Configure RBAC for Intune in a secure way
The purpose of this blog post is to inform you how to configure RBAC for Intune in a secure way via Role-assignable groups. So, the RBAC groups can only be populated by a Global administrator or Privileged role administrator.
If you want to configure Intune RBAC roles, you must assign the Intune roles to an Azure AD Group. This means that every admin with permissions to manage groups can assign Intune RBAC roles to a user. Role-assignable groups can only be managed by a Global administrator or Privileged role administrator, so if we combine this, we have a secure RBAC configuration. Another benefit of configuring Intune RBAC roles with a role-assignable group is that we can assign roles to the RBAC group, like a custom role to read the BitLocker recovery key.
Requirements:
What is RBAC, and why should I configure it?
RBAC means Role-based access control. Role-based access control is a method by which you can effectively and efficiently establish access control for information systems. You can specify a role and the required permission, so you can apply the least privileges principal. So, this means that you can limit for an admin what they can see and what they can change.
Within Intune, you can use the built-in roles which cover common roles, or you can create your own roles and define the set of permission that needs to be granted to the admin.
If you are having a helpdesk with level 1, level 2, and level 3 support. You do not want that your first-line helpdesk employees can change the Intune configuration, but they must be able to do some limited remote actions on the Intune devices. This is only achievable via RBAC.
Role-assignable groups
Assigning roles to groups can simplify the management of role assignments in Azure AD with minimal effort from your Global administrators or Privileged role administrators. For example, if an employee leaves the company or changes function, the Global admin or privileged role administrator must only populate the group instead of removing all their assigned roles.
If you want to assign a role to a group, you must create a new security group with the isAssignableToRole property set to true. The isAssignableToRole property is immutable, so it cannot be changed.
