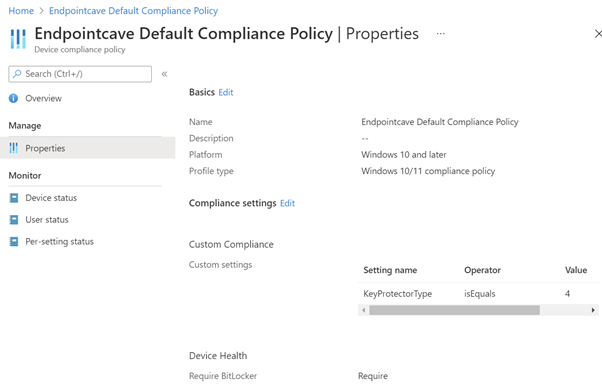
- Open an existing compliance policy to enforce BitLocker startup Pin
- Click on Properties under Manage
- Edit the compliance settings via the edit button
- Open the Custom Compliance section
- Configure the following Custom Compliance settings
| Setting | Value |
|---|---|
| Custom compliance | Required |
| Select your discovery script | BitlockerPin |
JSON
{
"Rules":[
{
"SettingName":"KeyProtectorType",
"Operator":"IsEquals",
"DataType":"Int64",
"Operand":"4",
"MoreInfoUrl":"https://endpointcave.com",
"RemediationStrings":[
{
"Language":"en_US",
"Title":"Bitlocker Startup Pin must be set",
"Description": " Bitlocker Startup Pin must be set "
}
]
}
]
}Result:

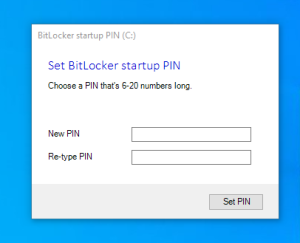
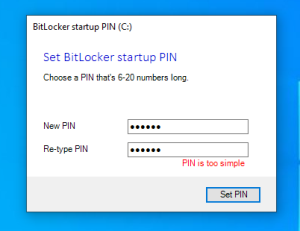
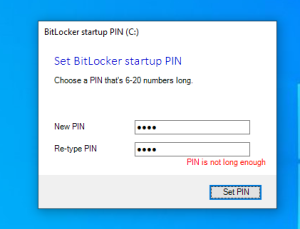



awesome script. one issue i found is that when i do an autopilot reset of the pc the win32 app package detects that the folder is still there so it does not try to redownload.
when the proactive remediation script runs it fails as it cannot find ‘C:\PINtemp\PIN-prompted.txt’
Is there a method of detecting after an auto pilot reset? for instance that a pin is set? unable to see anything in the registry. Closest i have is Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FVE\UseEnhancedPin
Hi
Sorry for the late delay, but I do not like to use Autopilot reset. The information of the previous user is still on the device and when they are Local Admin they can open the folder. I always use Fresh Start. What you could do is change the script build an option when the folder is older than x period remove the folder.
Hello René,
I have tried to use your solution on Microsoft Intune to generate startup PIN for non-administrator users for Bitlocker encryption. After windows device is enrolled on Microsoft Intune, silent encryption is not starting even if the Bitlocker policy has been applied. Win32 application has been installed successfully and proactive remediation script has been applied as well. Can you please confirm if popup to enter startup PIN will appear first before silent encryption starts on the Windows device or after the after the bitlocker encryption. I am using Windows 10 22H2 version. Thank you for replying.
Hi Vaibhav,
Bitlocker encyption is a dependency (Check Proactive Remediation detection script).
Does your devices have TPM 2.0? This a requirements for silent encryption.
Rene
Hello,
I have followed above given steps, but in few devices I am getting the set up pin prompt frequently even though the PIN is already set. And I also observed that compliance policy is showing not applicable to most of the devices and for some failing. Can anyone help in this?
Hi Alex, are your user allowed to set a password as pin prompt? I think if your pin is already set, you should check your Proactive remediation detection script
Hello, Thanks for creating this script. I followed your instructions and deployed the script/ intunewin but i don’t see any pop up. I have a couple of questions.
1. How do we run this script to create this folder? Can you provide some instructions for this? I ran it on PowerShell manually and also deployed it with intune but it failed.
New-Item -ItemType Directory -Force -Path C:\progra~2\BitLockerPINDialog\
Move-Item -Path .\*.* -Destination C:\progra~2\BitLockerPINDialog\
2. I have the Intunewin app successfully installed but i do not see any pop up? I assume it might be due to the folder not being created in my question 1
Hi Matt,
If you installed the Win32 application with the PowerShell script, it will create the folder in the program files folder and moved the files to that folder. Please follow the How to create the BitLocker Startup Pin package and How to install BitLocker solution part of the blog.
After the Win32 app is installed you should have some files in the folder and then the proactive remediation scripts can use this script to show the popup.
If you need more assistance, please let me know.
Kind regards,
Rene
Hi,
Has anyone has problems with the compliance policy not completing on Windows 11 Pro, Build 22H2?
My test computers report “Bitlocker PIN must be set” in ‘Company Portal’ even though an 11-digit PIN is set and it is requested on bootup – the script doesn’t seem to realise this. This works on earlier versions of Windows, but seems to have problems with this build version. This occurs on 2 different computers so far, so it’s not isolated to 1 computer.
Windows 11’s “Smart App Control” is turned off so I don’t think this is stopping the script.
The Proactive Remediation report is successful too.
The folder at “C:\progra~2\BitLockerPINDialog\” is also in place and all files appear to be correct too.
Any ideas or solutions would be gratefully received.
Thanks
Hi Ben,
Thanx for your comment. I will check on Win 11 device 22H2 device as well.