Note. You can create up to 500 role-assignable groups per Azure AD tenant.
If a group has a role assigned, any IT administrator who can manage group membership could also indirectly manage the membership of that role. So, an administrator can elevate their privilege in a way you do not want.
Role-assignable groups are designed to help prevent potential breaches by having the following restrictions:
- Only Global Administrators and Privileged Role Administrators can create and manage a role-assignable group.
- The membership type for role-assignable groups must be assigned.
- To prevent elevation of privilege, only a Privileged Authentication Administrator or a Global Administrator can change the credentials or reset MFA for members and owners of a role-assignable group.
- Group nesting is not supported. A group can’t be added as a member of a role-assignable group.
More information about Role-assignable groups can be found here.
Create a Role-assignable Group
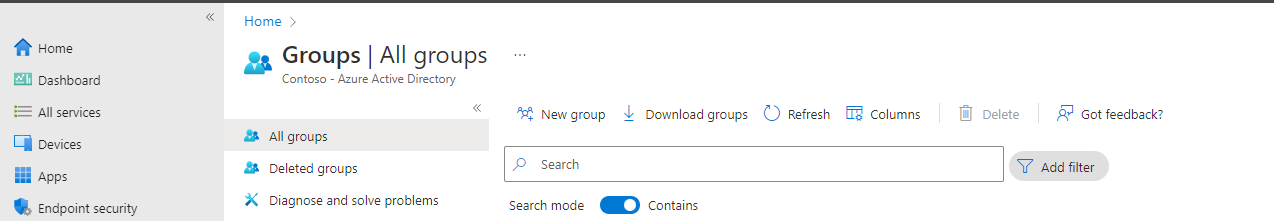
- Open Microsoft endpoint manager
- In the menu select Groups
- Under Groups, select All groups
- Click on New Group
Or use the following link New Group – Microsoft Endpoint Manager admin center
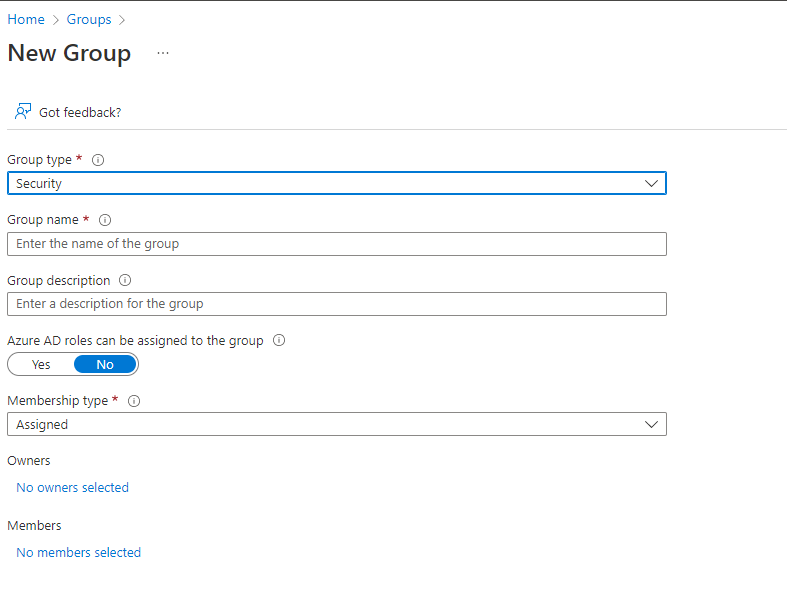
- Set the following settings
| SETTING | VALUE |
|---|---|
| Group type | Security |
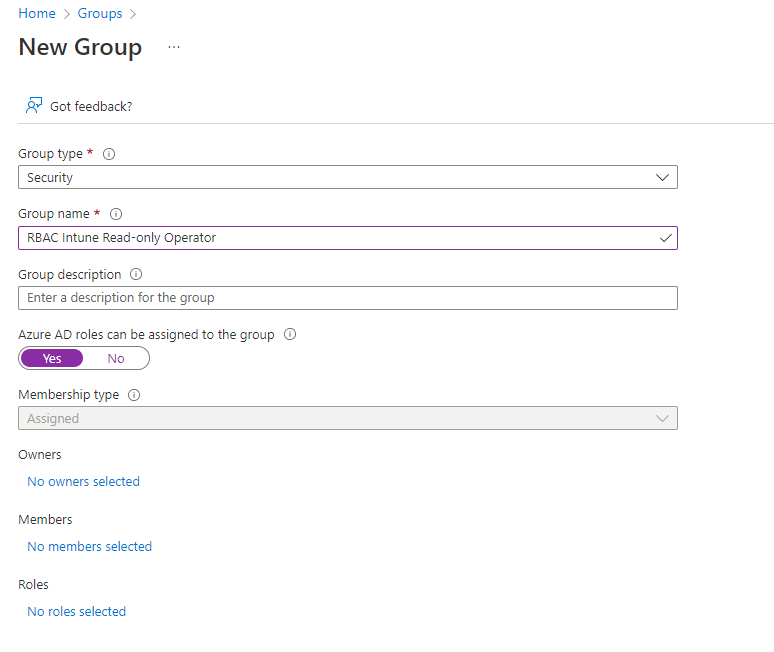
| Group Name | E.g., RBAC Intune Read-only Operator |
| Group Description | Set a good description, so that everyone with access to the portal knows the purpose of the group |
| Azure AD roles can be assigned to the group | Yes |
- So, that is all, Click on Create
- Select in the toast notification yes, this confirms that you are aware that the group cannot be changed
- The role-assignable group is now created and can only be assigned by a Global administrator or Privileged role administrator Role
Non-Intune license admin configuration
Tenants created before the 2006 release do not have by default the option Unlicensed admins enabled. So only accounts with an Intune license can access the Intune portal
See here my knowledge base item to enable the unlicensed admin option.