Can you confirm if you have tested the solution and works on Win10?
Kind regards,
Rene
Thanks Rene – just to follow up on this, we found out our Antivirus package was being too sensitive and was stopping this app from setting a PIN IF the antivirus package was installed before the PIN / encryption process has completed.
Our workaround is to allow the encryption to complete and a PIN to be configured as this program wants to do. When a PIN has been set, we adapted the remediation script from this page to also insert a temp log file on the computer when the message is set to – Write-Output “TPM Pin set” – we then make this file existence a Requirement on our Antivirus app configuration page so the app doesn’t install before the PIN is set / the file exists.
Please help , have tried this not really good with Intune . I did all the steps the the pop up showed on 2 P.C’s and we entered the code but it does not require the users to put the PIN after reboot.
Am i missing something? this happened on 2 Machines
Hi Wangu,
can you please check on the device where you get the popup if all the files are in the C:\progra~2\BitLockerPINDialog\ folder?
All needed files:
https://github.com/Renelaas/EndpointCave.com/tree/main/BitLockerStartupPin
Did the BitLocker Popup create a PIN-prompted.txt file in C:\PinTemp?
Has the proactive remediation Script been run?
Kind regards,
Rene
Good day , thank you so much for the response. I managed to resolve the issue. I removed the intune extension managed on the control panel and restated the machine. It worked fine and i have now deployed to about 400 machines no errors so far.
I am now working on migrating those that used Bitlocker onprem to the cloud then will be done. Thank you so much for the help. This was a massive project for me and its making me look good in front of our big client. They think I am a genious . Many thanks once again.
I have the same problem. I also removed the intune extension managed on the control panel en restarted my machine. But still no bitlocker PIN..
In don’t have a C:\PinTemp folder on that machine. Is that maybe the reason?
Many thanks.
Hi Rick,
Can you check if have all the files are in the correct folder? Are you getting the BitLocker Pin popup?
If not, please make sure all the files are in the C:\progra~2\BitLockerPINDialog\ folder or configure the remediation script correctly.
Kind regards,
Rene
Hi Rene , may you kindly confirm if this still works on Intune as i have tried as i see Intune is changed a bit. Its like a license is required for remediation script for windows or something.
Are there any changes that we need to make now with new Intune?
Thank you
Correct for Remedation script you need one of the following license:
Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
Windows 10/11 Virtual Desktop Access (VDA) per user
https://learn.microsoft.com/en-us/mem/intune/fundamentals/remediations
Thanks for this.
For some reason during the enrolment I’m encountering an error 0x81035202 with no indication as to why this has failed. Is this something you’ve seen before?
Hi Adam,
Can you provide me with more information?
Are you getting this error in the Intune portal? Is this an AutoPilot error code or application error code?
Kind regards,
Rene
This is during the pre-staging process when a machine has been given a ‘fresh start’ in InTune. The application install fails with that error code and halts the setup.
I’ve tried adding your .intunewin as an application in our CompanyPortal without enforcing it. This allows the application to ‘install’ but nothing happens. The bitlocker policy works great – it’s likely something I’ve missed when adding the .intunewin.
Hi Adam,
I have not seen or heard that before. Is it failing on the application or on something else, you can try that to remove the assignment of the application to check if the enrollment status page will complete successfully.
If you install the application manually it will create the “C:\progra~2\BitLockerPINDialog\” folder and place the correct file in the folder and the proactive remediation script will take care of the enforcement.
If you have any further questions, please let me know
Kind regards,
Rene
Hi,
I’ve worked through all of your documentation above. It seems the only part I’ve missed (and probably the most crucial) is the ‘Add install/uninstall script to the source?’ section.
Can you please provide information on how this should be implemented onto a device?
Thanks!
Hi,
first of all thanks a lot for this. This really helped us to get StartUpPin set for most of our hybrid join devices.
But sometimes if the encryption is delayed the startup pin pop will not show up. The endpoint analysis say “with issues” but you guys know whats the issue here?
Regards Max
Hey Rene,
the array function regarding same number in a row seemd to be not working.
The user interace is accepting a PIN like 0000 but the key is not set.
Any idea?
BR
Harald
have found the issue – line 161 needs to be changes (test-number function was missing)
if ($(Test-IncrementNumber -NumberString $textboxNewPin.Text) -or $(Test-DecrementNumber -NumberString $textboxNewPin.Text) -or $(Test-Number -NumberString $textboxNewPin.Text)) {
Hi Harald,
I am happy that you have found the issue. Thank you for let me know!
Kind regards,
Rene
Hi Rene,
found an other issue too – popup.ps line 1911 entry remove-Item -Path $PSScriptRoot\BitLockerRunning.txt -Force was added twice.
BR
Harald
Hey Rene,
One of my employees messaged you earlier on Twitter. Thank you for your prompt response, it is appreciated.
We deployed this at a customer and it worked great for Azure AD joined machines very well. However, it is not working on Hybrid join machines. We are still investigating this and i can post something here later after we figure it out but i wanted to mention that you have a line commented out that is making the hybrid join machines come back with an error. On the set-bitlockerpin script the directory that the encrypted temp pin is being stored is on the $env:system\tracing folder, but in your update, that line is commented out. We un-commented it out and now we can get to the root of the issue with hybrid Join Machines. Thought folks would like to know.
Mav
Hey Mav,
I am also trying to use this solution for Hybrid joined devices. Did you ever come to a conclusion on your investigation as to why Hybrid joined devices are having trouble? What are the issues you are seeing?
Thanks,
nope, in my opinion there is no reason to hybrid join machines, otherwise enforce that MDM policy win over GPO