Configure an Intune RBAC role and assignable via a role-assignable group
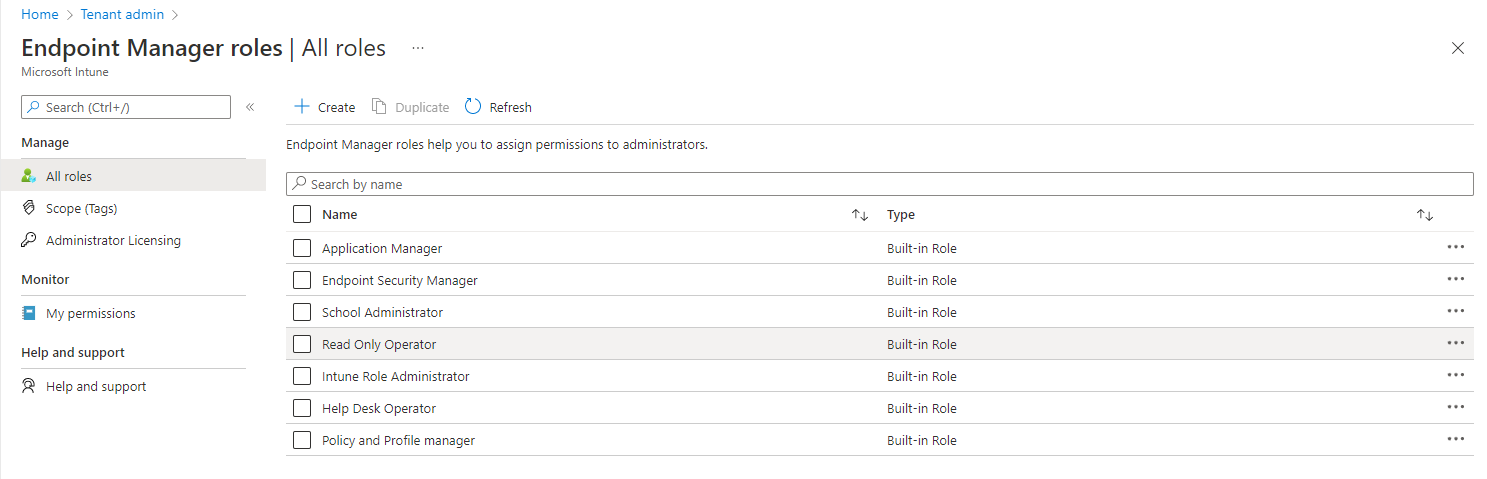
- Open Microsoft endpoint manager
- In the menu select Tenant administration
- Select in the second menu Roles
or use the following link Endpoint Manager roles – Microsoft Endpoint Manager admin center - Select the role that you will assign to the RBAC role-assignable group. E.g., Read-only Operator
- Click on properties and check the permissions.
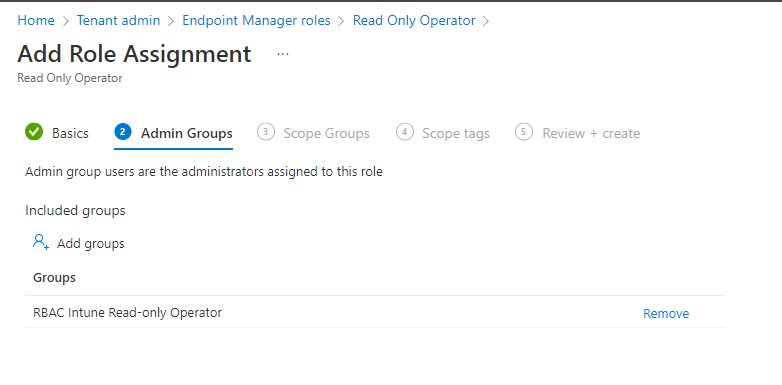
- So, we know the permissions now we will assign the role. Click on Assignment
- Click on + assign
- Set the following settings:
| SETTING | VALUE |
|---|---|
| Name | RBAC Intune Read-only Operator |
| Description | Set a good description, so that everyone with access to the portal knows the purpose of the RBAC assignment |
- Click on Next
- The next step is to assign the admin group.
- Click on +Add groups and you must select the role-assignable group
- Click on Next
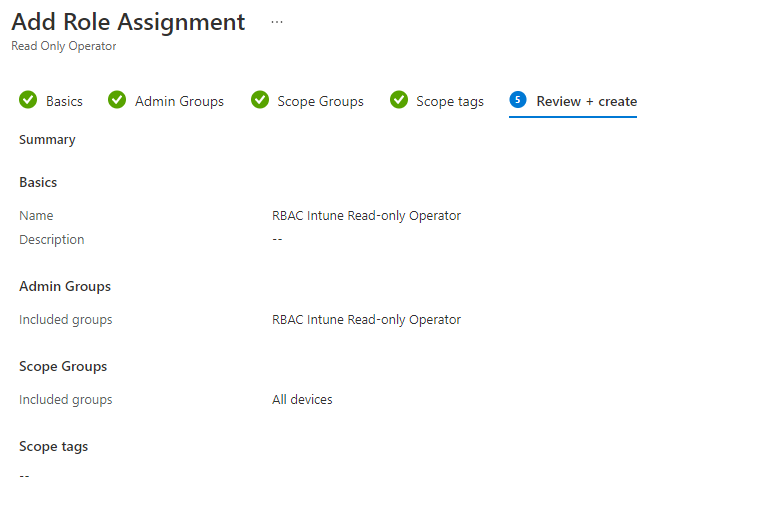
- Now we must set the scope group.
- Select all devices
- Click Next
- On the Scope tags section click Next. For this blog post we don’t want to scope anything for an administrator.
- Review your configuration and select Create
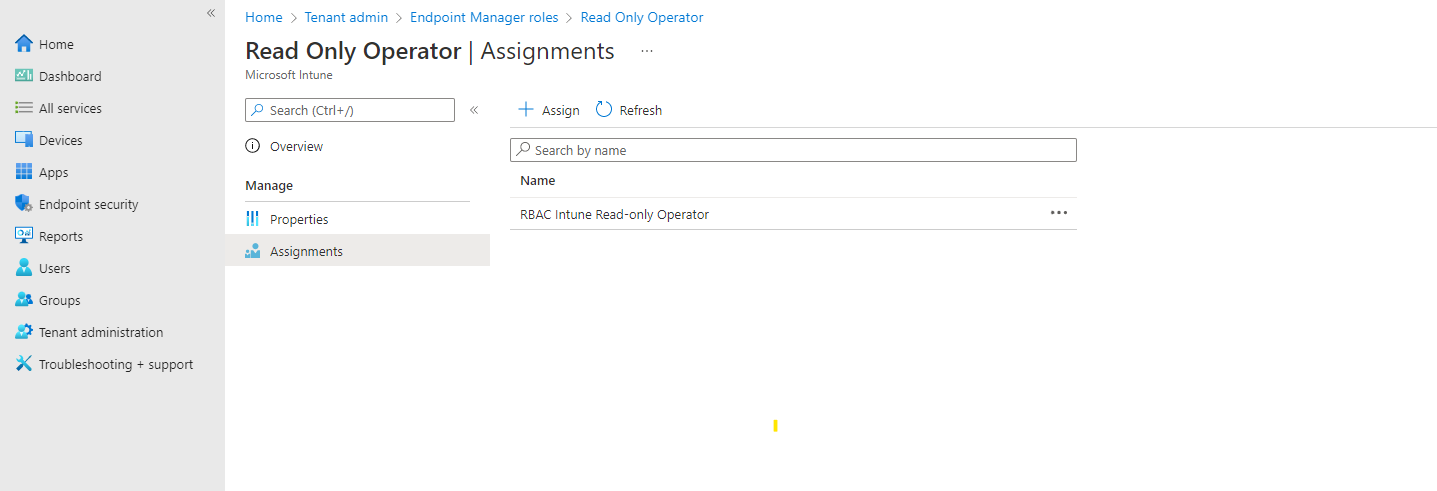
- The RBAC role is created and can only be assigned by a Global administrator or Privileged role administrator
So that’s all, now you are ready to create more RBAC roles and configure RBAC for Intune in a secure way.
Note. It take some time to process the RBAC permissions for an admin. So, be a little patient with testing.

 Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.
Hi! My name is René Laas. I have passion and enthusiasm for the Microsoft 365 Cloud. I am based in the Netherlands.

Hello Rene, that’s a great post and this is what I was looking for. Microsoft says to assign Intune RBAC role to any user he should have Intune license assigned, which means even if he is helpdesk operator or readonly operator then still we need to purchase license for them which increase company cost.
I have one requirement for packaging team, I want all my packaging team members to have access to Intune to Add windows app(win32/Lob etc) and assign app to groups. I got to know “Application Manager” role is more related with this requirement, but I would like to know will this role give them access to create packages on Intune portal ? I havent tested this but would like to know your inputs.
Hi Suraj, an intune license is not required no use the functionality. But from security perspectives you want that your admin use for instance mfa and pim. For some features you need an entra id (azure ad) P2 license but not the intune. You only have to make sure that you have enabled the option that admin without license have access to the portal.
You can check in the roles section and clicking on the built in role what rights they will get with that role. I prefer to use custom roles and give them least privileges. So describe what they have to do in the intune portal and assign those rights to their account.
Kind regards,
Rene